BokBot, also known as IcedID, is a modular banking Trojan that has been active since at least April 2017. The core module provides robust functionality allowing the malware to collect system information, acquire persistence, and establish a communication channel with the adversary’s infrastructure. Furthermore, with its modular functionality BokBot has the ability to increase and evolve its capabilities by receiving additional modules during its execution.
BokBot’s is now commonly delivered using spearphishing but leverages multiple payload delivery vectors such as malicious Office documents, ISO images, and polyglot files with embedded payloads.
In the past, BokBot was primarily distributed via Emotet-related infections, a Malware-as-a-Service (MaaS) developed and operated by the adversary known as Mummy Spider, which AttackIQ has previously emulated. BokBot has not only been observed interacting with Emotet, but also with other malware families, such as Smoke Loader and Gootloader. Its use is shared amongst various ransomware groups such as XingLocker, Quantum, REvil, and Conti.
AttackIQ has released two new attack graphs that emulate BokBot’s behaviors to help customers validate their security controls and their ability to defend against this threat. Validating your security program performance against these behaviors is vital in reducing risk. By using these new attack graphs in the AttackIQ Security Optimization Platform, security teams will be able to:
- Evaluate security control performance against multiple threat actors all who are using BokBot as part of their infection chains.
- Assess their security posture against the many evolutions of one of the most prolific malware families used in cybercrime.
- Continuously validate detection and prevention pipelines against attacks with different endgame objectives.
BokBot – 2022-08 – Polyglot CHM File leads to BokBot and Cobalt Strike Infection
The first attack graph is based on a Unit 42 report detailing an attack that took place in August 2022. Researchers observed the adversary leveraging a Microsoft Compiled HTML Help (CHM) polyglot file. Polyglot files are files that contain several different file format types, causing the file to behave differently depending on which application is used to open the file.
The infection chain started from a phishing email that included a ZIP file attachment containing an ISO image with the CHM file inside. When the polyglot CHM file is executed, an HTML file is used as a decoy window with hidden script code. There is a single-line command to execute the same CHM file again, this time using MSHTA, a Windows-native binary designed to execute Microsoft HTML Application (HTA) files.
The attack graph begins its first stage by downloading and saving the malicious ZIP file used by the adversary. Then it emulates the mounting of the ISO image and subsequent execution of its payload, which in this case is the Microsoft Compiled HTML Help (CHM) polyglot file. MSHTA is then used for the saving and subsequent execution of the DLL associated with BokBot. This stage ends with the creation of a scheduled task in order to obtain persistence.
Ingress Tool Transfer (T1105): This scenario downloads to memory and saves to disk in two separate scenarios to test network and endpoint controls and their ability to prevent the delivery of known malicious content.
Subvert Trust Controls: Mark-of-the-Web Bypass (T1553.005): This scenario bypasses MOTW by downloading and mounting an ISO image on the system to execute the payload contained inside.
System Binary Proxy Execution: Mshta (T1218.010): Mshta.exe is a native Windows utility that threat actors can abuse to download remote payloads that include VBScript code.
System Binary Proxy Execution: Rundll32 (T1218.011): RunDll32 is a native system utility that can be used to execute DLL files and call a specific export inside the file. This scenario executes RunDll32 with an AttackIQ DLL and calls an export to mimic previously reported malicious activity.
Scheduled Task/Job: Scheduled Task (T1053.005): This scenario creates a new scheduled task using the schtasks utility with the name {868268D3-B614-2C87-8ABA-992771D9A3DA} that was observed to be used in these attacks.
The second stage focuses on the discovery and collection of information related to the compromised system. This stage culminates with the identification of remote systems and subsequent execution of AdFind, used to collect information related to the Active Directory of the compromised environment.
System Information Discovery (T1082): The native systeminfo and net config commands are executed to retrieve all of the Windows system information.
- System Network Configuration Discovery (T1016): Native Window’s commands like
route,ipconfig, andnet useare executed to collect details about the infected host and network shares.
System Language Discovery (T1614.001): The adversary uses the chcp command to collect information on the active console code page.
Security Software Discovery (T1518.001): A native Microsoft Windows WMIC (Windows Management Instrumentation Command-line) is executed to retrieve information regarding the installed antivirus product on the local system.
Domain Trust Discovery (T1482): This scenario calls the native nltest utility with the /trusted_domains option to retrieve a list of trusted Active Directory domains associated with this host.
Remote System Discovery (T1018): This scenario executes the net view command to gather additional hosts available to the infected asset.
Account Discovery: Domain Account (T1087.002): The system command net group and the Adfind utility are used to discover details about the victim’s Active Directory configuration including accounts, groups, computers, and subnets.
The final stage of this attack is based on the download and execution of Cobalt Strike which will attempt to collect credentials from memory. The attack graph culminates with the lateral movement to other systems in the environment through the Remote Desktop Protocol (RDP).
OS Credential Dumping: LSASS Memory (T1003.001): LSASS memory is dumped to disk by creating a minidump of the lsass process. This process is used for enforcing security policy on the system and contains many privileged tokens and accounts that are targeted by threat actors.
Remote Desktop Protocol (T1021.001): The adversary leveraged RDP to propagate to several hosts within the network.
BokBot – 2021-05 – Malicious Office Document leads to Lateral Movement and Data Exfiltration
The second attack graph is based on a report released in June 2021 by the DFIR Report involving the delivery of BokBot. The initial BokBot infection is suspected to have occurred via a malicious spam campaign that included a password-protected ZIP archive. Once extracted, the user would find a Word document with a macro that when executed, delivered the initial DLL loader. During this attack, the adversary performed a range of techniques, from host discovery to lateral movement, using Remote Desktop and SMB to access file servers within an enterprise domain.
This attack featured overlap with the techniques observed and the delivery of the same 2nd stage malware. This demonstrates a consistency in the BokBot infection chain over time.
This attack graph begins with the download and saving of the malicious office file used by the adversary, which culminates with the saving of a never-before-seen first-stage loader called GzipLoader, which is executed by means of RegSvr32.
System Binary Proxy Execution: Regsvr32 (T1218.010): RegSvr32 is a native Windows utility that threat actors can use to register Common Object Model (COM) DLLs. This functionality allows an actor to deploy a malicious DLL and have a native Windows tool execute the code as the parent process. This scenario executes RegSvr32 with an AttackIQ binary.
Next, the attack graph will execute the initial host enumeration actions handled by GzipLoader followed by the loader downloading and saving a fake Gzip file, which contains the encrypted BokBot DLL. Finally, the attack graph will try to load the BokBot DLL by using RunDLL32, having RegSvr32 as a fallback and obtaining persistence by using a scheduled task.
System Information Discovery (T1082): Executes a WMI command to learn information about the system’s OS type.
System Owner / User Discovery (T1033): Live off the land by running whoami and users to gain details about the currently available accounts and permission groups.
The final stages of the attack mimic the ones used in the previously described attack graph. The actor deploys Cobalt Strike, dumps credentials, and attempts to move laterally using RDP.
Detection and Mitigation Opportunities
With so many different techniques being used by threat actors, it can be difficult to know which to prioritize for prevention and detection assessment. AttackIQ recommends first focusing on the following techniques emulated in our scenarios before moving on to the remaining techniques.
1. Scheduled Task/Job: Scheduled Task (T1053.005)
Adversaries may abuse the Windows Task Scheduler to perform task scheduling for initial or recurring execution of malicious code. There are multiple ways to access the Task Scheduler in Windows. The schtasks utility can be run directly from the command line, or the Task Scheduler can be opened through the GUI within the Administrator Tools section of the Control Panel.
1a. Detection
With an EDR or SIEM Platform, you can detect the following commands being issued to schedule a malicious task:
Process Name = (“cmd.exe” OR “Powershell.exe”)
Command Line CONTAINS (“schtasks” AND “/CREATE” AND (“cmd” OR “powershell”)
1b. Mitigation
MITRE ATT&CK has the following mitigation recommendations:
- M1047 – Audit
- M1028 – Operating System Configuration
- M1026 – Privileged Account Management
- M1018 – User Account Management
2. System Binary Proxy Execution: Rundll32 (T1218.011)
Adversaries may abuse rundll32.exe to proxy execution of malicious code. Using rundll32.exe instead of executing directly, may avoid triggering security tools that may not monitor execution of the rundll32.exe process because of allow-lists or false positives from normal operations.
2a. Detection
Using a SIEM or EDR product, you can monitor the use of benign tools such as rundll32.exe being used to execute possibly malicious DLLs. A common way to detect this activity is to detect when DLLs are being executed from a globally writable directory, such as C:\Windows\Temp\
Process Name = (“cmd.exe” OR “powershell.exe”)
Command Line CONTAINS (“rundll32” AND “.dll”)
Target File Path CONTAINS (“\temp\” OR “\tmp\”)
2b. Mitigation
MITRE ATT&CK has the following mitigation recommendations:
3. System Binary Proxy Execution: Mshta (T1218.010)
MSHTA is a native Windows tool that can either be used to open .hta files directly or be passed a URL in the command line arguments to download and execute a remote file. This tactic is very commonly used as part of a phishing attack where either the Mshta.exe process is executed as part of Office macros or a Shortcut .lnk file.
3a. Detection
The following pseudo-signature can help detect abuse of the MSHTA process.
Process Name == mshta.exe
Command Line CONTAINS (“http” OR “vbscript” OR “jscript”)
Process Name == Mshta.exe
Parent Process Name CONTAINS (“word” OR “excel” OR “powerpoint”)
3b. Mitigation
MITRE ATT&CK has the following mitigation recommendations for <Technique>
Wrap-up
In summary, this attack graph will evaluate security and incident response processes and support the improvement of your security control posture against another shared cybercrime malware. With data generated from continuous testing and use of these attack graphs, you can focus your teams on achieving key security outcomes, adjust your security controls, and work to elevate your total security program effectiveness against a known and dangerous threat.
AttackIQ stands at the ready to help security teams implement this attack graph and other aspects of the AttackIQ Security Optimization Platform, including through our co-managed security service, AttackIQ Vanguard.
 (Click for Larger)
(Click for Larger)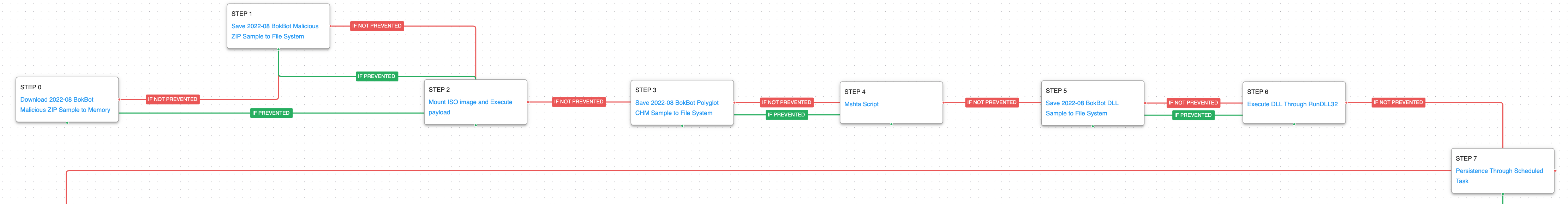 (Click for Larger)
(Click for Larger) (Click for Larger)
(Click for Larger)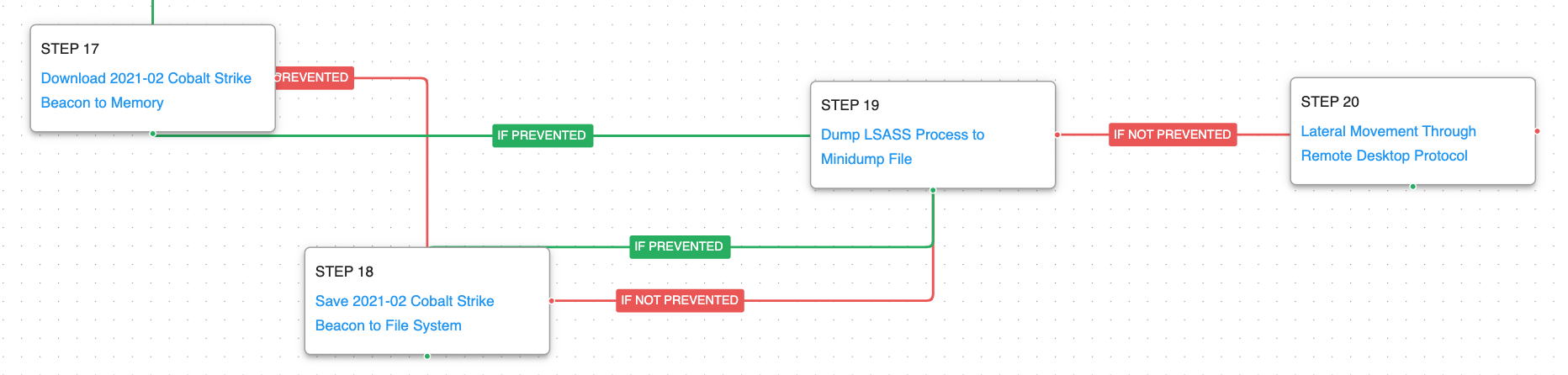 (Click for Larger)
(Click for Larger)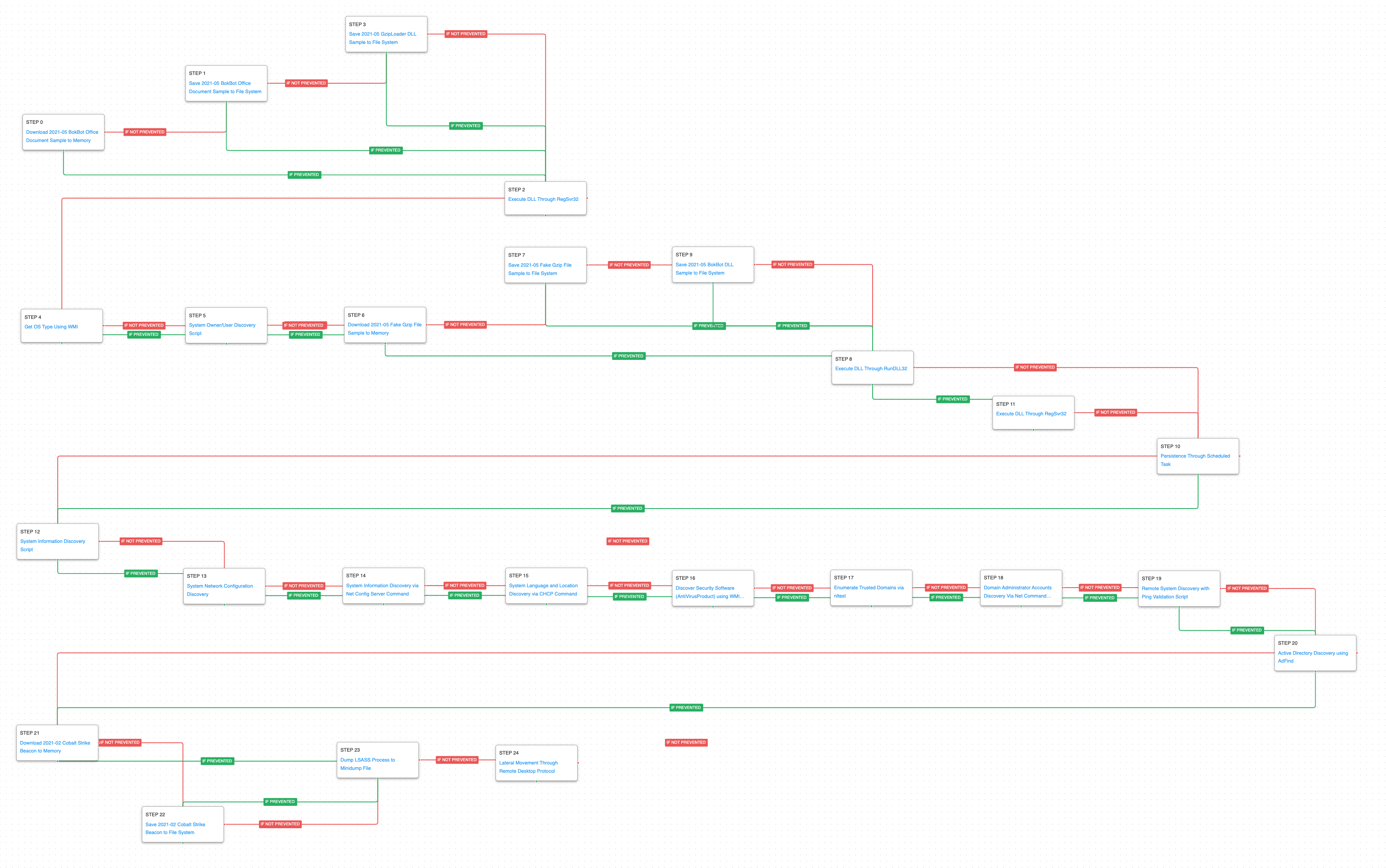 (Click for Larger)
(Click for Larger)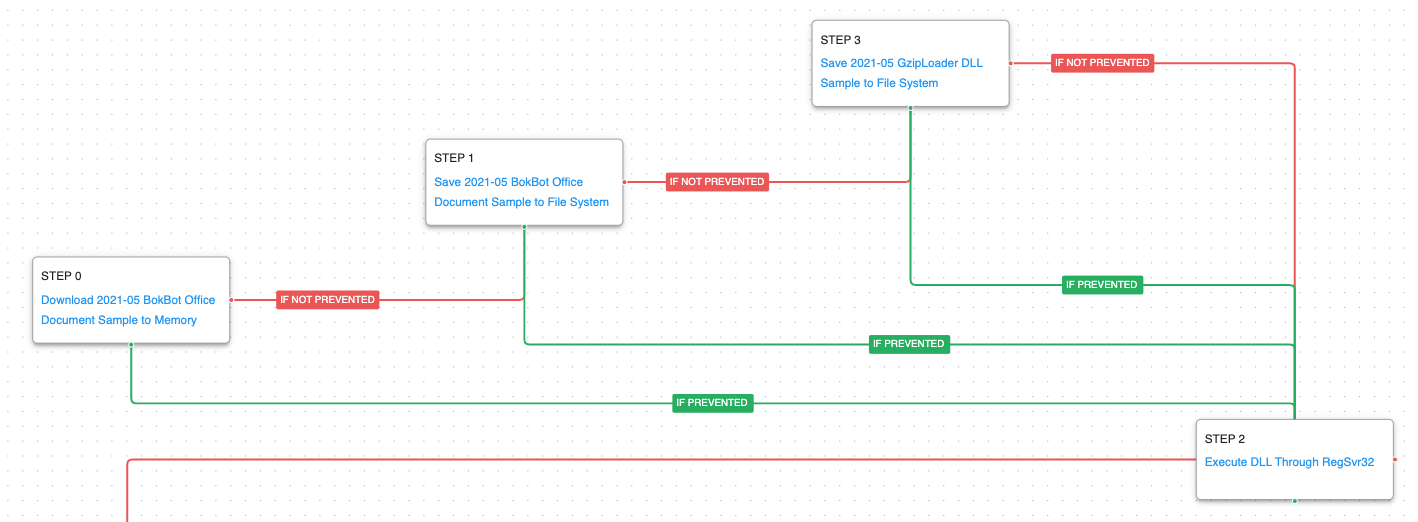 (Click for Larger)
(Click for Larger)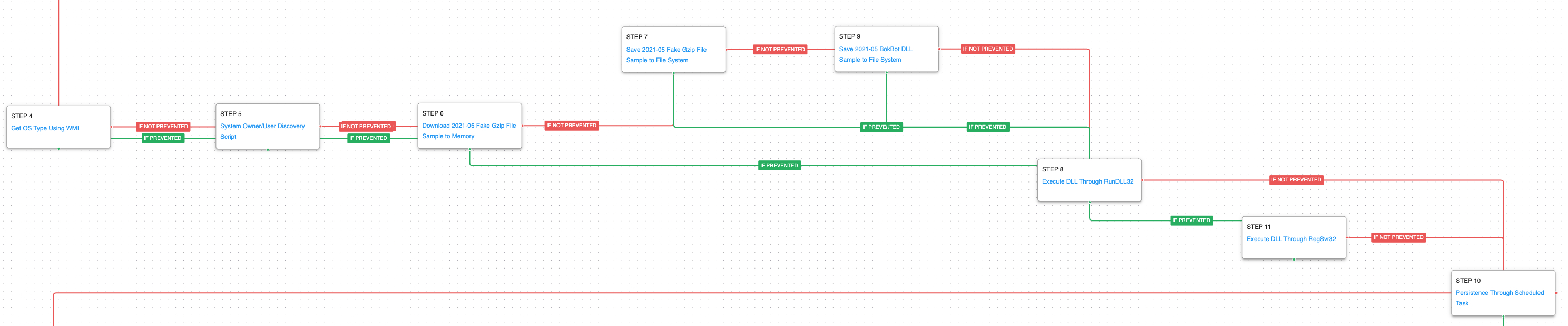 (Click for Larger)
(Click for Larger)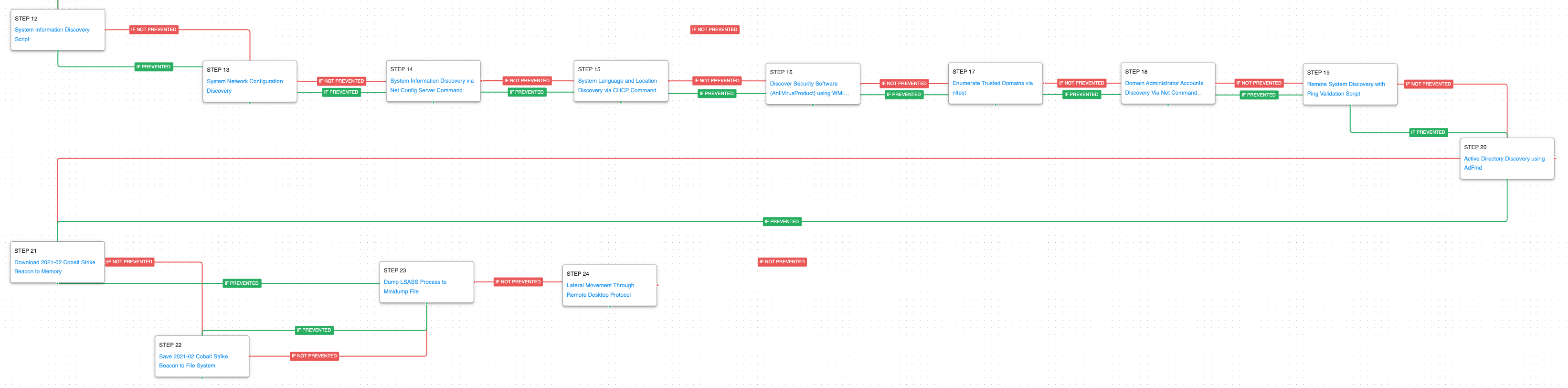 (Click for Larger)
(Click for Larger)
