On May 16, 2023, the Federal Bureau of Investigation (FBI), the Cybersecurity and Infrastructure Security Agency (CISA) and the Australian Cyber Security Centre (ACSC) released a joint Cybersecurity Advisory (CSA) disseminating known BianLian ransomware and data extortion group techniques and. This joint CSA is a continuation of CISA’s ongoing #StopRansomware effort to arm defenders with the intelligence they need to combat different ransomware variants and ransomware threat actors.
BianLian is a ransomware developer, deployer, and data extortion cybercriminal group that has targeted organizations in multiple U.S. critical infrastructure sectors since June 2022. They have also targeted Australia’s critical infrastructure sectors in addition to professional services and property development organizations. BianLian group originally employed a double-extortion model in which they encrypted victims’ systems after exfiltrating the data, however, around January 2023, they shifted to primarily data theft extortion.
AttackIQ has released a new attack graph that emulates the capabilities of the BianLian cybercriminal group to help customers validate their security controls and their ability to defend against this determined adversary.
Validating your security program performance against these behaviors is vital to reducing risk. By using this new attack graph in the AttackIQ Security Optimization Platform, security teams will be able to:
- Evaluate security control performance against a ransomware actor who continues to evolve and adapt.
- Assess their security posture against an attack with dual goals, exfiltrating and encrypting data.
- Continuously validate detection and prevention pipelines against an actor playbook similar to many of today’s current ransomware groups.

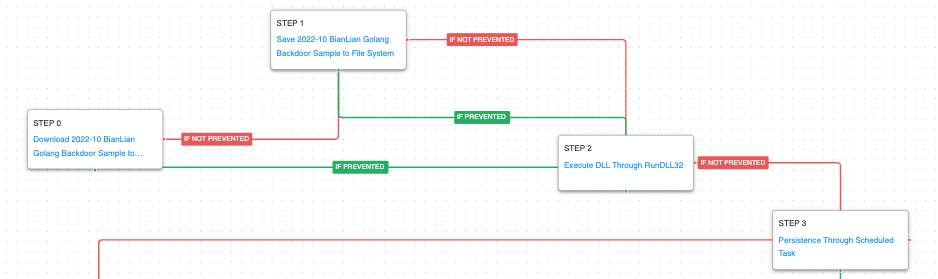
This attack graph emulates a full kill chain attack from the BianLian adversary, that both exfiltrates data and attempts to encrypt sensitive files. This activity leverages a custom backdoor, tailored to each victim and a bespoke encryptor used to encrypt all files, which are accompanied by a ransom note placed in each affected directory.
The attack graph starts by downloading the custom backdoor and executing it using Window’s native RunDll32 utility. Persistence is established by creating a Scheduled Task using a name attempting to blend in with legitimate tasks.
Ingress Tool Transfer (T1105): This scenario downloads to memory and saves to disk known malicious files in two independent scenarios, testing both network and endpoint controls.
System Binary Proxy Execution: Rundll32 (T1218.011): RunDll32 is a native system utility that can be used to execute DLL files and call a specific export inside the file. This scenario executes RunDll32 with an AttackIQ DLL and calls an export to mimic previously reported malicious activity.
Scheduled Task/Job: Scheduled Task (T1053.005): This scenario creates a new scheduled task using the schtasks utility with the name NetSh Helper that was observed to be used in these attacks.
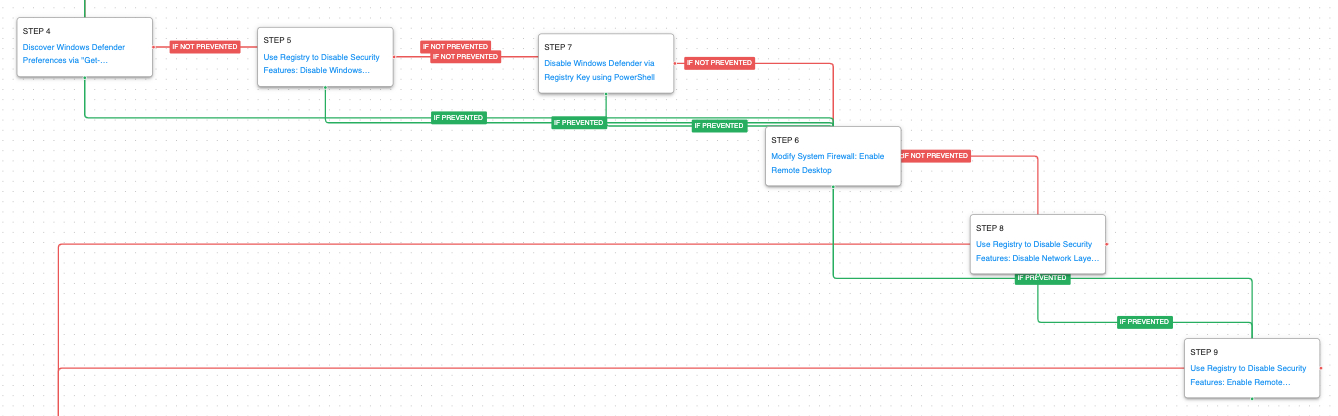
Next, the attack graph will carry out defense evasion tasks, such as disabling security tools and modifying system firewall policies. The end goal of this stage is to then attempt to enable some remote graphical access to the system by either allowing Remote Desktop or Remote Assistance.
Security Software Discovery (T1518.001): The PowerShell cmdlet Get-MpPreference is executed to retrieve Windows Defender preferences.
Impair Defenses: Disable or Modify Tools (T1562.001): Multiple registry keys are modified to disable multiple Windows Defender features, such as Realtime Monitoring.
Impair Defenses: Disable or Modify System Firewall (T1562.004): Remote Desktop may not be enabled by default through the local system firewall. The threat actors can create new firewall rules to open up ports for local and remote access using the netsh advfirewall utility. This scenario opens local port 3389 for inbound access.
Modify Registry (T1112): Disables the Network Layer Authentication (NLA) for Remote Desktop connections and enables Remote Assistance to allow external users to request control of the system.
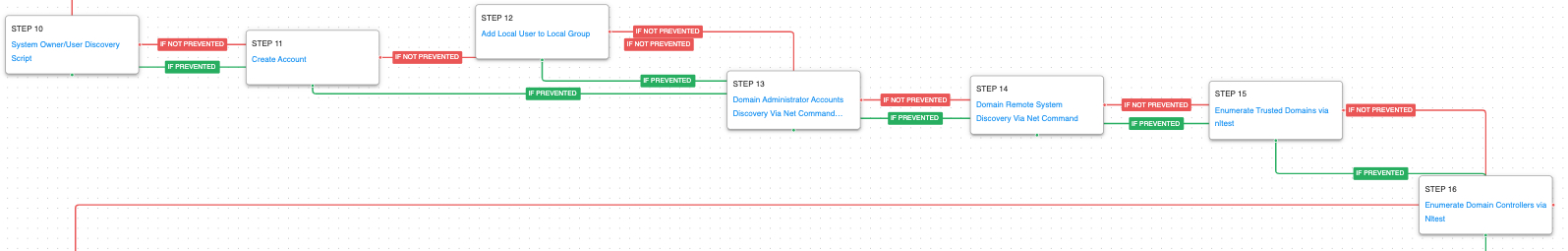
The emulation then enters a discovery phase. Identifying information about the infected system, its Active Directory domain environment, and its network capabilities. It will also look for information about connected drives and the search for files and directories on the infected system.
System Owner/User Discovery (T1033): query user and whoami are called to determine what account is the webshell currently operating under.
Create Account: Local Account (T1136.001): In this example of the attacks, the actors needed to create a new account instead of blending in as an existing local account. An account with the name LocalAdministrator is created using net user.
Account Manipulation (T1098): The newly created local admin account is added to the Remote Desktop Users group which allows the account to access the computer remotely.
Account Discovery: Domain Account (T1087.002): The system command net group is used to list Domain and Enterprise Admins accounts.
Remote System Discovery (T1018): This scenario executes the net group command to gather additional hosts available to the infected asset.
Domain Trust Discovery (T1482): This scenario calls the native nltest utility with the /trusted_domains or /dclist option to retrieve a list of trusted Active Directory domains and Domain Controllers associated with this host.
Network Service Discovery (T1046): This scenario uses nmap for scanning hosts that are open on ports 139, 389, 445, 636, 3389 that would identify remote Windows accessible hosts to the attacker.
Network Share Discovery (T1135): The PowerShell cmdlet Get-SmbShare is used to retrieve the Server Message Block (SMB) shares of the compromised host.
File and Directory Discovery (T1083): The actors used the dir command to recursively query a drive and list all of the files.
Peripheral Device Discovery (T1120): This scenario retrieves information about the system’s logical drives through the execution of the DeviceIoControl (Kernel32) Windows API call.
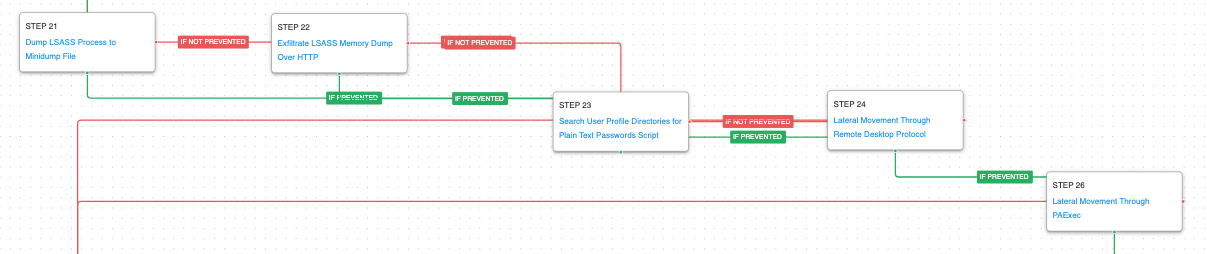
To facilitate lateral movement, the attack graph will dump and exfiltrate LSASS memory and search files for plain text credentials. Attempts to move laterally to other systems will be completed by using RDP or PAExec.
OS Credential Dumping: LSASS Memory (T1003.001): LSASS memory is dumped to disk by creating a minidump of the lsass process. This process is used for enforcing security policy on the system and contains many privileged tokens and accounts that are targeted by threat actors.
Exfiltration Over C2 Channel (T1041): This scenario exfiltrates via HTTP POST requests a file named lsass.dmp which contains the LSASS process memory dump.
Unsecured Credentials: Credentials in Files (T1552): This scenario runs the command findstr against local files looking for passwords that may be stored in plain text.
Remote Services: Remote Desktop Protocol (T1021.001): Attempt to use Remote Desktop to move laterally to additional hosts and identify additional data for exfiltration and extortion.
Remote Services: SMB/Windows Admin Shares (T1021.002): The open-source utility PaExec is used to emulate create remote process on Windows systems by abusing open ADMIN$ shares.
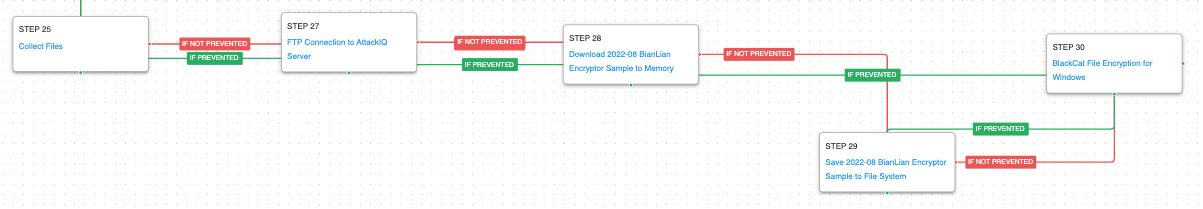
Finally, the emulation will collect files of interest and exfiltrate them through the File Transfer Protocol (FTP). Once the exfiltration is complete, the BianLian encryptor will be downloaded and saved on the system, which will be used to encrypt the files on the system.
Automated Collection (T1119): This scenario performs the automated collection of files with certain extensions for later exfiltration.
Exfiltration Over Asymmetric Encrypted Non-C2 Protocol (T1048.002): This scenario simulates the ability to exfiltrate collected information via File Transfer Protocol (FTP) by performing a connection to a remote AttackIQ server.
Data Encrypted for Impact (T1486): This scenario performs the file encryption routines used by common ransomware families. Files matching an extension list are identified and encrypted in place using the same encryption algorithms observed in another Rust-based ransomware family.
Detection and Mitigation Opportunities
With so many different techniques being used by threat actors, it can be difficult to know which to prioritize for prevention and detection assessment. AttackIQ recommends first focusing on the following techniques emulated in our scenarios before moving on to the remaining techniques.
1. Data Encrypted for Impact (T1486)
It should go without saying that as a last resort, preventing your systems and files from being encrypted should be your number one focus. Ensuring that you have the layered endpoint defenses including Antivirus and EDR solutions is critical.
1a. Detection
Ransomware attacks are best prevented and alerted by your EDR/AV Policies. Typically, a configuration for ransomware protection is presented and we strongly encourage that it is enabled in your security controls.
There are three telling signs of ransomware activity in an environment that you could query for and possibly make preventative detections if your security controls allow. Those three are deletion of shadow volumes, suspicious amounts of exfiltrated data, and of course, wide set file encryption.
Detecting deletion of shadow volumes is usually the first step that occurs and can be detected by looking at command line activity:
Via vssadmin.exe:
Process Name == (cmd.exe OR powershell.exe)
Command Line CONTAINS (“vssadmin” AND “Delete Shadows”)
Via PowerShell:
Process Name == powershell.exe
Command Line == “Get-WmiObject Win32_Shadowcopy | ForEach-Object ($_.Delete();)”
Detecting suspicious Data Exfiltration:
Detecting exfiltration is well suited for IDS/IPS and DLP solutions. These products should be configured to identify sensitive files. If sensitive files, or a large amount of web traffic is sent to a rare external IP, it should be detected or prevented depending on security policies for the security control. Historical NetFlow data logging can also bubble up hosts that are experience uncommon peaks in outgoing traffic.
Detecting Ransomware-like File Encryption:
Utilizing an EDR or SIEM/SOAR product can help detect and prevent suspicious file encryption related to ransomware attacks. Utilizing these tools to look for excessive file modifications (greater than 1000 on a system) within less than a minute of time is a good starting indicator. To increase the fidelity a bit, you could include file modification file extension to popular ransomware extensions such as .conti, .Locky, .Ryuk, etc. If possible, with a SOAR or preventative EDR platform, we recommend setting these detections to kill all processes involved in creating the alert as it will most likely stop the spread of the Ransomware.
1b. Mitigation
MITRE ATT&CK Recommends the following mitigations:
2. Scheduled Task/Job: Scheduled Task (T1053.005)
Adversaries may abuse the Windows Task Scheduler to perform task scheduling for initial or recurring execution of malicious code. There are multiple ways to access the Task Scheduler in Windows. The schtasks utility can be run directly from the command line, or the Task Scheduler can be opened through the GUI within the Administrator Tools section of the Control Panel.
2a. Detection
With an EDR or SIEM Platform, you can detect the following commands being issued to schedule a malicious task:
Process Name = (“cmd.exe” OR “Powershell.exe”)
Command Line CONTAINS (“schtasks” AND “/CREATE” AND (“cmd” OR “powershell”)
2b. Mitigation
MITRE ATT&CK has the following mitigation recommendations:
- M1047 – Audit
- M1028 – Operating System Configuration
- M1026 – Privileged Account Management
- M1018 – User Account Management
3. Command and Scripting Interpreter: PowerShell (T1059.001)
This actor heavily utilizes PowerShell scripts and built-in PowerShell cmdlets to complete their discovery objectives and interact with Active Directory.
3a. Detection
Enabling PowerShell script logging is critical to being able to track how PowerShell is being used in your environment. Many actors will obfuscate their code to make it more difficult to detect.
Resources for Enabling PowerShell Logging:
- https://logrhythm.com/blog/powershell-command-line-logging/
- https://www.mandiant.com/resources/blog/greater-visibility
- https://www.splunk.com/en_us/blog/security/hunting-for-malicious-powershell-using-script-block-logging.html
3b. Mitigation
MITRE ATT&CK has the following mitigation recommendations:
- M1049 – Antivirus/Antimalware
- M1045 – Code Signing
- M1042 – Disable or Remove Feature or Program
- M1038 – Execution Prevention
- M1026 – Privileged Account Management
Wrap-up
In summary, this attack graph will evaluate security and incident response processes and support the improvement of your security control posture against an active ransomware threat. With data generated from continuous testing and use of these attack graphs, you can focus your teams on achieving key security outcomes, adjust your security controls, and work to elevate your total security program effectiveness against a known and dangerous threat.
AttackIQ stands at the ready to help security teams implement this attack graph and other aspects of the AttackIQ Security Optimization Platform, including through our fully managed service, AttackIQ Ready!, and our co-managed security service, AttackIQ Vanguard.