APT36, also known as Transparent Tribe, is a politically motivated Pakistan-based adversary that has been active since at least 2013. APT36 has been observed targeting diplomatic entities, defense contractors, and research organizations from several countries, primarily in India and to a lesser extent Afghanistan, Kazakhstan, and Saudi Arabia, with the objective of collecting sensitive information that supports Pakistani military and diplomatic decision-making.
The group was discovered by Proofpoint in 2016 during operation Transparent Tribe, hence the adversary’s alias, when APT36 targeted several officials at Indian embassies in both Saudi Arabia and Kazakhstan with the objective of directing them to watering hole websites focused on Indian military personnel. APT36 is linked to the adversary known as the Gorgon Group, an espionage-motivated group with connections to Pakistan that has directed attacks against government organizations in the United Kingdom, Spain, Russia, and United States.
Throughout 2022, APT36 was observed targeting Indian government organizations with the abuse of malicious Google advertisements in order to distribute a trojanized installer that masquerades as Kavach, a multi-factor authentication (MFA) application. During this activity, the adversary conducted very low-volume credential harvesting attacks with links masquerading as official Indian government websites and luring unsuspecting users to enter their credentials.
Validating your security program performance against these behaviors is vital in reducing risk. By using these new attack graph(s) in the AttackIQ Security Optimization Platform, security teams will be able to:
- Evaluate security control performance against an actor who uses many different initial access vectors but follows a similar attack path post compromise.
- Assess their security posture against attacks that complete very little discovery techniques and instead move quickly towards data exfiltration.
- Continuously validate detection and prevention pipelines involving network and endpoint controls from an attack conduct without the need for administrative privileges.
APT36 – 2022-11 – Campaign against Indian Governmental Organizations
This attack graph will conduct a full attack chain beginning with the delivery of the actor’s first stage malware before moving through their basic discovery playbook and leading to the exfiltration of sensitive data.
The attack graph starts immediately by downloading one of the fake installers for the Kavach application. The installer collects information about the system time zone, which determines if the victim is one of their intended targets by limiting further execution only if the time zone matches Indian Standard Time (IST).
Ingress Tool Transfer (T1105): This scenario downloads to memory and saves to disk in independent scenarios to test network and endpoint controls and their ability to prevent the delivery of known malicious samples.
System Time Discovery (T1124): The scenario identifies the time and time zone of the compromised system through the net time command.
Data Staged: Local Data Staging (T1074.001): Files are collected and stored in a temporary directory so they can be exfiltrated later.
After the victim has been verified the installer will drop the actor’s backdoor known as LimePad. This tool has the capability to take screenshots from the logged in user and sets up persistence using shortcut files. The backdoor will collect system information that it will use as part of its future command and control requests.
Screen Capture (T1113): This scenario executes a PowerShell script that utilizes the Graphics.CopyFromScreen method from the System.Drawing namespace to collect screenshots from the compromised system.
Shortcut Modification (T1547.009): The scenario creates a shortcut that is used to execute a program during system boot or during the user logon process.
System Information Discovery (T1082): The native systeminfo command is executed to retrieve all the Windows system information.
The final stages of the attack involve making two requests to the command-and-control server of HTTP to register with the attacker’s server and pass along profiling data. The malware will then immediately begin to search for files of interest and start exfiltrating them to the actor’s infrastructure using HTTP POST requests.
Application Layer Protocol: Web Protocols (T1071.001): These two scenarios emulates the HTTP requests made by LimePad backdoor by making an HTTP POST to an AttackIQ server that mimics the URL format and data sent during a real infection.
File and Directory Discovery (T1083): This scenario uses the native dir command to find files of interest and output a file listing to a temporary location.
Exfiltration Over C2 Channel (T1041): Files are sent to an AttackIQ controlled server using HTTP POST requests and validated to verify the files were not modified in transit.
Detection and Mitigation Opportunities
With so many different techniques being used by threat actors, it can be difficult to know which to prioritize for prevention and detection. AttackIQ recommends first focusing on the following techniques emulated in the scenarios emulated in this attack graph:
1. Exfiltration Over C2 Channel (T1041)
These attacks result in the immediate exfiltration of sensitive data from the infected host, and it does not wait for an actor to issue any commands.
1a. Detection
The data is being exfiltrated without any throttling or additional encoding or encryption from the backdoor. All data is being sent via HTTP POSTs in plain text and therefore should be easier to detect using Data Loss Prevention tools.
Additionally, since these requests are not throttled, network traffic can be monitored for anomalous traffic flow patterns that can identify single systems, typically client assets, that are sending out significant amounts of data.
1b. Mitigation
MITRE ATT&CK has the following mitigation recommendations:
2. Application Layer Protocol: Web Protocols (T1071.001)
The actor’s use of simplistic unencrypted HTTP requests is the ideal use case for network traffic inspection tools like an Intrusion Detection System.
2a. Detection
The following simple Suricata rules can be used to detect LimePad network requests. It is highly recommended that your IPS/IDS be constantly up to date with new signatures from vendors or free resources like Emerging Threats.
alert http any any -> any any (msg:"LimePad Initial Checkin Request (GET)"; flow:established,to_server; http.method; content:"GET"; http.uri; content:".php"; http.header_names; content:"Username"; http.header_names; content:"Auth_Token"; http.user_agent; content:"Python-urllib"; fast_pattern; startswith; classtype:trojan-activity; sid:9001; rev:1;)
alert http any any -> any any (msg:"LimePad pong! Response"; flow:established,from_server; http.response_body; content:"pong!"; fast_pattern; classtype:trojan-activity; sid:9002; rev:1;)
alert http any any -> any any (msg:"LimePad System Information (POST)"; flow:established,to_server; http.method; content:"POST"; http.uri; content:".php"; http.request_body; content:"USERNAME="; http.request_body; content:"_v1_"; http.request_body; content:"&PASSWORD="; http.user_agent; content:"Python-urllib"; fast_pattern; startswith; classtype:trojan-activity; sid:9003; rev:1;)
2b. Mitigation
MITRE ATT&CK has the following mitigation recommendations:
Wrap-up
In summary, this attack graph will evaluate security and incident response processes and support the improvement of your security control posture against an unsophisticated but successful threat actor . With data generated from continuous testing and use of this attack graph, you can focus your teams on achieving key security outcomes, adjust your security controls, and work to elevate your total security program effectiveness against a known and dangerous threat.
AttackIQ stands at the ready to help security teams implement this attack graph and other aspects of the AttackIQ Security Optimization Platform, including through our co-managed security service, AttackIQ Vanguard.
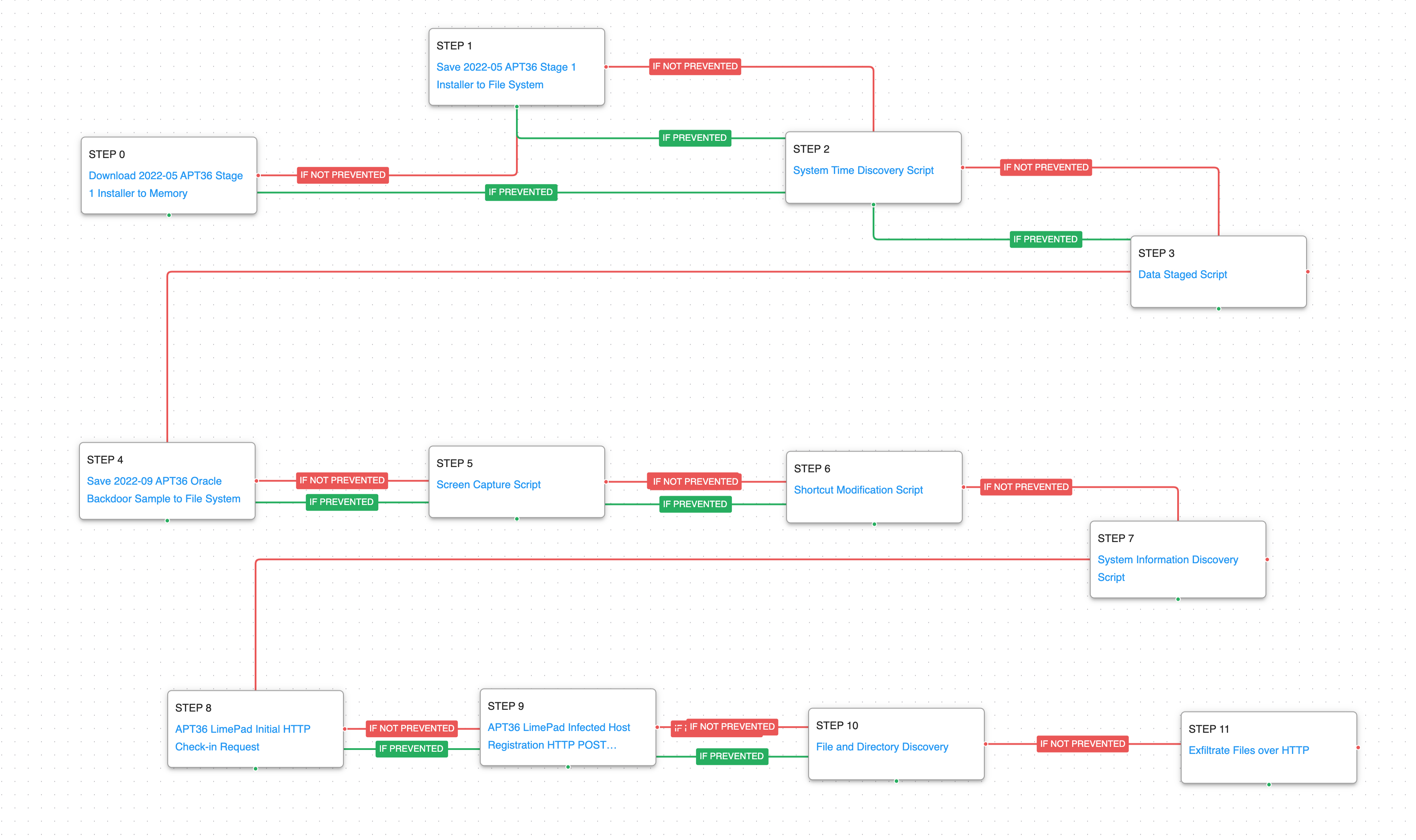 (Click for Larger)
(Click for Larger)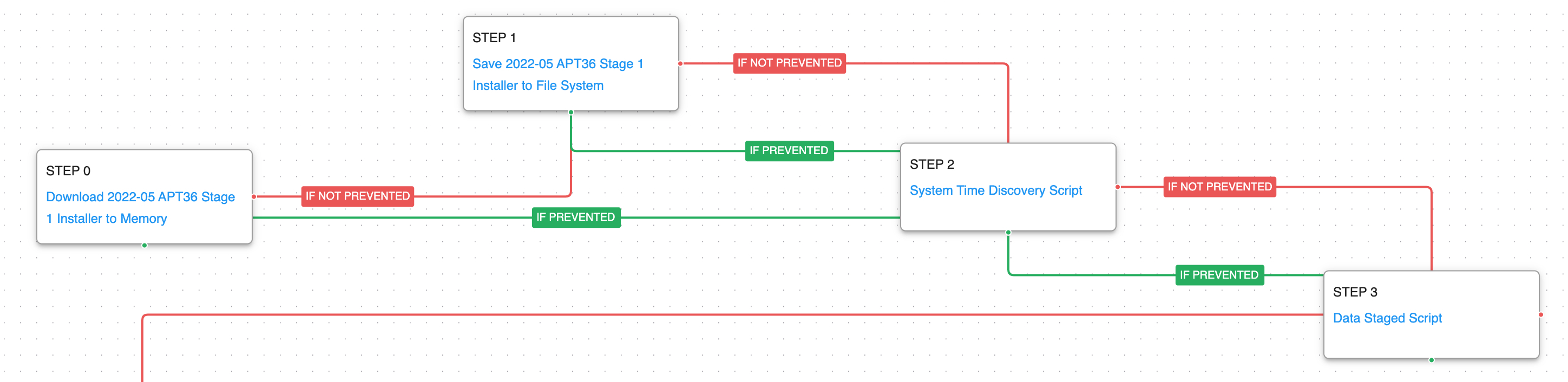 (Click for Larger)
(Click for Larger)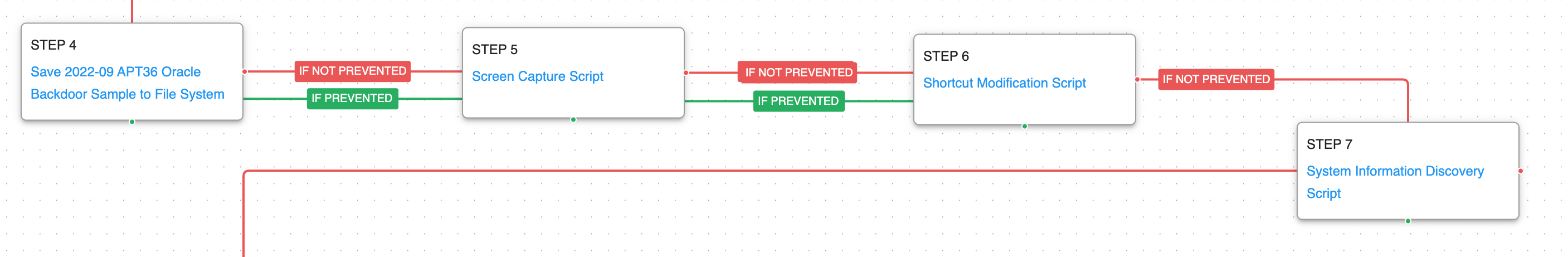 (Click for Larger)
(Click for Larger)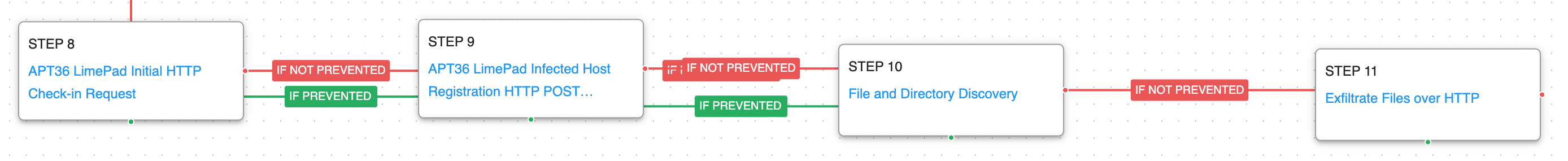 (Click for Larger)
(Click for Larger)
