TA551, also known as Shathak is a sophisticated cybercrime actor targeting victims on a global scale since 2018. The actors are initial access brokers, compromising targets with a variety of shared cybercrime malware families and selling that access to other threat groups. TA551 has leveraged different malware families over time such as Ursnif, IcedID, Valak, Qbot, and Zloader. have been consistently using password-protected ZIP archives containing macro-enabled Office documents as their delivery mechanism. .
The threat actor does not exclusively target any sector and region. They have been observed sending t phishing emails targeting English, German, Italian and Japanese speakers. The majority of their victms have been based in the U.S. and the UK. The access to victim organizations has been sold to ransomware operators like Maze and Egregor.
According to Red Canary, TA551 was the most prevalent threat actor the vendor encountered in 2020. IcedID and Valak were the predominant payloads observed targeting organizations across multiple industries and company This threat actor occupies the first position on the Red Canary 2022 Threat Detection Report.
AttackIQ has released a new fully featured attack graph that emulates the tactics, techniques, and procedures (TTPs) associated with the TA551 intrusion chain that happened in 2020 to help customers validate their security posture against the usual infection chain from this threat actor.
Unlike other attack graphs offered on our platform, this particular attack graph places a specific focus on testing the initial access steps.
Validating your security program performance against these behaviors is vital in reducing risk. By using this new attack graph in the AttackIQ Security Optimization Platform, security teams will be able to:
- Evaluate security control performance against the TA551 intrusion chain.
- Evaluate your email security control performance against the TA551 malspam.
- Assess their security posture against an ever-persistent threat actor that has survived years of competition and take-down attempts.
- Continuously validate detection and prevention pipelines against a threat actor strain that will continue to evolve and impact victims across the globe.
TA551 – 2020 – Intrusion Chain
This attack graph is designed to demonstrate the intrusion chain of TA551, which has been identified as the leading threat of 2022 according to Red Canary’s rankings.
Unlike other attack graphs offered on our platform, this particular graph places a specific focus on testing the initial access steps.
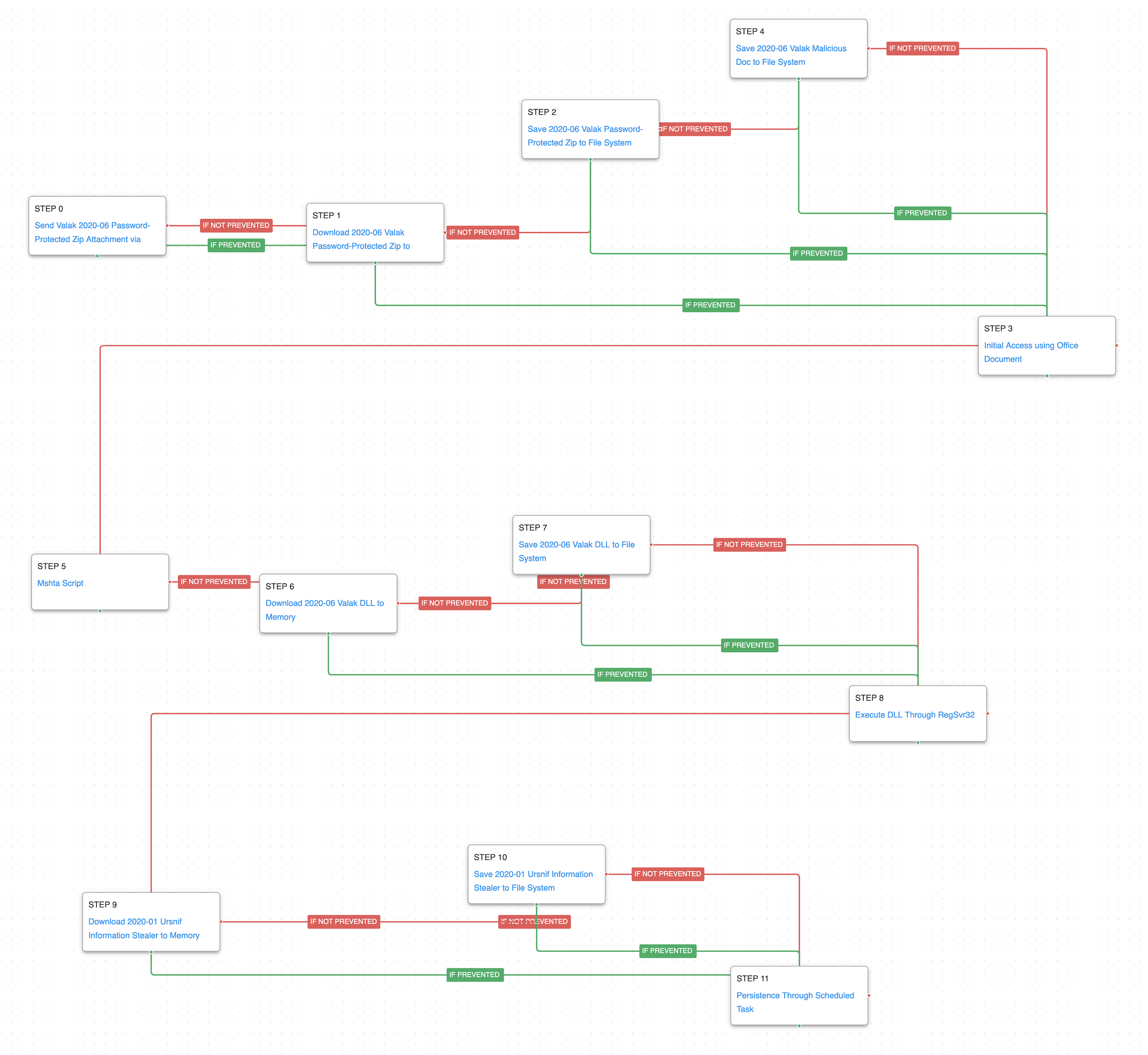
The attack graph will begin with a Test Ingress Email Filter scenario model that will send an email with a Valak password-protected zip file and a body to replicate how the threat actor initiates its campaigns.
After the email reaches the inbox, the user downloads and saves the zip file into the disk. Our graph mimics this behavior by downloading and saving the sample.
Once the user has access to the zip file it will decompress it, triggering a save for the Valak malicious document into the disk.
The scenario Initial Access using Office will emulate the user being tricked to open the document and activate the macros.
A Phishing: Spearphishing Attachment (T1566.001): These scenarios will mimic the reception of an email that contains a Valak Password-Protected zip file as an attachment, its download, and macro enabling. The first scenario will require configuration, such as the email recipient account information.
The macro will execute mshta.exe or certutil.exe to download a valak DLL. Our attack graph will emulate this behavior by running the mshta script scenario followed by the download and save of the valak DLL.
After that, the DLL would be executed using rundll32 or regsvr32. Our attack graph mimics this behavior by executing a DLL using regsvr32.
System Binary Proxy Execution: Mshta (T1218.005): This scenario will use the Windows-native binary mshta.exe to proxy execute an AttackIQ binary.
System Binary Proxy Execution: Mshta (T1218.005): This scenario will use the Windows-native binary mshta.exe to proxy execute an AttackIQ binary.
Ingress Tool Transfer (T1105): These scenarios download to memory and then save to disk in two separate steps to test network and endpoint controls and their ability to prevent the delivery of known malicious files. These scenarios are used for each stage of the malware delivered in these attacks.
System Binary Proxy Execution: Regsvr32 (T1218.010): RegSvr32 is a native Windows utility that threat actors can use to register Common Object Model (COM) DLLs. This functionality allows an actor to deploy a malicious DLL and have a native Windows tool execute the code as the parent process. This scenario executes RegSvr32 with an AttackIQ binary.
The graph will conclude by downloading and saving a Ursniff sample and replicating the way this Information Stealer adds persistence.
Ingress Tool Transfer (T1105): These scenarios download to memory and then save to disk in two separate steps to test network and endpoint controls and their ability to prevent the delivery of known malicious files. These scenarios are used for each stage of the malware delivered in these attacks.
Scheduled Task/Job: Scheduled Task (T1053.005): This scenario will schedule a task using the schtasks Windows utility and verify if the task is successfully executed. The task will be named as Ursniff name its tasks: {54323DEF-300C-4F37-9617-2D01AF8F4CF7}.
Detection and Mitigation Opportunities
With so many different techniques being used by threat actors, it can be difficult to know which to prioritize for prevention and detection assessment. AttackIQ recommends first focusing on the following techniques emulated in our scenarios before moving on to the remaining techniques.
1. System Binary Proxy Execution: Mshta (T1218.005):
TA551 has abused mshta.exe to download and proxy execution of malicious files through a trusted Windows utility.
1a. Detection
Using a SIEM or EDR Platform to see monitor mshta.exe execution will alert when unauthorized users or software attempt to abuse this tool.
Process Name == mshta.exe
Command Line CONTAINS (‘Wscript.Shell)
1b. Mitigation
MITRE ATT&CK has the following mitigation recommendations for System Binary Proxy Execution: Mshta
2. System Binary Proxy Execution: Regsvr32 (T1218.010):
TA551 has used Regsvr32.exe to proxy execute a malicious DLL.
2a. Detection
While this native tool is commonly used by legitimate applications there are behaviors related to their execution that can stand out in your process logs. Searching for files that are being executed from temporary directories, that don’t have the standard .dll file extension, or call strange-looking export names can stand out from regular user behavior.
Process Name == regsvr32.exe
Command Line CONTAINS (‘TEMP’ OR ‘.png’ OR ‘Roaming’)
2b. Mitigation
MITRE ATT&CK has the following mitigation recommendations for <Technique>
3. Scheduled Task/Job: Scheduled Task (\):
Ursniff leverages the use of scheduled tasks to ensure persistence in the target system.
3a. Detection
Using a SIEM or EDR Platform to see monitor schtasks.exe execution will alert when unauthorized users or software attempt to abuse this tool.
Process Name == schtasks.exe
Command Line CONTAINS (‘Create’)
3b. Mitigation
MITRE ATT&CK has the following mitigation recommendations for <Technique>
- M1047 – Audit
- M1028 – Operating System Configuration
- M1026 – Privileged Account Management
- M1018 – User Account Management
Wrap-up
In summary, this attack graph will evaluate security and incident response processes and support the improvement of your security control posture against the TA551 intrusion chain. With data generated from continuous testing and the use of this attack graph, you can focus your teams on achieving key security outcomes, adjust your security controls, and work to elevate your total security program effectiveness against a known and dangerous threat.
AttackIQ stands at the ready to help security teams implement this attack graph and other aspects of the AttackIQ Security Optimization Platform, including through our co-managed security service, AttackIQ Vanguard.
 Click for Larger
Click for Larger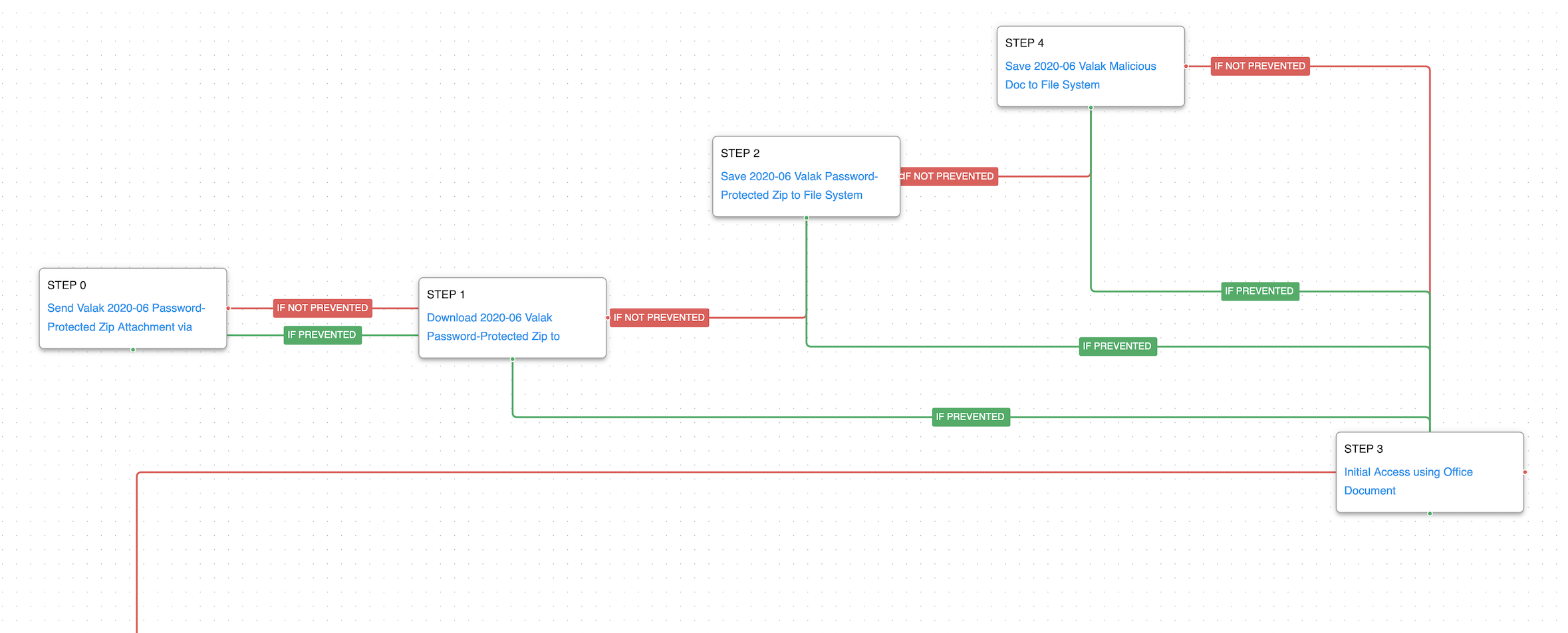 Click for Larger
Click for Larger Click for Larger
Click for Larger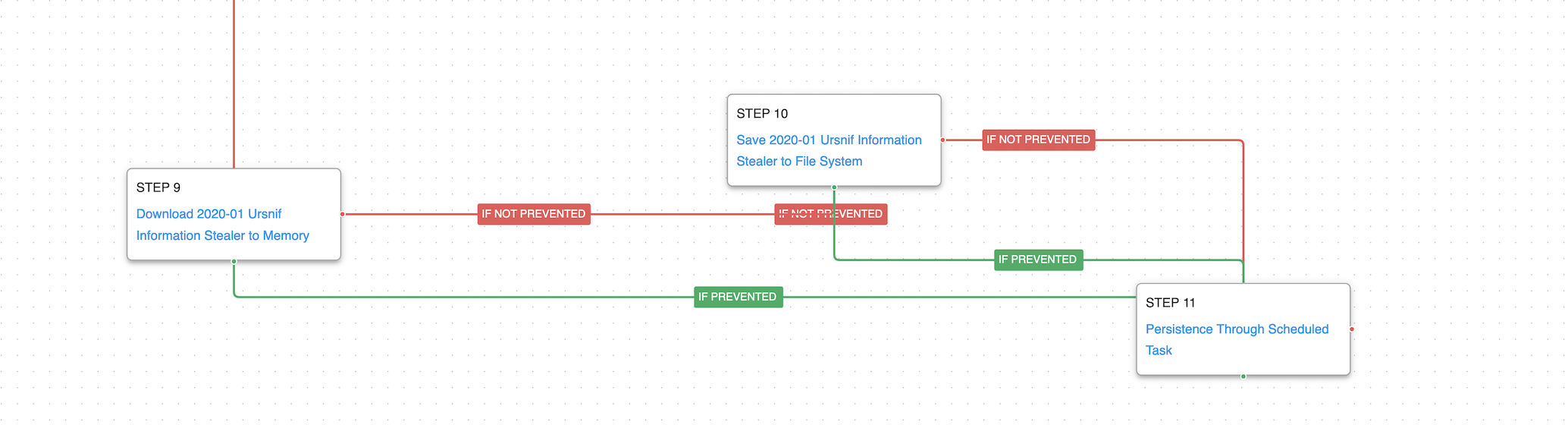 Click for Larger
Click for Larger

