Targeted Sectors: Manufacturing, Communications, Healthcare and Public Healthcare (HPH), and Education
On March 2, 2022, the Cybersecurity and Infrastructure Security Agency (CISA) and the Federal Bureau of Intelligence (FBI) released a joint Cybersecurity Advisory (CSA) to continue their #StopRansomware efforts to help organizations protect themselves against ransomware attacks.
This latest advisory covers attacks against U.S. and international organizations involving the deployment of variants of the Royal ransomware. The actors behind these attacks have targeted multiple critical infrastructure sectors including communications, education, healthcare, and manufacturing. While these actors have purchased access to potential victims in the past, they primarily conduct their own initial intrusions using spearphishing and malvertising to trick users into downloading trojanized software.
The most recent attacks involving Royal ransomware have leveraged the Batloader downloader. These are malicious MSI installation files that execute a hidden PowerShell command to download a second-stage Windows batch file. This file leads to additional downloads of more PowerShell scripts, utilities, and malware.
The PowerShell scripts perform many defense evasion techniques to weaken the security of the infected asset and set the groundwork for the information stealers and backdoors. The actors then use shared commodity malware like Ursnif, Vidar, and Cobalt Strike. Their end goal is to exfiltrate sensitive data for extortion before finally encrypting files with their custom ransomware known as Royal.
AttackIQ has released a new attack graph emulating a recent Royal ransomware attack to help customers validate their security controls and their ability to defend against this determined adversary.
Validating your security program performance against these behaviors is vital to reducing risk. By using these new attack graphs in the AttackIQ Security Optimization Platform, security teams will be able to:
- Evaluate security control performance against an actor who is relentless in attempting to weaken your system’s security controls.
- Assess their security posture against both ransomware and data extortion outcomes.
- Continuously validate detection and prevention pipelines that leverage a combination of native system tools along a significant number of downloads of third-party utilities.
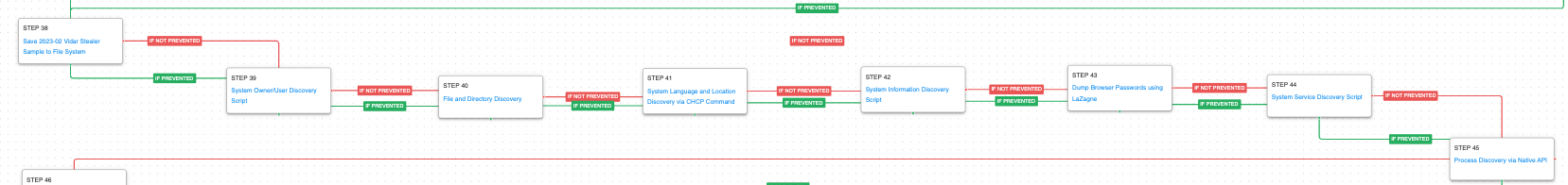
Stages of the Attack Graph
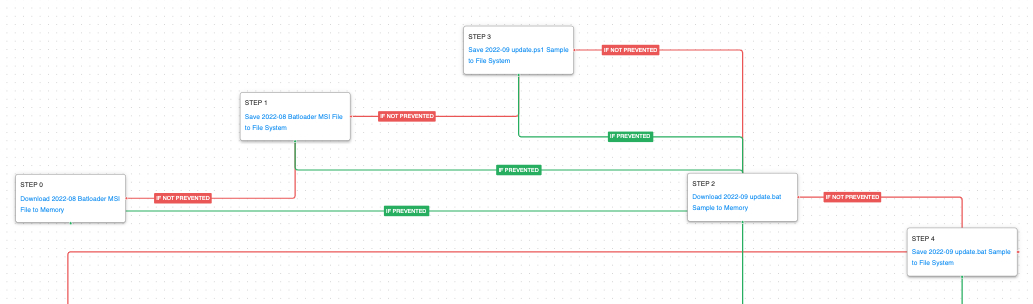
This attack graph emulates a full cyberattack involving Royal ransomware. It starts with the delivery and emulation of Batloader’s initial defense evasion techniques and its attempts to weaken security controls. This is followed up by emulations of their second and third-stage malware families of Ursnif and Vidar and their attempts to steal sensitive data. The final stage of the attack involves the deployment of Cobalt Strike and a ransomware event to encrypt local files.
The first stage of the attack is focused on the deployment of Batloader. This arrives as a malicious MSI file that installs a trojanized version of a legitimate software package. When the software is installed a hidden PowerShell script is executed that begins downloading various batch files and other PowerShell scripts that will be used in the later stages of the attack.
Ingress Tool Transfer (T1105): These scenarios download to memory and save to disk in independent steps to test network and endpoint controls and their ability to prevent the delivery of known malicious samples. The operators behind Royal ransomware use PowerShell to download all of the stages of their attack and many of the additional utilities they use in later steps.
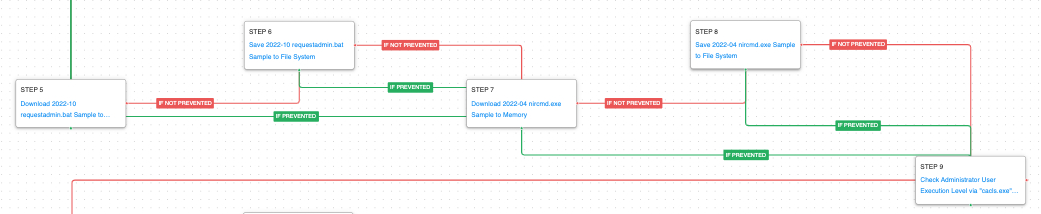
The second stage continues the downloading of their payloads and ends with the execution of a native Windows command to determine if they are currently running with elevated permissions.
Windows File and Directory Permissions Modification (T1222.001): This scenario uses the native Windows cacls.exe utility to check their permissions against a restricted directory. The return code will tell the actor if they are already running with elevated privileges.
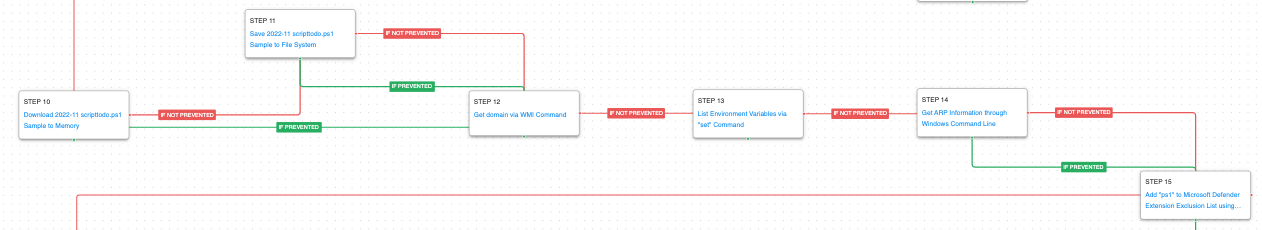
After validating that elevated privileges are achieved, more stages are downloaded before the malware collects some initial information about the infected host including the infected host’s domain, the computer’s name, and network table. It finishes by setting up an exclusion in Microsoft defender for all PowerShell scripts to ensure that future stages will not be detected.
Windows Management Instrumentation (WMI) (T1047): WMI is a native Windows administration feature that provides a method for accessing Windows system components. This scenario executes the computersystem get domain command to retrieve the host’s connected Active Directory domain.
System Information Discovery (T1082): The actor collects all the environmental variables. These variables can be a great source for credentials and important configuration settings used by different applications.
System Network Configuration Discovery (T1016): The network configuration of the asset is collected using the standard Windows utility arp.
Impair Defenses: Disable or Modify Tools (T1562.001): PowerShell is used to add exclusions to the Microsoft Defender policy. This first time all PowerShell scripts (.ps1) are added to the exclusion list.
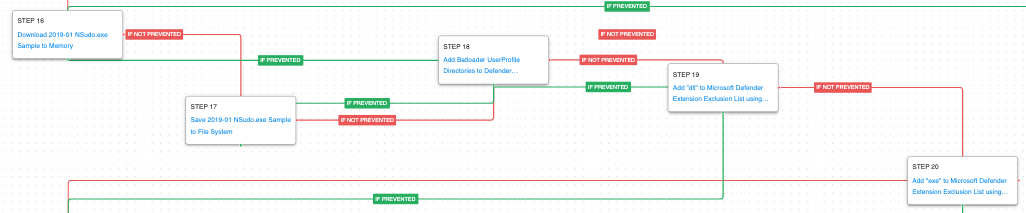
After bringing down even more scripts and tools the actor continues to weaken the infected hosts’ security controls. This time they are adding directory exclusions along with expanding the excluded extensions to include all executable file types.
Impair Defenses: Disable or Modify Tools (T1562.001): PowerShell commands are executed by the threat actor to add directory exclusions for the %USERPROFILE% and the Roaming subdirectory. They use a built-in cmdlet called Add-MpPreference to add a series of folders to the exclusion list in Microsoft Defender. This is for any processes executing in those directories or interacting with files in those directories.
Impair Defenses: Disable or Modify Tools (T1562.001): PowerShell is once again used to add exclusions to the Microsoft Defender policy. This time all Executables (.exe and .dll) and PowerShell scripts (.ps1) are added to the exclusion list.
The fifth stage continues the actor’s onslaught against the system’s security controls. This time they are focused around removing the ability for end users to observe and find malicious processes or execute commands that would assist in stopping the attack.
Modify Registry (T1112) / Disable or Modify Tools (T1562.001): The actor uses the native Windows reg command to disable a series of security controls and Windows features that would inhibit the recovery of the system before the ransomware can complete.
ConsentPromptBehaviorAdmin – This registry key controls if Windows should prompt administrators for consent before performing elevated actions.
Notification_Suppress – This registry key controls the Windows notifications that appear like warnings that antivirus has been disabled.
DisableTaskMgr – This key when enabled will prevent a user from accessing the Task Manager and observing the presence of suspicious processes.
DisableCMD – When enabled, this command will prevent users from accessing a command shell which could be used to troubleshoot and identify problems.
DisableRegistryTools – Tools to modify and fix the registry to revert these changes will not be accessible for users.
NoRun – This key will remove the Run command from the Start Menu making it more difficult to execute commands and programs that can defend against the attack.
Impair Defenses: Disable or Modify Tools (T1562.001): The actor uses the native powercfg.exe utility to increase the delay before a system would enter power savings mode. This allows the actor to ensure they will not accidentally lose access to an infected host due to being idle.
Group Policy Modification (T1484.001): The actors were able to make modifications to a group policy that would bring down additional payloads and continue to weaken security controls. This scenario forces a machine to refresh its group policy settings.
Service Stop (T1489): Not satisfied with the exclusions previously put in place, the Windows Defender service is stopped with a net stop command.
With the shields significantly weakened it’s time for the actor to start achieving their objectives. They use the commodity malware Ursnif to perform some discovery actions and exfiltrate sensitive files.
System Binary Proxy Execution: Regsvr32 (T1218.010): RegSvr32 is a native Windows utility that threat actors can use to register Common Object Model (COM) DLLs. This functionality allows an actor to deploy a malicious DLL and have a native Windows tool execute the code as the parent process. This scenario executes RegSvr32 with an AttackIQ binary.
Process Injection (T1055): This scenario injects a DLL file into another running process and validates if a canary file can be created.
Remote System Discovery (T1018): Search for other domain computers using the net group command.
System Network Connections Discovery (T1049): The native Windows command net session is used to list all connected remote sessions.
Exfiltration Over Unencrypted Non-C2 Protocol (T1048.003): This scenario exfiltrates sensitive data using HTTP POSTs to an AttackIQ controlled server.
Nearing the end of the attack, the actors deploy Vidar Stealer. This is primarily used to complete a few additional discovery techniques and steal user credentials.
System Owner/User Discovery (T1033): Executes the native query user and whoami commands to receive details of the running user account.
File and Directory Discovery (T1083): A batch script is executed that lists all files and directories in %ProgramFiles% and the %systemdrive%\Users directory.
System Language Discovery (T1614.001): Windows code pages are used to customize the language of the system. Threat actors can use the native Microsoft Windows chcp utility to get the number of active console code page. This information can later be utilized by the actor to determine the system language and location.
System Information Discovery (T1082): The native systeminfo command is executed to retrieve all of the Windows system information.
OS Credential Dumping (T1003): This scenario uses the open-source tool LaZagne to dump user credentials available on the host.
System Service Discovery (T1007): Microsoft’s native sc utility is executed to query a list of all running services.
Process Discovery (T1057): The Windows API is used to receive a list of running process by calling CreateToolhelp32Snapshot and iterating through each process object with Process32FirstW and Process32NextW.
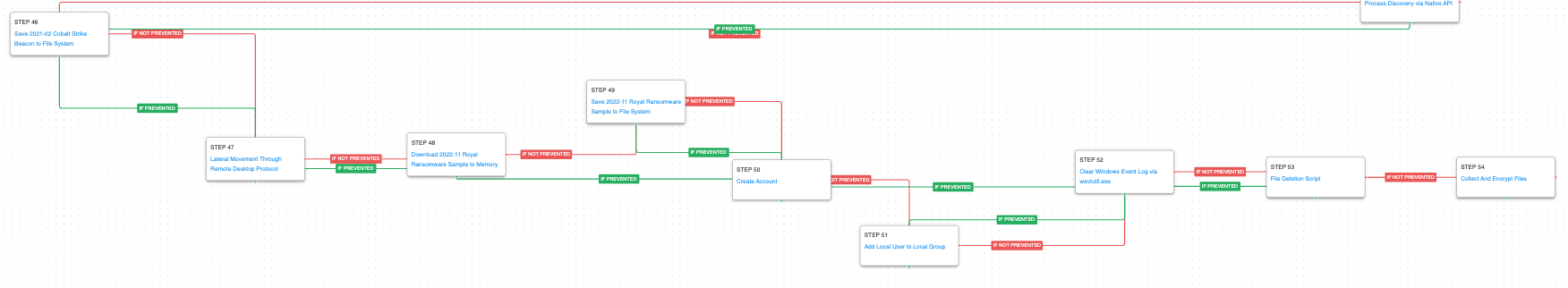
The final stage of the attack involves Cobalt Strike. The actor will attempt to move laterally to additional hosts using the network data and credentials they have discovered. A new account is created and added to the Administrators group to help preserve access in case their original credentials are revoked. They clear event logs to hide all traces of their activity before deleting any backups. Finally, the Royal Ransomware is deployed and files are encrypted.
Remote Services: Remote Desktop Protocol (T1021.001): Attempt to use Remote Desktop to move laterally to additional hosts and identify additional data for exfiltration and extortion.
Create Account: Local Account (T1136.001): Actors create a new account using net user that they can exclusively use in case their original access gets revoked.
Account Manipulation (T1098): The newly created account is added to the Local Administrators group to increase permissions.
Indicator Removal: Clear Windows Event Logs (T1070.001): This scenario uses the built-in Windows utility wevtutil to delete system event logs. Actors will perform this at the end of their operations to clean up evidence of the breach.
Inhibit System Recovery (T1490): Runs vssadmin.exe to delete a recent Volume Shadow Copy created by the attack graph.
Data Encrypted for Impact (T1486): This scenario performs the file encryption routines used by common ransomware families. Files matching an extension list are identified and encrypted in place using similar encryption algorithms observed in Royal ransomware.
Detection and Mitigation Opportunities
With so many different techniques being used by threat actors, it can be difficult to know which to prioritize for prevention and detection assessment. AttackIQ recommends first focusing on the following techniques emulated in our scenarios before moving on to the remaining techniques.
1. Ingress Tool Transfer (T1105)
This actor relies heavily on downloading additional stages of malware using PowerShell. Endpoint and Network security controls should both be employed to try and detect the delivery of these malicious payloads.
1a. Detection
The following signatures can help identify when native utilities are being used to download malicious payloads.
PowerShell Example:
Process Name == (Cmd.exe OR Powershell.exe)
Command Line CONTAINS ((“IWR” OR “Invoke-WebRequest") AND “DownloadData” AND “Hidden”)
1b. Mitigation
MITRE ATT&CK has the following mitigation recommendations.
2. Impair Defenses: Disable or Modify Tools (T1562.001):
This actor made heavy use of limiting what Microsoft Defender is able to scan by setting exclusions for processes, paths, and file extensions.
2a. Detection
Describe what the pseudo-signature is going to detect and where the signature would be applied.
Process Name == Powershell.exe
Command Line CONTAINS (“Add-MpPreference” AND
(“-ExclusionPath” OR “-ExclusionProcess” OR “-ExclusionExtension”) )
2b. Mitigation
MITRE ATT&CK has the following mitigation recommendations.
- M1038 – Execution Prevention
- M1022 – Restrict File and Directory Permissions
- M1024 – Restrict Registry Permissions
- M1018 – User Account Management
3. Data Encrypted for Impact (T1486)
It should go without saying that as a last resort, preventing your systems and files from being encrypted should be your number one focus. Ensuring that you have the layered endpoint defenses including Antivirus and EDR solutions is critical.
3a. Detection
Ransomware attacks are best prevented and alerted by your EDR/AV Policies. Typically, a configuration for ransomware protection is presented and we strongly encourage that it is enabled in your security controls.
There are three telling signs of ransomware activity in an environment that you could query for and possibly make preventative detections if your security controls allow. Those three are deletion of shadow volumes, suspicious amounts of exfiltrated data, and of course, wide set file encryption.
Detecting deletion of shadow volumes is usually the first step that occurs and can be detected by looking at command line activity:
Via vssadmin.exe:
Process Name == (cmd.exe OR powershell.exe)
Command Line CONTAINS (“vssadmin” AND “Delete Shadows”)
Via PowerShell:
Process Name == powershell.exe
Command Line == “Get-WmiObject Win32_Shadowcopy | ForEach-Object ($_.Delete();)”
Detecting suspicious Data Exfiltration:
Detecting exfiltration is well suited for IDS/IPS and DLP solutions. These products should be configured to identify sensitive files. If sensitive files, or a large amount of web traffic is sent to a rare external IP, it should be detected or prevented depending on security policies for the security control. Historical NetFlow data logging can also bubble up hosts that are experience uncommon peaks in outgoing traffic.
Detecting Ransomware-like File Encryption:
Utilizing an EDR or SIEM/SOAR product can help detect and prevent suspicious file encryption related to ransomware attacks. Utilizing these tools to look for excessive file modifications (greater than 1000 on a system) within less than a minute of time is a good starting indicator. To increase the fidelity a bit, you could include file modification file extension to popular ransomware extensions such as .conti, .Locky, .Ryuk, etc. If possible, with a SOAR or preventative EDR platform, we recommend setting these detections to kill all processes involved in creating the alert as it will most likely stop the spread of the Ransomware.
3b. Mitigation
MITRE ATT&CK has the following mitigation recommendations for <Technique>
Wrap-up
In summary, this attack graph will evaluate security and incident response processes and support the improvement of your security control posture against another top ransomware actor. With data generated from continuous testing and use of this attack graph, you can focus your teams on achieving key security outcomes, adjust your security controls, and work to elevate your total security program effectiveness against a known and dangerous threat.
AttackIQ stands at the ready to help security teams implement this attack graph and other aspects of the AttackIQ Security Optimization Platform, including through our co-managed security service, AttackIQ Vanguard.