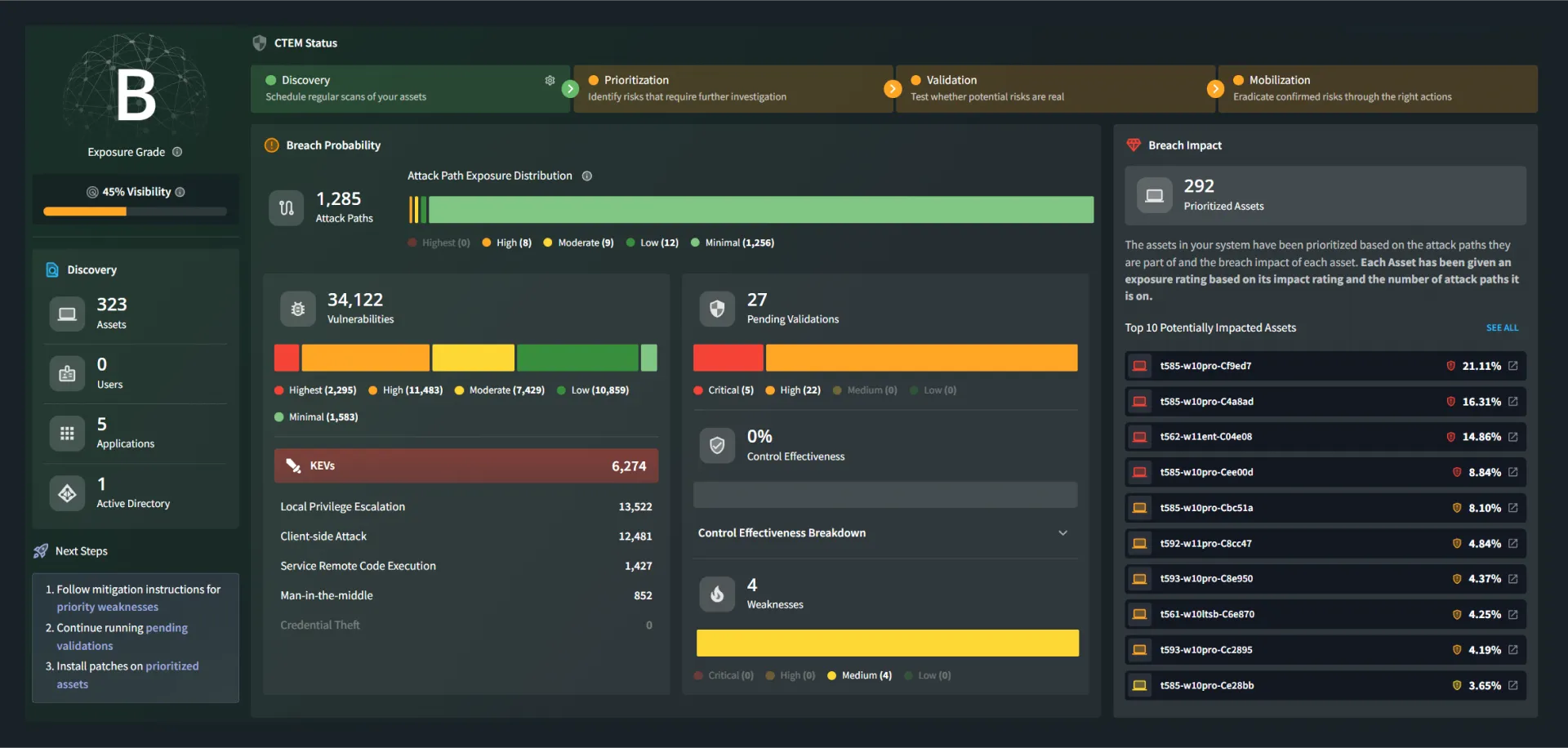
How Do You Manage Exposure?
You can’t manage what you can’t measure.
Validate everything.
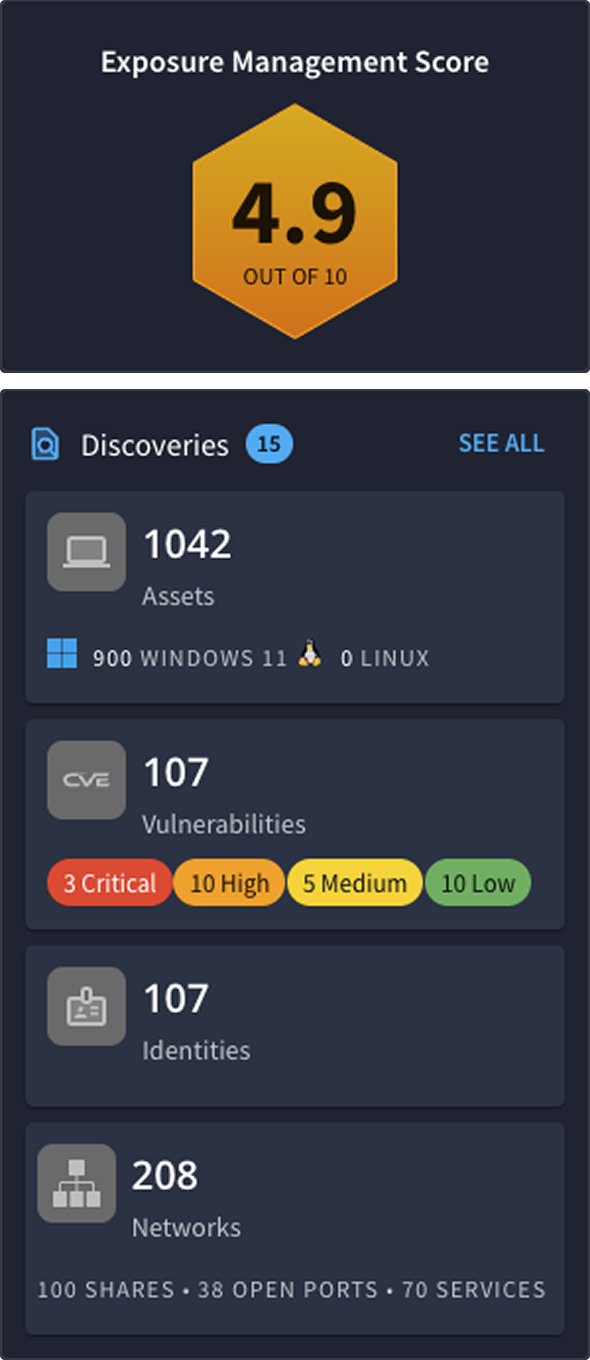
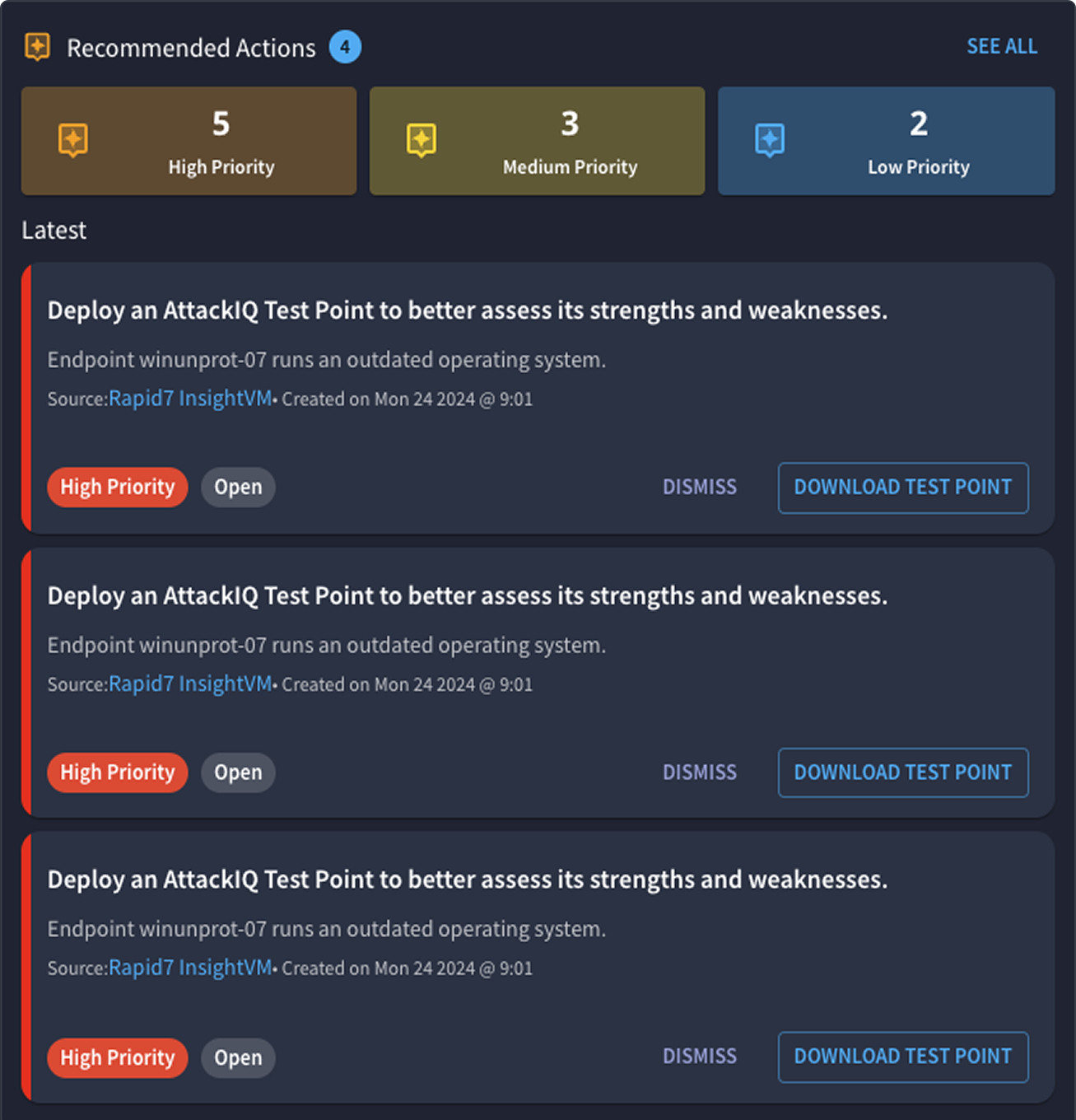

AEV: The Next Evolution of BAS
Validate Continuously
Catch failures fast with always-on, automated testing that eliminates point-in-time blind spots.
Validate Everything
Verify threats, controls, and attack paths across cloud, identity, and infrastructure—in one unified platform.
Validate Everywhere
Evaluate defenses across endpoints, hybrid environments, and third parties at scale and without disruption.
Validate What Matters
Prioritize exploitable exposures that impact your business and prove which defenses actually work.
Introducing The AttackIQ Adversarial Exposure Validation (AEV) Platform
The AttackIQ AEV platform goes beyond traditional exposure management by continuously validating security controls and simulating real-world scenarios.
Exposure by Terrain
Map your exposure across operational environments—not just control frameworks. AttackIQ provides granular visibility across On-Premises, Cloud, Hybrid, and Remote Workforce environments to pinpoint your highest-risk terrain. Go beyond aggregate scores to see exactly where vulnerabilities concentrate and focus security investments where they’ll have the greatest impact.
Learn MoreCyber Threat Intelligence
Transform static threat feeds into actionable insights. AttackIQ integrates with leading CTI providers to correlate real-world adversary behaviors with your environment, enabling targeted validation, faster response, and improved readiness against the threats most likely to impact your organization.
Vulnerability Data
Centralize and operationalize vulnerability insights from across your ecosystem. AttackIQ ingests data from leading vulnerability management platforms to correlate known weaknesses with adversary behaviors, enabling contextual validation and smarter prioritization based on real-world exploitability.
SIEM+
Validate your entire detection pipeline with seamless AttackIQ integration. Ensure adversary techniques trigger the right alerts, populate key fields, and support effective threat hunting, delivering end-to-end visibility from simulation to analysis.
Learn MoreEDR
Prove your endpoint defenses work as intended. AttackIQ integrates with leading EDR platforms to safely test prevention, detection, and response against real attacker TTPs without disrupting users or production systems.
Learn MoreNGFW
Put your firewall rules and segmentation policies to the test. AttackIQ emulates adversary behaviors like lateral movement, command-and-control, and exfiltration to continuously validate NGFW configurations and uncover policy gaps before attackers do.
Learn MoreCloud
Test your cloud defenses across major cloud environments without deploying agents or installations. Validate identity controls, workload protections, and misconfiguration detection against cloud-native threats and realistic attack paths.
Learn MoreCustomer Controls
Offering APIs such as:
Security Control Validation
Active Threat Monitoring
Attack Path Management
Attack Surface Management
Vulnerability Prioritization
Risk Scoring
Security Control Validation
Continuously validate whether your existing security controls—EDR, firewalls, email security, etc.—block or detect real adversary behaviors, ensuring that investments truly work as intended.
Learn MoreActive Threat Monitoring
Monitor emerging threats in real time. As new TTPs arise, emulate them to see if your security stack can prevent, detect, or log the suspicious activity.
Learn MoreAttack Path Management
Dynamically discover and visualize how attackers could chain vulnerabilities and misconfigurations to move laterally. Identify choke points in those attack paths to remediate the biggest risks first.
Learn MoreAttack Surface Management
Identify both agented and agentless assets, including cloud workloads, on-prem endpoints, and shadow IT, so you can see coverage gaps and target them with real adversary tests.
Learn MoreVulnerability Prioritization
Prioritize vulnerabilities based on actual adversary exploitability—rather than raw CVSS scores—so you know which issues matter most for preventing an active breach scenario.
Learn MoreRisk Scoring
Get an aggregate score of your organization’s resilience, factoring in vulnerabilities, control coverage, and actual test outcomes. Track it over time to show how your exposure level is trending.
Learn MoreScale Offensive Testing
Scale Offensive Testing with AttackIQ’s automated adversary emulations and comprehensive scenario library. Red teams can multiply their impact across thousands of endpoints, continuously exercising real-world threats to test prevention and detection controls at scale—all mapped to MITRE ATT&CK.
Learn MoreManage Exposure
Reduce Exposure by going beyond simple vulnerability scanning. AttackIQ’s approach merges vulnerability data, threat intelligence, and adversary emulation to pinpoint which exposures are most critical to fix first—so you close real attack paths before adversaries exploit them.
Learn MoreOptimize Defensive Posture
Optimize Defensive Posture by aligning your people, processes, and technologies around demonstrable security outcomes. Use AttackIQ’s recommended mitigations to strengthen detection logic, ensure security tools are configured properly, and reduce mean time to remediation.
Learn MoreEnhance Detection Engineering
Transform detection engineering from reactive rule adjustments to proactive validation. AttackIQ empowers detection teams to continuously test their logic against real adversary techniques across SIEM, EDR, and XDR environments. Deploy production-safe simulations to verify detection triggers, optimize MITRE ATT&CK coverage gaps, and eliminate false positives before real threats exploit blind spots.
Learn MoreCommand Center
Command Center is your unified control plane for orchestrating, managing, and measuring all your testing efforts and exposure insights. It is the hub through which AttackIQ brings together threat intelligence, vulnerability data, and security control validation information.
Learn MoreFlex
AttackIQ’s agentless, on-demand testing platform. Ideal for environments where you need a quick, lightweight way to assess controls.
Learn MoreReady
Optimize Defensive Posture by aligning your people, processes, and technologies around demonstrable security outcomes. Use AttackIQ’s recommended mitigations to strengthen detection logic, ensure security tools are configured properly, and reduce mean time to remediation.Ready! offers streamlined, prescriptive validation for teams that want to unlock the power of AttackIQ and don’t need advanced capabilities – making it easier to validate your controls and quickly show measurable security improvements.
Learn MoreEnterprise
Enterprise is our flagship adversary emulation solution, giving security teams full control over automated, continuous testing across diverse environments. It uses our persistent agent model and integrates deeply with your existing security stack to deliver robust validation of prevention and detection controls at scale.
Learn MoreAdversary Exposure Validation (Aligned with MITRE ATT&CK)
Adversary Exposure Validation goes beyond standard Breach & Attack Simulation (BAS). It merges threat intelligence, vulnerability data, attack surface management and continuous testing to give you real-time clarity on which critical adversary behaviors would bypass controls and succeed in your environment—and how to fix the issues before attackers can exploit them.
Learn MoreAVA (AI)
AVA is AttackIQ’s AI-based assistant that helps you create and tailor adversary scenarios, interpret threat intelligence data, and provide automated recommendations on what to test next. AVA also speeds up remediation by suggesting precise detection-rule validations and mitigations.
Proactively Manage Threat Exposure with CTEM + AEV
AEV puts CTEM into action—helping you uncover control failures, reduce exposure, and close security gaps before attackers can exploit them. The result is stronger defenses, lower risk, and improved operational performance.
Align Security With Business Priorities
Smarter Security, Proven Results
Gain unparalleled visibility, efficiency, and control for unmatched protection, cost savings, and peace of mind.
Be Ready for Every Threat,
Every Time
Achieve continuous resilience through a proactive, threat-informed defense.
Optimize Defensive Posture
Reduce
Exposure
featured Resource
10 Strategic Priorities for Security Leaders in 2026
AI acceleration and industrialized cybercrime are changing the threat landscape. Learn what security leaders must operationalize now to build resilience in 2026.
Read the Guide
Real Impact for Real-World
Security Challenges
From Fortune 500 companies to mid-sized enterprises, organizations across industries trust us to keep them resilient.
Never Settle for Uncertainty
Validate Your Defenses
Take the guesswork out of threat exposure management. Validate your defenses with real-world attack scenarios and focus on what matters most—managing your risk.