BlueNoroff is a North Korean-sponsored, a financially motivated adversary that has exclusively targeted financial institutions, financial trading software development companies, cryptocurrency exchanges, cryptocurrency trading companies, and decentralized finance protocols. In the past, BlueNoroff has demonstrated a particular interest in the Society for Worldwide Interbank Financial Telecommunication (SWIFT) software, learning the inner workings of the software and protocols to implement patches that would allow attackers to bypass security controls to steal significant amounts of money without leaving a trace.
The actors are notorious for the attack against the Bangladesh Central Bank (BCB) in February 2016, when the adversary created fraudulent SWIFT transactions for more than $850 million. Their technical procedures were undetected, and it was only a small spelling mistake that foiled their plans and ultimately flagged the transactions for manual review.
AttackIQ has released four new attack graphs emulating the actor’s historical campaigns to help customers validate their security controls and their ability to defend against one of the subgroups of the infamous Lazarus group.
Validating your security program performance against these behaviors is vital in reducing risk. By using these new attack graph(s) in the AttackIQ Security Optimization Platform, security teams will be able to:
- Evaluate security control performance against a financially motivated actor who has re-used techniques across the years to steal millions of dollars.
- Assess their security posture against a threat actor who can live off the land or use their own bespoke malware to achieve their goals.
- Continuously validate detection and prevention pipelines against a subset of North Korean activity who share successful techniques.
BlueNoroff – 2016-08 / 2017-01 – Southeast Asian and European Bank Attacks
The first attack graph covers a set of attacks first identified by Kaspersky in a February 2017 report that detailed the attacks against the SWIFT systems of a bank in Southeast Asia in August 2016 and an unknown bank in Europe in January 2017.
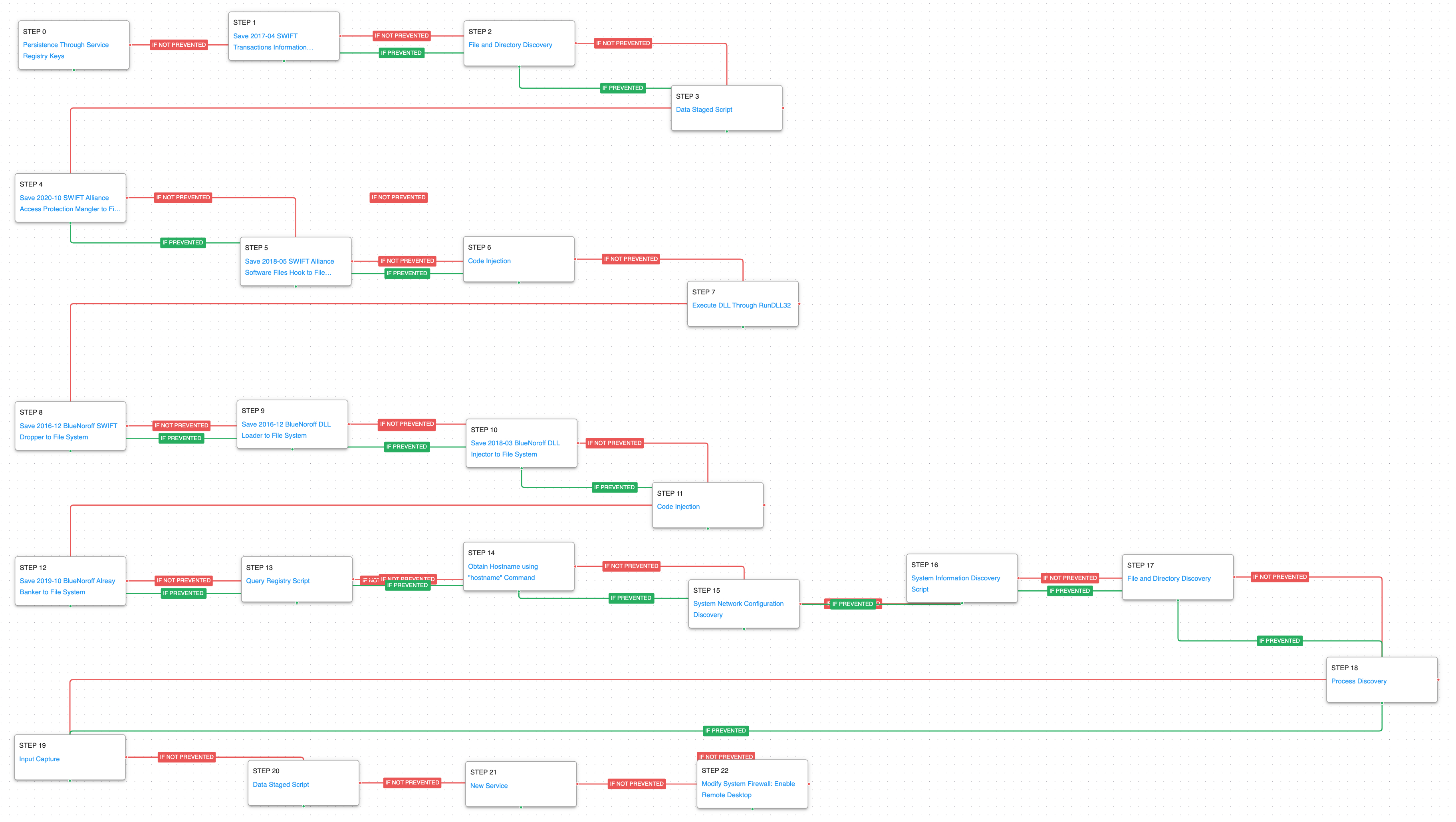
The attack graph starts with obtaining persistence by creating a service. Immediately after, the actors pulled down malware that searched for files of interest on the system and then saved them in a temporary location.
Windows Service (T1543.003): The registry keys for a service with the name helpsvcs is created that would automatically start a process at system boot.
Ingress Tool Transfer (T1105): This scenario saves to disk a sample of the actor’s SWIFT Harvester malware to test endpoint controls and their ability to prevent the delivery of known malicious samples.
File and Directory Discovery (T1083): This scenario uses the traditional dir command to find files of interest and output to a temporary file.
Data Staged: Local Data Staging (T1074.001): Files are collected and stored in a temporary directory so they can be exfiltrated later.
Two second stage tools are written to disk which can then be injected into an active process or subsequently executed using a native Windows tool.
Process Injection (T1055): This scenario injects a DLL file into another running process and validates if a canary file can be created.
System Binary Proxy Execution: Rundll32 (T1218.011): RunDll32 is a native system utility that can be used to execute DLL files and call a specific export inside the file. This scenario executes RunDll32 with an AttackIQ DLL and calls an export to mimic previously reported malicious activity.
The actor’s third and fourth stage tools are dropped and executed using the same process observed in the previous stages. A registry key is used to hold a decryption key used to decode the stages. Once the fourth stage malware is executed the actor begins to execute discovery commands to learn more about the infected host, its local network, and the running processes.
Query Registry (T1012): The HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\svchost\netsvcs contains a decryption key used by BlueNoroff.
System Owner/User Discovery (T1033): query user and whoami are called to determine what account the malware is currently operating under.
System Network Configuration Discovery (T1016): The network configuration of the asset is collected using standard Windows utilities like ipconfig, arp, route, and nltest.
System Information Discovery (T1082): The native hostname and systeminfo commands are used to get the infected host’s computer name and basic details about the system.
Process Discovery (T1057): From a command window the tasklist command is run to download a list of all running processes.
The final steps involve the deployment of a keylogger and the staging of the final files that the actor wishes to exfiltrate. A new service is created to establish persistence and firewall rules are opened that would allow for external access to the infected host using Remote Desktop.
Input Capture: Keylogging (T1056.001): A keylogger is executed that hooks API callbacks to collect keystrokes typed by a logged in user.
Windows Service (T1543.003): Use the native sc command line tool to create a new service that will executed at reboot.
Disable or Modify System Firewall (T1562.004): The local host firewall is configured to allow for incoming RDP connections so the actors can move away from interacting with their backdoor and begin using the native Windows functionality.
BlueNoroff – 2017-10 – Far Eastern International Bank (FEIB) SWIFT Attack
In October 2017 BlueNoroff attacked the Far Eastern International Bank (FEIB), a commercial firm in Taiwan, and attempted to move funds from accounts to multiple overseas beneficiaries. This attack graph emulates the activity observed during the attack against the bank starting with the delivery of their custom malware and the discovery techniques taken by the actor to understand the compromised environment. The final steps of the attack graph led to the deployment of a ransomware scenario that BlueNoroff used as part of a false flag operation to distance themselves from the true intent of the attack.
The actor begins by downloading their Bitsran loader to the system which uses the Registry to set persistence. The malware collects information about the environment by executing multiple native commands and creates a scheduled task to deploy the final payload.
Ingress Tool Transfer (T1105): This scenario downloads to memory and saves to disk in two separate scenarios to test network and endpoint controls and their ability to prevent the delivery of known malicious samples. These scenarios are used for each stage of the malware delivered in these attacks.
Logon Autostart Execution: Registry Run Keys (T1547.001): This scenario sets the HKLM\Software\Microsoft\Windows\CurrentVersion\Run and RunOnce registry keys that Windows uses to identify what applications should be run at system startup.
Security Software Discovery (T1518.001): A PowerShell script is executed to determine which software has been installed as an AntiVirusProduct class.
System Network Configuration Discovery (T1016): Native Window’s commands like route, ipconfig, and net use are executed to collect details about the infected host and network shares.
Scheduled Task/Job: Scheduled Task (T1053.005): This scenario creates a new scheduled task using the schtasks utility with the name BITSRAN that was observed being used in these attacks.
The scheduled task downloaded the actor’s next stages of malware which setup persistence using a new service.
Windows Service (T1543.003): Use the native sc command line tool to create a new service named AuditCred that will be executed at reboot.
The final steps in this attack graph download the actor’s final payload, the Hermes Ransomware, which was used as part of their false flag operations to obscure the financial theft.
System Language Discovery (T1614.001): The Windows API function GetSystemDefaultUILanguage is called to retrieve the language code of the system’s default language pack.
Data Encrypted for Impact (T1486): This scenario performs the file encryption routines used by common ransomware families. Files matching an extension list are identified and encrypted in place using the same encryption algorithms observed in the Hermes ransomware.
BlueNoroff – 2021-11 – SnatchCrypto Campaign (Weaponized Word document)
In January 2022, SecureList released a report detailing the SnatchCrypto campaign, where BlueNoroff was observed stalking successful cryptocurrency startups.
This infection chain starts from a malicious Word document leveraging remote template injection with an embedded malicious Visual Basic Script (VBS). Following similar process in their previous attacks, malicious code is injected into a running process that downloads and executes the next stage.
The actor’s backdoor is downloaded and saved to the file system and uses a file in the Windows Startup directory for persistence. When the second stage is executed it first gathers information about the logged in user that the malware will use as part of its initial check-in to the actor’s command and control infrastructure.
Logon Autostart Execution: Startup Folder (T1547.001): The Startup folder is a directory associated with the Windows Start Menu that can be used to launch a process at Windows logon. This scenario creates a binary file in this directory that would execute at next logon for users.
Application Layer Protocol: Web Protocols (T1071.001): This scenario emulates the HTTP requests made by during the initial check-in observed in the SnatchCrypto attack. An HTTP POST is sent to an AttackIQ server that mimics the URL format and data sent by a real infection.
The final stage of malware is downloaded to the system before the actor collections some additional details on the infected host. A list of users connected via Remote Desktop is collected along other local administrative accounts. Files of interest and keystrokes are collected before finally being staged in a temporary directory and exfiltrated over HTTP.
Account Discovery: Local Account (T1087.001): The native query session command is executed to get a list of all users logged into the asset using Remote Desktop.
Permission Groups Discovery: Local Groups (T1069.001): The actor is interested in finding out the memberships of privileged local groups like Remote Desktop Users and Local Administrators. They accomplish this by executing net localgroup lookups.
Exfiltration Over C2 Channel (T1041): Files are sent to an AttackIQ controlled server using HTTP POST requests.
BlueNoroff – 2021-11 – SnatchCrypto Campaign (Weaponized Shortcut Files)
There were two techniques observed in the SnatchCrypto campaign that were used for the initial infection and this attack graph emulates the behaviors starting from a malicious LNK file that used MSHTA to download and execute a remote payload.
The final attack graph starts with the execution of MSHTA that downloads and executes a remote payload containing VBScript code. This code is responsible for making the initial command and control request to the actor’s infrastructure.
System Binary Proxy Execution: Mshta (T1218.010): Mshta.exe is a native Windows utility that threat actors can abuse to download remote payloads that include VBScript code.
The actor downloads and executes multiple sages of their malware that makes various HTTP POST requests to register and authenticate with the command-and-control servers to receive the final payloads.
The final stage of the infection continues to execute native discovery commands before finally dumping additional credentials.
Credentials from Password Stores: Windows Credential Manager (T1555.004): Mimikatz is used to dump additional credentials that would aid the actor in moving to additional hosts.
Credential Dumping (T1003): This scenario uses the open-source tool LaZagne to dump all possible credentials available on the host.
Detection and Mitigation Opportunities
With so many different techniques being used by threat actors, it can be difficult to know which to prioritize for prevention and detection assessment. AttackIQ recommends first focusing on the following techniques emulated in our scenarios before moving on to the remaining techniques.
1. Ingress Tool Transfer (T1105)
BlueNoroff commonly uses many different stages of malware in both the initial compromise and post compromise stages of their attacks. Endpoint and Network security controls should both be employed to try and detect the delivery of these malicious payloads.
1a. Detection
The following signatures can help identify when native utilities are being used to download malicious payloads.
PowerShell Example:
Process Name == (Cmd.exe OR Powershell.exe)
Command Line CONTAINS ((“IWR” OR “Invoke-WebRequest") AND “DownloadData” AND “Hidden”)
certutil Example:
Process Name == Certutil.exe
Command Line Contains (“-urlcache” AND “-f” AND “http”)
Bitsadmin Example:
Process Name == Bitsadmin.exe
Command Line CONTAINS (“/transfer” AND “http”)
Curl Example:
Process Name == Curl.exe
Command Line CONTAINS (“http” AND “-o”)
1b. Mitigation
MITRE ATT&CK has the following mitigation recommendations
2. Windows Service (T1543.003)
Persistence is a key inflection point in an actor’s attack lifecycle. Concerned about their potential loss of access, they are going to take steps to ensure they will remain on the infected host after reboots or partial remediation efforts. Disrupting their ability to maintain their foothold will help prevent their immediate return.
2a. Detection
The following rules can help identify when that persistence mechanism is being set.
Process Name == (Cmd.exe OR Powershell.exe)
Command Line CONTAINS (‘sc’ AND ‘create’ AND ‘start= “auto”’)
2b. Mitigation
MITRE ATT&CK has the following mitigation recommendations
3. System Binary Proxy Execution: Rundll32 (T1218.011)
Adversaries may abuse rundll32.exe to proxy execution of malicious code. Using rundll32.exe instead of executing directly, may avoid triggering security tools that may not monitor execution of the rundll32.exe process because of allow-lists or false positives from normal operations.
3a. Detection
Using a SIEM or EDR product, you can monitor the use of benign tools such as rundll32.exe being used to execute possibly malicious DLLs. A common way to detect this activity is to detect when DLLs are being executed from a globally writable directory, such as C:\Windows\Temp\
Process Name = (“cmd.exe” OR “powershell.exe”)
Command Line CONTAINS (“rundll32” AND “.dll”)
Target File Path CONTAINS (“\temp\” OR “\tmp\”)
3b. Mitigation
MITRE ATT&CK has the following mitigation recommendations
Wrap-up
In summary, these attack graphs will evaluate security and incident response processes and support the improvement of your security control posture against North Korean threat actors. With data generated from continuous testing and use of these attack graphs, you can focus your teams on achieving key security outcomes, adjust your security controls, and work to elevate your total security program effectiveness against a known and dangerous threat.
AttackIQ stands at the ready to help security teams implement this attack graph and other aspects of the AttackIQ Security Optimization Platform, including through our co-managed security service, AttackIQ Vanguard.
 (Click for Larger)
(Click for Larger) (Click for Larger)
(Click for Larger) (Click for Larger)
(Click for Larger)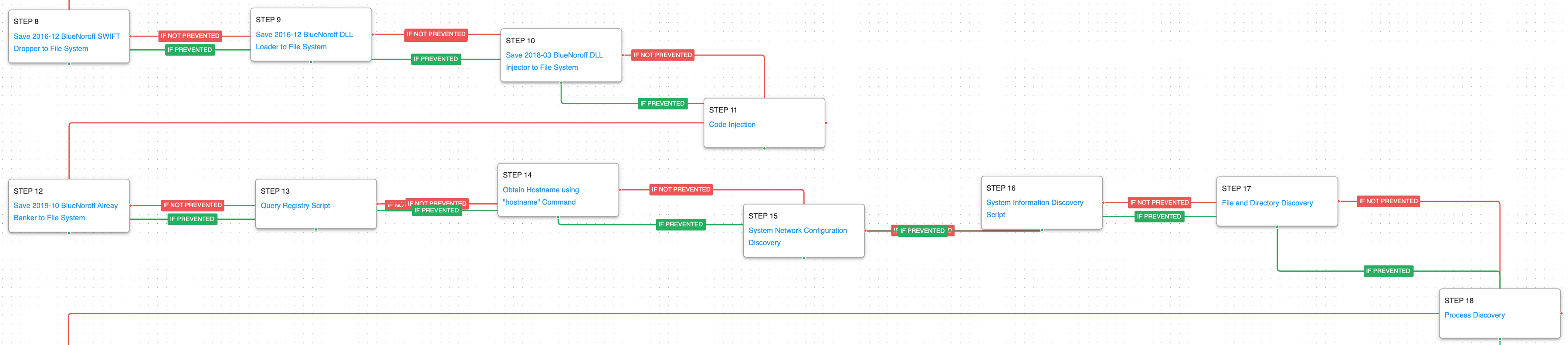 (Click for Larger)
(Click for Larger)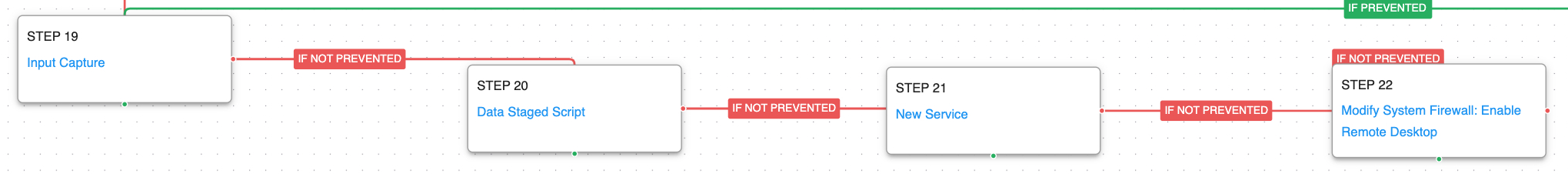 (Click for Larger)
(Click for Larger)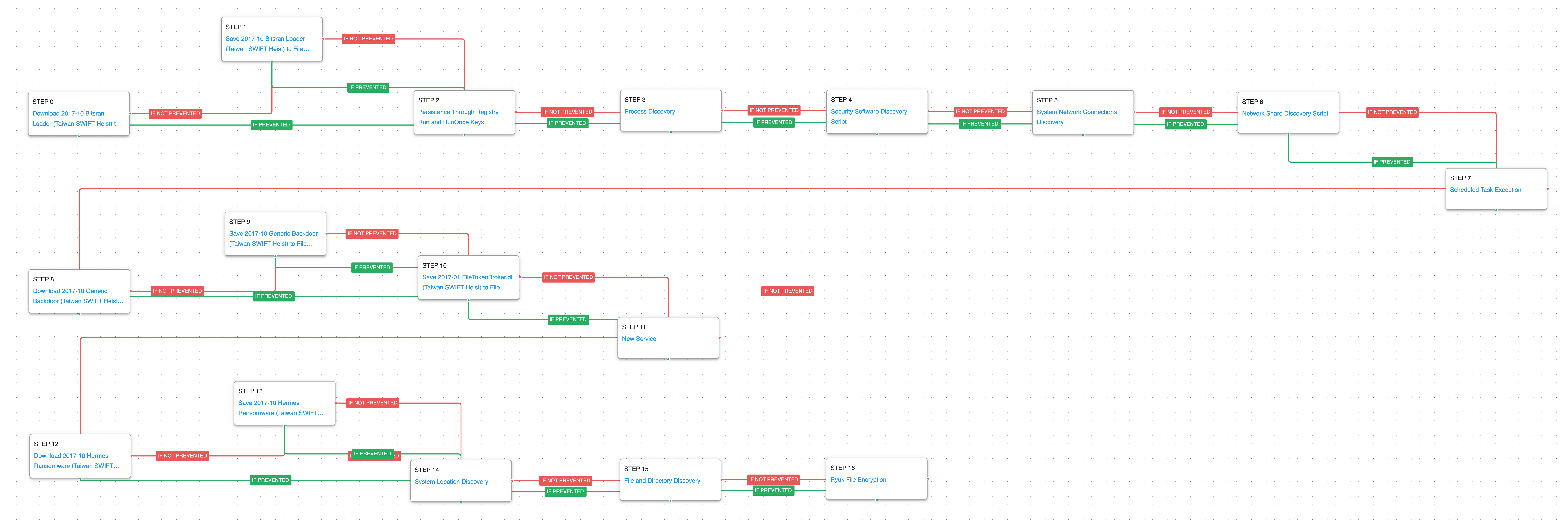 (Click for Larger)
(Click for Larger)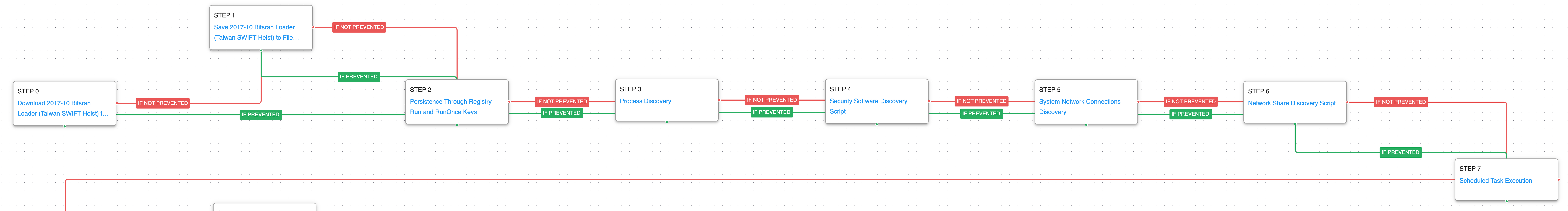 (Click for Larger)
(Click for Larger) (Click for Larger)
(Click for Larger) (Click for Larger)
(Click for Larger)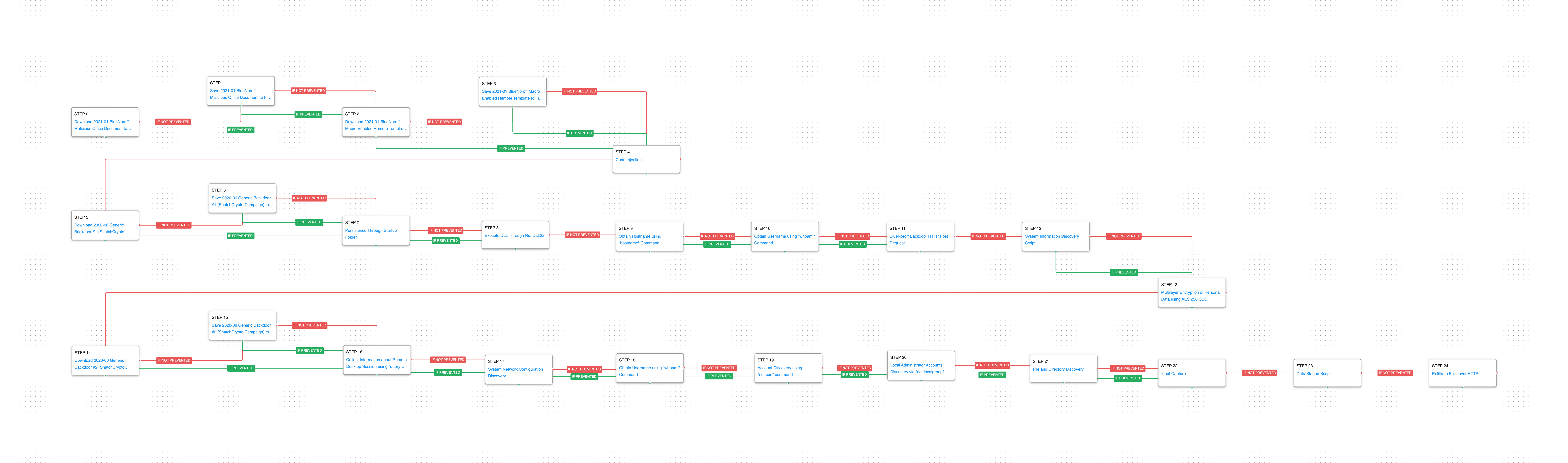 (Click for Larger)
(Click for Larger) (Click for Larger)
(Click for Larger)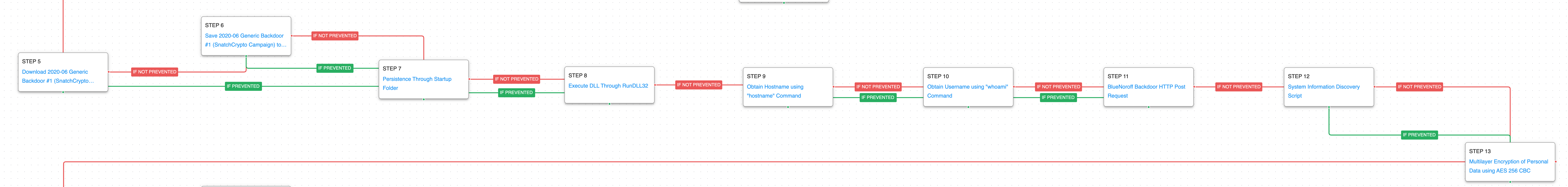 (Click for Larger)
(Click for Larger) (Click for Larger)
(Click for Larger)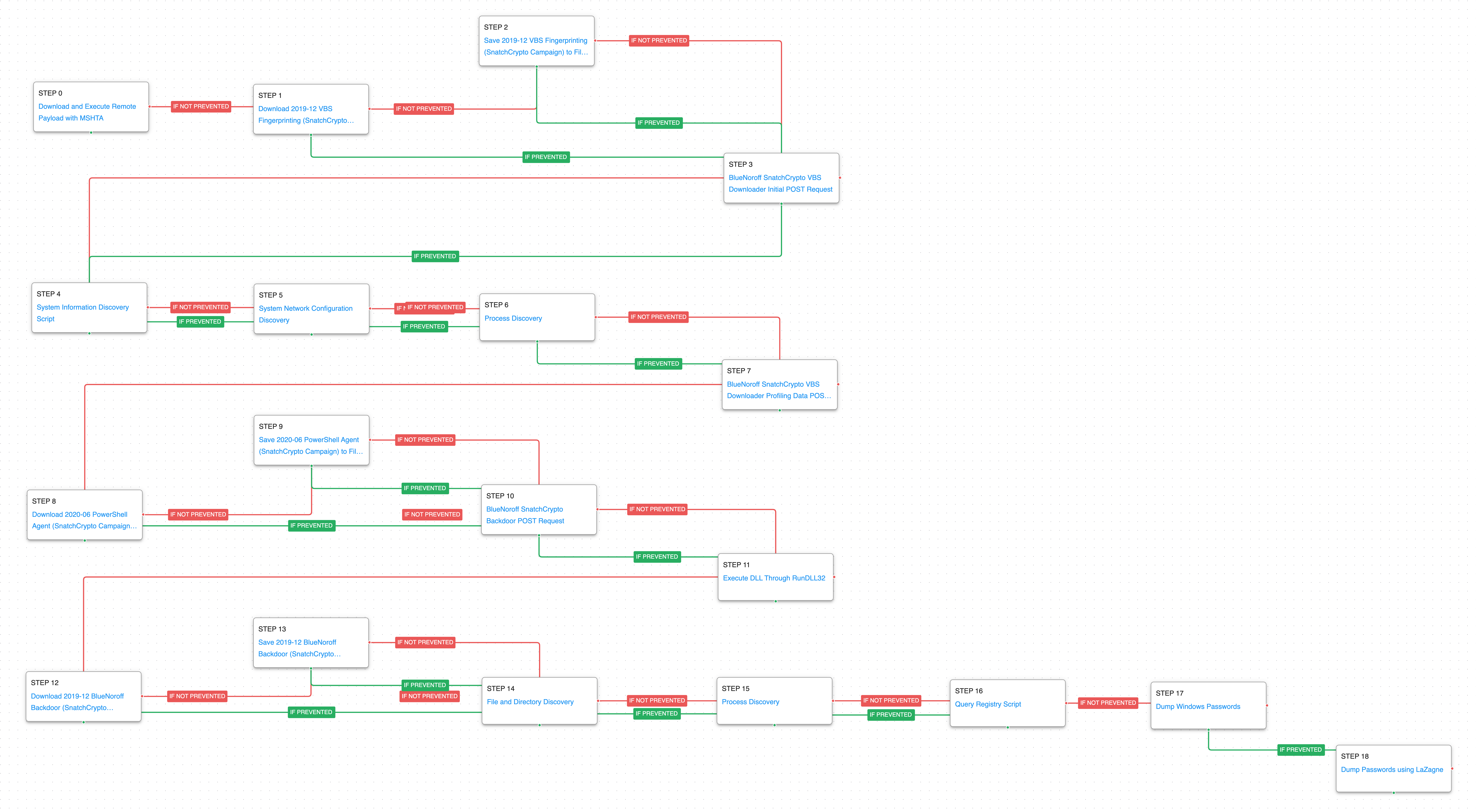 (Click for Larger)
(Click for Larger) (Click for Larger)
(Click for Larger) (Click for Larger)
(Click for Larger)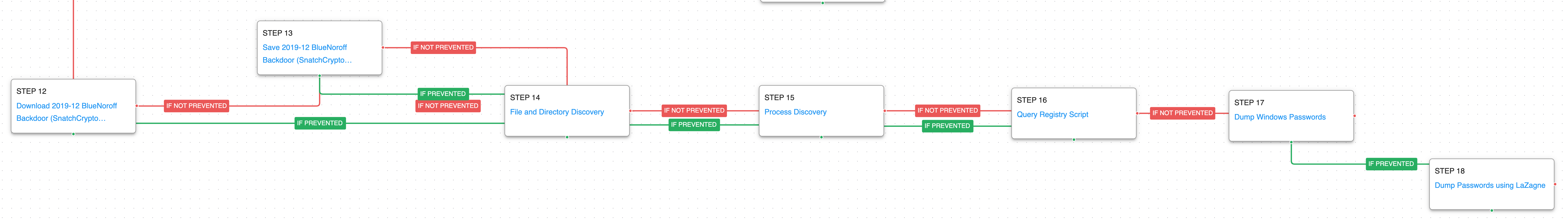 (Click for Larger)
(Click for Larger)
