In pursuit of this mission AttackIQ became a founding research partner of MITRE Engenuity’s Center for Threat-Informed Defense in 2019 to further the practice of threat-informed defense and help defenders take a strategic approach to their security programs. The goal? To put MITRE ATT&CK and adversary emulation into practice.
The Center for Threat-Informed Defense has just launched its 2022 Impact Report, and that presents a good time to look back and take stock at how we at AttackIQ have adopted research and development into the AttackIQ Security Optimization Platform and the practice of threat-informed defense. Since the founding of the Center for Threat-Informed Defense in 2019, AttackIQ has made leading contributions to key Center projects to include Attack Flows, Micro-Emulation Plans, Top ATT&CK Techniques, and NIST 800-53 Security Controls Mappings to ATT&CK, and cloud security stack mappings, as well as others. AttackIQ’s partnership with the Center spans beyond research as we supplement each research project with an AttackIQ Academy course and integrate the Center’s research into our platform. In this post we outline some of the specific details about why we selected these Center projects, how AttackIQ has helped drive the Center’s research, and the ways in which we incorporate research into the AttackIQ Security Optimization Platform.
Attack Flows
Let’s start with research that underpins our advanced adversary emulation capabilities: attack flow and attack graphs. AttackIQ is committed to advancing the art of adversary emulation and that means producing emulations and assessments that mirror the adversary’s behavior in the real world with specificity and granularity. That is why we sponsored the Center’s research on attack flows. Under the Center’s definition, an Attack Flow “is a machine-readable representation of sequences of adversary techniques used in an attack.” Through this project, AttackIQ and the Center developed a data format for describing sequences of adversary behavior to test an organization’s defenses with specificity, moving through an attack in a logical chain. Using behaviors in MITRE ATT&CK, attack flows help executives, security operations center managers, and defensive operators to easily understand and visualize how attackers conduct attacks. Techniques combine into a representation, modeling flows for a corpus of incidents, and create visualization tools to display the attack.
From Attack Flows to Attack Graphs
To make the Center’s research operational, AttackIQ incorporates ATT&CK-based adversary behaviors into multi-stage attack graphs that defenders can use to evaluate their security controls and generate performance data about their teams’ and technologies’ performance. The AttackIQ Adversary Research Team observes adversary behavior in the real world and builds attack graphs about emerging threats, including by responding to US-CERT alerts within 24 and 72 hours with attack graphs that incorporate threat intelligence and build on the U.S. government’s analysis of adversary behaviors, using MITRE ATT&CK. Attack graphs are particularly useful when applied to purple teaming exercises, as they enable security teams to move beyond a description of an attack sequence to then determine methods to detecting threats and break the kill chain.
As one example, AttackIQ released an attack graph emulating the Cuba ransomware group to help customers validate their security controls and their ability to defend against this threat actor and others who follow similar behaviors. Validating your security program performance against a specific threat actor’s behavior is vital for reducing risk, and by using attack graphs in the AttackIQ Security Optimization Platform, security teams can:
- evaluate security control performance against malicious techniques in use by active operators;
- assess their security posture against actors who pursue these and similar pathways; and
- continuously validate detection and prevention pipelines beyond the initial access exploits.
As shown below, the initial access methods of these attacks vary from victim to victim, and this attack graph starts with the delivery of the Hancitor malware. The attack graph moves through the installation of the kernel driver payloads, the execution of local and remote discovery commands, and the various methods used to gain additional credentials. It then transitions to emulating the behaviors observed in the Cuba ransomware group’s ROMCOM malware family before finishing with a ransomware attack to encrypt user documents.
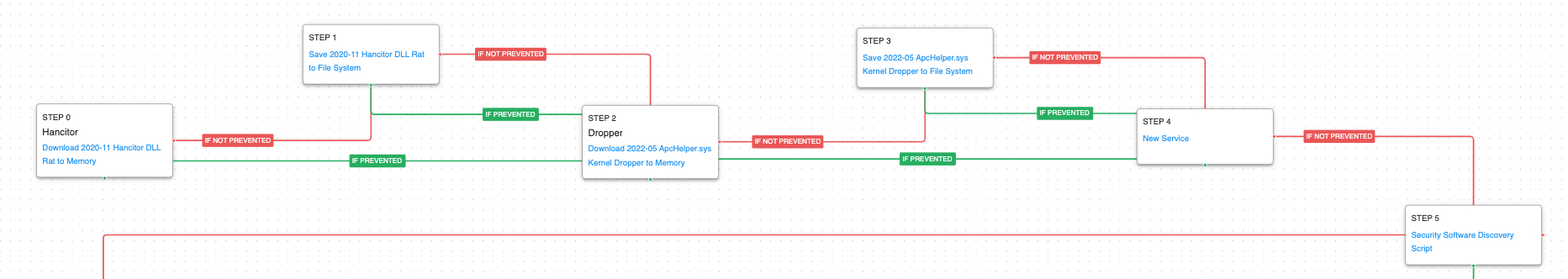
To give you a sense of how attack graphs work, the first steps in this attack graph are the delivery of the Hancitor malware and ApcHelper kernel driver dropper. The actor creates a service for initial persistence and scans the host to determine what security software is installed.
Putting attack graphs into action, the AttackIQ Security Optimization Platform produces emulation plans in the form of atomic scenarios and end-to-end attack graphs that mimic a range of ransomware families, and strings together adversary TTPs in attack graphs that emulate the adversary with specificity and realism. Defenders can use these graphs to test their organization’s security program continuously and automatically. Enumerating complete kill-chain sequences in this manner both better prepares organizations for real-world attacks and provides high-level efficacy when testing modern ML—and AI—based security controls.
Micro-Emulation Plans
This past year, we funded the Center for Threat-Informed Defense’s research into “ micro-emulation plans”, combining adversary tactics, techniques, and procedures into plans that are easier to digest than the Center’s full-scale adversary emulation plans. The Micro Emulation Plan project helps scale the impact of the Center for Threat-Informed Defense’s Adversary Emulation Library, making the library useful for companies that may lack sophisticated red teams, helping even those without a red team to run scenarios.
We at AttackIQ are obviously very bullish about the idea of defense teams learning how to run adversary emulations. We are even more bullish about how AttackIQ does this better than anyone else. Our assessments, attack graphs, packet capture (PCAP) replay capability, and our open API give defenders the tools they need to run emulations at scale and in production to answer the question: are we ready for the next attack?
AttackIQ puts into practice what we learned from the micro-emulation plan project through the following key capabilities:
- The AttackIQ Security Optimization Platform tests in production, at scale across your security program, and it tests security controls against multiple adversary tactics, techniques, and procedures concurrently.
- Our platform has the deepest alignment with MITRE ATT&CK, our open API allows teams to build and deploy adversary emulations quickly, and teams can tailor their tests to validate specific regulatory, insurance, and board requirements.
- The AttackIQ Adversary Research Team produces attack graphs and assessments as soon as US-CERT publishes its alerts, through research you can see here.
- And our platform tests artificial intelligence and machine learning-based cyberdefense technologies with specificity and realism.
AttackIQ is committed to helping organizations validate their defenses quickly and easily by building smaller scale adversary emulation plans that are fully automated.
Top ATT&CK Techniques
This part year the Center published its Top ATT&CK Techniques project, providing defenders with a systematic approach to prioritizing ATT&CK techniques based on the threats that matter most to them. The Center’s open methodology considers technique prevalence, common attack choke points, and actionability to enable defenders to focus on the ATT&CK techniques that are most relevant to their organization. AttackIQ funded this project and has built the project into the Security Optimization Platform so that organizations can test and validate their defenses against top techniques.

The Center’s Top ATT&CK Techniques Calculator (above) makes building customized top technique lists easy. Users can create a top 10 technique list tailored to their organization. The Top Ransomware Technique List provides a starting point for defending against ransomware attacks and demonstrates how the Top ATT&CK Techniques methodology can be tailored to different use cases. Once customers have built a customized top technique list, they can use the AttackIQ Security Optimization Platform to test their security program’s effectiveness against these techniques.
The below images show how the Top ATT&CK techniques process works in the Security Optimization Platform.


Once users run the assessment, it displays security control performance results.

Aligning CVE and ATT&CK, Vulnerability and Threat Management
Not all vulnerabilities are created equal. In focusing on which vulnerabilities to patch first, the key strategic approach is to focus on the vulnerabilities that present the gravest threat to the organization if exploited. Today defenders struggle to integrate vulnerability and threat information and lack a consistent view of how adversaries use vulnerabilities to achieve their goals. Without context, it is difficult to prioritize patching. This is why AttackIQ funded research at the Center for Threat-Informed Defense to map adversary behaviors described in ATT&CK to MITRE’s common vulnerabilities and exposures (CVE) list, providing much-needed context. The research linked CVEs to ATT&CK techniques to form a contextual bridge between vulnerability management, threat modeling, and compensating controls, empowering defenders to better assess the true risk posed by specific vulnerabilities in their environment.
Putting this research into practice, AttackIQ now partners with a range of vulnerability management-focused companies to align vulnerability and threat management into a set of combined solutions. In a new joint solution that aligns vulnerability management data with ATT&CK-focused assessments, AttackIQ and its partners have built a data enrichment engine that allows teams to operate from a single set of assets and a single list of top-tier threats, running ATT&CK-focused assessments to generate real-time performance data to fix misconfigurations, improve team cohesion, and enhance decision-making. Armed with intelligence and research from MITRE ATT&CK and the Center for Threat-Informed Defense, this solution helps breakdown silos between red and blue teams to adopt a purple team construct that significantly improves internal coordination. Teams can use Jupyter notebooks to aggregate, analyze, and present information from the combined dataset in clear reports for the C-suite and the board, improving communication and confidence.
Combining data from our vulnerability management partners’ asset criticality analysis with AttackIQ’s security control validation data gives teams a single portrait of their overall risk posture – all from the perspective of critical assets. The joint solution provides a comprehensive picture of asset criticality, CVE, security control performance measurements. Defenders can see how the organization will respond from the point of entry at the vulnerability to critical compensating controls’ response, as well as a clear picture of their security control effectiveness.
NIST Compliance Assessment
Over the last year and a half, AttackIQ has continued to align ATT&CK-focused testing capabilities to the security controls in the NIST 800-53 family, leveraging research from the Center for Threat-Informed Defense. In the winter of 2020, the Center mapped Revisions 4 and 5 of the NIST 800-53 controls to the adversary behaviors described by the ATT&CK framework. By using breach and attack simulation to connect NIST 800-53 controls to MITRE ATT&CK techniques, security teams can strengthen their overall security program in important ways. First, it creates a common understanding of the adversary techniques that a specific security control or set of controls is designed to detect or mitigate. From this understanding flows shared knowledge about which security controls the organization should implement to properly defend itself against a particular adversary behavior. The security team can then use AttackIQ to validate that policies, teams, and technologies function as intended; data then helps team leaders to optimize their security program over time to achieve greater operational effectiveness and resource use.
What does that mean specifically? The integrated NIST-ATT&CK perspective provides security leaders with greater clarity about overall program readiness in relation to known threats and the existence of compensating security controls for all the relevant NIST 800-53 Control Families. The net result is that the organization better understands where gaps exist—and where the organization may benefit from additional security investments to adhere to specific control families. With that information, security leaders can prioritize investments and make better long-term budgeting and resource-allocation decisions.
NIST Testing with AttackIQ
Building on the Center’s research, AttackIQ has introduced new assessments into the Security Optimization Platform that take adversary behaviors from the AttackIQ library to guide testing activity and produce evidence about their performance in meeting key NIST security controls.
The AttackIQ Security Optimization Platform provides output in an easy-to-understand visual presentation that can be delivered as a report for reference and briefings. The Security Optimization Platform also offers API access to its results to support a host of other integration and automation use cases.


Security Control Cloud Mappings
The advent of the cloud age has increased productivity but brought with a host of novel challenges for the security community. Defenders lack visibility into adversary behaviors in cloud technologies, leaving organizations exposed. To confront this challenge, AttackIQ and the Center for Threat-Informed Defense delivered a trilogy of projects to help cloud technology users map security controls to MITRE ATT&CK. Through this research and subsequent application, users of Microsoft Azure, Amazon Web Services (AWS), and Google Cloud Platform (GCP) can now build a scoring methodology and use it to map the effectiveness of native security controls within their respective cloud platform to specific ATT&CK techniques.
Through tight integration with the MITRE ATT&CK framework, cloud users can apply this research to their native environment directly in the AttackIQ Security Optimization Platform. Our prebuilt templates streamline scenario testing for specific ATT&CK TTPs, and its integration of up-to-date threat intelligence facilitates the application of a threat-informed defense.


Threat-Informed, Brick by Brick
AttackIQ is the industry’s first and leading independent provider of breach and attack simulation solutions and automated security control validation, and we deliver performance data to security teams across the world from Fortune 10 to Global 2000 companies so that they can make better decisions. Our mission is to make the world safe for compute, and that mission extends far beyond the benefits that our platform provides. As a founding research partner of the Center for Threat-Informed Defense, we believe in democratizing the practice of adversary emulation for everyone. Our contributions to research, education, and defender empowerment are pillars we stand on and help define our identity. As a key partner to the Center, we remain committed to creating and expanding impact in threat-informed defense research. To receive regular updates about our work, sign up for research updates on our AttackIQ Adversary Research Team page.

