On March 15, 2023, the Cybersecurity and Infrastructure Security Agency (CISA), the Federal Bureau of Intelligence (FBI), and the Multi-State Information Sharing and Analysis Center (MS-ISAC) published a joint Cybersecurity Advisory (CSA) disclosing two compromises that occurred between November 2022 and early January 2023 at a Federal Civilian Executive Branch (FCEB) agency.
Two separate adversaries were able to exploit a .NET deserialization vulnerability (CVE-2019-18935) in the Progress Telerik user interface (UI) running on the agency’s Microsoft Internet Information Services (IIS) web server. Through the exploitation, the threat actors uploaded Dynamic-link Library (DLL) files, masquerading as Portable Network Graphics (PNG) files, and injected them into the IIS Worker Process to gain initial access.
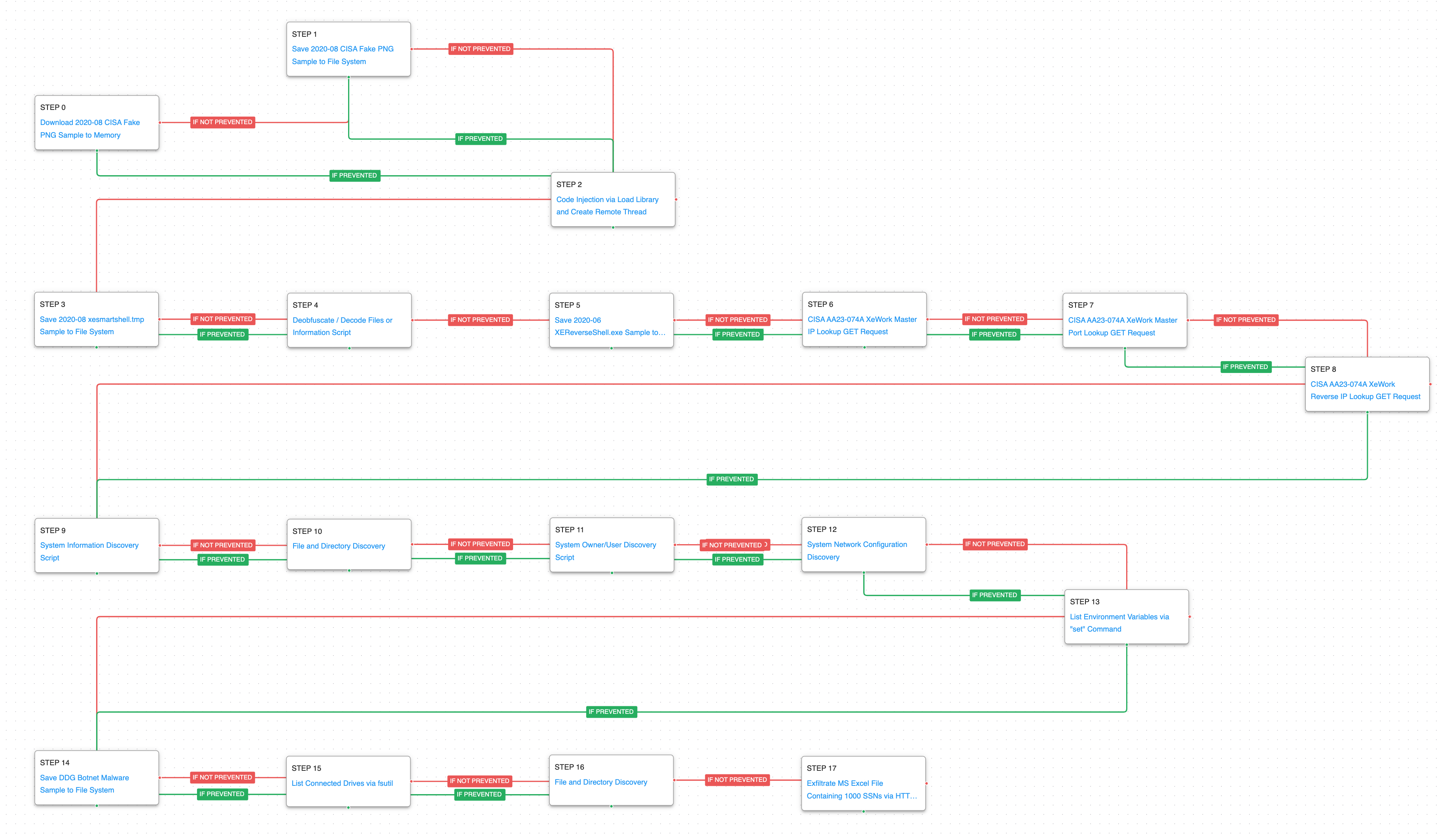
AttackIQ has released a new attack graph emulating the activities carried out by the second adversary, a Vietnamese cybercriminal actor identified as the XE Group. After exploiting the vulnerability, the actor dropped malware that downloaded additional payloads and created a reverse shell to the threat actor’s infrastructure. The final goal was internal reconnaissance and exfiltration of sensitive data.
Validating your security program performance against these behaviors is vital in reducing the risk of ransomware. By using this new attack graph in the AttackIQ Security Optimization Platform, security teams will be able to:
- Evaluate security control performance against the post-compromise and discovery techniques that will occur no matter which vulnerability is initially exploited.
- Assess their security posture against an opportunistic cybercriminal group that has automated large portions of the initial attack chain.
- Continuously validate detection and prevention pipelines against other cybercriminal actors who use a similar playbook to discover more data about their victims.
[CISA AA23-074A] Multiple Actors Exploit Telerik Vulnerability to Deploy Webshells and Backdoors
This attack graph emulates four stages of the compromise by XE Group. The graph starts with the saving and execution of the malware that was delivered using the Telerik vulnerability. This malware would then decode additional payloads and make initial network requests to establish a reverse shell. Once the shell was established they would perform common discovery techniques before moving on to exfiltration of data.
The first stage of the attack drops and saves the initial masquerading DLL payloads delivered by XE Group. This file would be executed using code injection that loads the DLL file into the memory of another process.
Ingress Tool Transfer (T1105): These scenarios download to memory and save to disk in independent steps to test both network and endpoint controls and their ability to prevent the delivery of known malicious samples.
Process Injection (T1055): This scenario injects a DLL file into another running process and validates if a canary file can be created.
In the second stage of the attack, a second payload that was encoded with base64 is deobfuscated using the native Windows utility CertUtil. This payload is executed and makes three network requests to determine what IP Address and Port should be used to establish a reverse TCP shell.
Deobfuscate/Decode Files or Information (T1140): Use the legitimate certutil binary to decode a base64 encoded payload.
Application Layer Protocol: Web Protocols (T1071.001): This scenario emulates the initial HTTP requests made by XE Group’s malware by making three HTTP GET requests to an AttackIQ controlled server that mimics the URL format and data sent by a real infection.
The next stage of the attack is focused on environment discovery with the adversary seeking to collect relevant system information. During this stage, the adversary obtains information about the initial infected host, interesting files and directories, the current network configuration, and any environment variables.
System Information Discovery (T1082): The native systeminfo command is executed to retrieve all of the Windows system information.
File and Directory Discovery (T1083): This scenario uses the traditional dir command to find files of interest and output to a temporary file.
- System Owner / User Discovery (T1033): Live off the land by running
whoamiandusersto gain details about the currently available accounts and permission groups.
System Network Configuration Discovery (T1016): Native Window’s commands like route, ipconfig, and net use are executed to collect details about the infected host and network shares.
System Information Discovery (T1082): Execute the set command to print all the environmental variables. These variables can be a great source for credentials and important configuration settings used by different applications.
In the fourth and final stage of the attack, the adversary drops a webshell called small.aspx which allows for obtaining additional information about the disks available on the system and the files and directories they contain. The last step culminates with the exfiltration of the collected information.
Peripheral Device Discovery (T1120): This scenario retrieves information about the system’s logical drives through the execution of the fsutil command.
Exfiltration Over C2 Channel (T1041): Files are sent to an AttackIQ controlled server using HTTP POST requests.
Detection and Mitigation Opportunities
With so many different techniques being used by threat actors, it can be difficult to know which to prioritize for prevention and detection assessment. AttackIQ recommends first focusing on the following techniques:
1. Exploit Public-Facing Application (T1190)
The vulnerability exploited in these attacks was discovered in December 2019 and received a CRITICAL 9.8 CVSS score. The compromise of the web server occurred almost 3 years after patches were made available.
Having a robust asset and software inventory and a functional vulnerability management program is paramount to reducing risk.
1a. Mitigation
- M1048 – Application Isolation and Sandboxing
- M1050 – Exploit Protection
- M1030 – Network Segmentation
- M1026 – Privileged Account Management
- M1051 – Update Software
- M1016 – Vulnerability Scanning
2. Process Injection (T1055)
During the exploitation of this vulnerability, malicious code was injected into the IIS Worker Process. Additionally, some actors will intentionally inject in existing legitimate processes to attempt to hide their tracks.
2a. Detection
Searching for common processes that are performing uncommon actions can help identify when a process has been compromised. In this instance, the w3wp.exe process was used and would be observed executing all of the discovery commands performed by the actor. These standard Windows commands would not normally be executed by this process. You can look for similar activity using a signature like:
Parent Process Name == w3wp.exe
Command Line CONTAINS (‘set’ OR ‘whoami’ OR ‘ping’ OR ‘dir’)
2b. Mitigation
Wrap-up
In summary, this attack graph will evaluate security and incident response processes and support the improvement of your security control posture against another a cybercrime actor who is known to exploit common critical vulnerabilities. With data generated from continuous testing and the use of these attack graphs, you can focus your teams on achieving key security outcomes, adjust your security controls, and work to elevate your total security program effectiveness against a known and dangerous threat.
AttackIQ stands at the ready to help security teams implement this attack graph and other aspects of the AttackIQ Security Optimization Platform, including through our co-managed security service, AttackIQ Vanguard.
 (Click for Larger)
(Click for Larger) (Click for Larger)
(Click for Larger) (Click for Larger)
(Click for Larger) (Click for Larger)
(Click for Larger) (Click for Larger)
(Click for Larger)
