On March 16, 2023, the Federal Bureau of Investigation (FBI), the Cybersecurity and Infrastructure Security Agency (CISA), and the Multi-State Information Sharing & Analysis Center (MS-ISAC) released a joint Cybersecurity Advisory (CSA) with the objective of disseminating known LockBit 3.0 ransomware indicators and techniques identified through FBI investigations. This joint CSA is part of their ongoing #StopRansomware effort to arm network defenders with the intelligence they need to combat different ransomware variants and ransomware threat actors.
LockBit is a ransomware family that has been active since September 2019 and operates under the Ransomware-as-a-Service (RaaS) model. Affiliates complete the intrusions and delivery of LockBit which handle the ransom payments and negotiations. LockBit has continued to improve and evolve over time with three primary variants: LockBit, LockBit 2.0 and LockBit 3.0.
LockBit 3.0, also reported under the name “LockBit Black”, is more modular and evasive compared to previous version of LockBit variants. LockBit 3.0 shares similarities with other ransomware families, such as Blackmatter and Blackcat.
Since LockBit operates under a RaaS model, there isn’t a standard intrusion playbook used by affiliates. Those actors will leverage a wide variety of Tactics, Techniques, and Procedures (TTPs) in the initial stages of the attack. The attack graph released by AttackIQ combines the new CISA alert with a recent report published by Fortinet, which shed light on the other activities observed during an intrusion from one of the affiliates.
AttackIQ has released a new fully featured attack graph that emulates these attacks involving the LockBit 3.0 ransomware with the aim of helping customers validate their security controls and their ability to defend against this determined adversary.
Validating your security program performance against these behaviors is vital in reducing risk. By using this new attack graph in the AttackIQ Security Optimization Platform, security teams will be able to:
- Evaluate security control performance against the core behaviors observed in the installation and execution of LockBit 3.0.
- Assess their security posture against one of the opportunistic affiliates and the additional actions taken to weaken a target’s defenses.
- Continuously validate detection and prevention pipelines against other affiliates who will likely leverage similar techniques in their own intrusions.
[CISA AA23-075A] #StopRansomware: LockBit 3.0
This attack graph starts with the delivery of a malicious IMG file containing hidden files and a Shortcut (LNK) file to initiate the infection. The initial stages of the attack are automated using a series of batch files (BAT) and Visual Basic Scripts (VBS). The actors would additionally move laterally to a domain controller and modify group policy to weaken endpoint security controls. The final stage of the attack emulates the final Lockbit 3.0 encryption of data. It uses the system language to validate an intended target before checking in with an emulated version of the actors command-and-control server. Volume Shadow Copies are deleted, and files are encrypted.
This first stage deals with the delivery IMG file that functions similar to ISO files, when opened in Windows the file is mounted like a disk drive and the Windows Explorer window is displayed to the user. Inside this IMG file are 6 additional files that will be used throughout the infection. Subsequently, the attacker will list the active sessions on the network to determine if they are operating on a server or endpoint.
Ingress Tool Transfer (T1105): This scenario downloads to memory and saves to disk in two separate scenarios to test network and endpoint controls and their ability to prevent the delivery of known malicious samples.
System Network Connections Discovery (T1049): Using net session the adversary can get a list of remote connections established to and from the infected asset.
In the second stage of the attack, the adversary will seek to obtain persistence through multiple mechanisms. In the first instance, he will attempt to modify an account to have a password the actor controls. They then attempt to enable automatic login to the Windows workstation using registry keys. It will then create a new service on the system and seek to force that service to start when the system is restarted in Safeboot minimal mode. The actors would force a reboot at this stage so they could access the system while other security tools and applications that would lock files would not be executing. Alternatively, if the service creation fails, the actor will set a batch file to be executed at Winlogon.
Create Account: Local Account (T1136.001): In this example of the attacks, the actors needed to create a new account instead of blending in as an existing local account. An account with the name LocalAdmin is created using net user.
Logon Autostart Execution (T1547): This scenario sets modifies the registry value AutoAdminLogon to enable automatic login with an administrative account at system startup.
Create or Modify System Process: Windows Service (T1543.003): Creates a new service mimicking the name used in LockBit intrusions called tckzpj using the native sc.exe utility.
Impair Defenses: Safe Mode Boot (T1562.009): This scenario will attempt, through the registry, to force the configure a service to be executed at startup when a machine has been rebooted in Safeboot’s minimal mode.
Once the persistence stage is completed, the attack graph will start the discovery and collection phase. In this phase, the adversary seeks to collect relevant information from the environment, identify disks connected to the system to propagate to, and attempt to generate a dump of the LSASS process so that it could retrieve additional credentials that could be used to move laterally.
System Information Discovery (T1082): The native systeminfo command is executed to retrieve all of the Windows system information.
System Owner / User Discovery (T1033): Live off the land by running whoami and users to gain details about the currently available accounts and permission groups.
Peripheral Device Discovery (T1120): This scenario retrieves information about systems peripherals such as logical drives, physical memory, network cards through the execution of commands and binaries.
Network Service Discovery (T1046): This scenario uses PowerShell for scanning hosts that are open on ports 21, 22, 23, 25, 80, 110, 139, 443, 445 and 3389 that would identify remotely accessible hosts to the attacker.
OS Credential Dumping: LSASS Memory (T1003.001): LSASS memory is dumped to disk by creating a minidump of the lsass process. This process is used for enforcing security policy on the system and contains many privileged tokens and accounts that are targeted by threat actors.
If the LSASS process dump is not prevented, the attack graph will continue with lateral movement to other systems via Remote Desktop Protocol (RDP). This will start the stage in which the adversary seeks to disable system features through making Group Policy changes which result in registry modifications. The attacker will seek to modify the normal Group Policy refresh time and force immediate Group Policy updates. These new policies would disable multiple security features of the system such as Windows Defender monitoring and reporting, Windows privacy experience, and the system’s firewall.
Domain Policy Modification: Group Policy Modification (T1484.001): These scenarios will attempt to force a refresh of a computer’s Group Policy by executing the gpupdate /force command.
Impair Defenses: Disable or Modify Tools (T1562.001): The following modifications are applied by the scenarios:
Disable Windows Defender’s SmartScreen Protection which helps protect against phishing or malware websites and applications, and the downloading of potentially malicious files by modifying the registry value EnableSmartScreen to 0 and the registry value ShellSmartScreenLevel to warn.
Disable Windows Privacy Experience which will prevent the system from sharing information and telemetry with Microsoft by modifying the registry value DisablePrivacyExperience to set the value 1.
Disable Realtime Monitoring functionality of Windows Defender by modifying three registry values to disable Windows Defender from automatically acting against malicious files.
Disable Windows Defender’s SpyNet Capability from submitting suspicious files by setting SubmitSamplesConsent set to 2 and SpynetReporting set to 0.
Impair Defenses: Disable or Modify System Firewall (T1562.004): This scenario modifies the registry value EnableFirewall under the DomainProfile and StandardProfile to the value 0 to disable the local system firewall.
In the last stage, LockBit will check the system’s location to avoid encrypting systems located in friendly geopolitical regions like Russia. LockBit will then make a web request to the adversary’s infrastructure, followed by the deletion of Volume Shadow Copies to remove any backups. Finally, the attack graph will seek to collect and encrypt files on the system by mimicking the ransomware encryption routine.
System Location Discovery (T1614): The scenario executes native API calls GetUserDefaultUILanguage and GetSystemDefaultUILanguage to check the system’s default code page and identify what region the user is located.
Application Layer Protocol: Web Protocols (T1071.001): This scenario emulates the request made by LockBit by making an HTTP POST to an AttackIQ server that mimics the URL format and data sent by a real infection.
Inhibit System Recovery (T1490): Runs vssadmin.exe to delete a recent Volume Shadow Copy created by the attack graph.
Data Encrypted for Impact (T1486): This scenario performs the file encryption routines used by common ransomware families.
Detection and Mitigation Opportunities
With so many different techniques being used by threat actors, it can be difficult to know which to prioritize for prevention and detection assessment. AttackIQ recommends first focusing on the following techniques emulated in our scenarios before moving on to the remaining techniques.
1. Data Encrypted for Impact (T1486)
It should go without saying that as a last resort, preventing your systems and files from being encrypted should be your number one focus. Ensuring that you have the layered endpoint defenses including Antivirus and EDR solutions is critical.
1a. Detection
Ransomware attacks are best prevented and alerted by your EDR/AV Policies. Typically, a configuration for ransomware protection is presented and we strongly encourage that it is enabled in your security controls.
There are three telling signs of ransomware activity in an environment that you could query for and possibly make preventative detections if your security controls allow. Those three are deletion of shadow volumes, suspicious amounts of exfiltrated data, and of course, wide set file encryption.
Detecting deletion of shadow volumes is usually the first step that occurs and can be detected by looking at command line activity:
Via vssadmin.exe:
Process Name == (cmd.exe OR powershell.exe)
Command Line CONTAINS (“vssadmin” AND “Delete Shadows”)
Via PowerShell:
Process Name == powershell.exe
Command Line == “Get-WmiObject Win32_Shadowcopy | ForEach-Object ($_.Delete();)”
Detecting suspicious Data Exfiltration:
Detecting exfiltration is well suited for IDS/IPS and DLP solutions. These products should be configured to identify sensitive files. If sensitive files, or a large amount of web traffic is sent to a rare external IP, it should be detected or prevented depending on security policies for the security control. Historical NetFlow data logging can also bubble up hosts that are experience uncommon peaks in outgoing traffic.
Detecting Ransomware-like File Encryption:
Utilizing an EDR or SIEM/SOAR product can help detect and prevent suspicious file encryption related to ransomware attacks. Utilizing these tools to look for excessive file modifications (greater than 1000 on a system) within less than a minute of time is a good starting indicator. To increase the fidelity a bit, you could include file modification file extension to popular ransomware extensions such as .conti, .Locky, .Ryuk, etc. If possible, with a SOAR or preventative EDR platform, we recommend setting these detections to kill all processes involved in creating the alert as it will most likely stop the spread of the Ransomware.
1b. Mitigation
MITRE ATT&CK Recommends the following mitigations:
2. Create or Modify System Process: Windows Service (T1543.003 )
Actors can create or modify Windows services to repeatedly execute malicious payloads as part of persistence. When Windows boots up, it starts programs or applications called services that perform background system functions. The actors focus on creating services that would only run at Safeboot would also be a behavior not commonly observed.
2a. Detection
Using an EDR or SIEM product, you can create detections to alert when a possibly malicious service has been created due to adversarial behavior.
Process Name = (“cmd.exe” OR “powershell.exe”)
Command Line CONTAINS (“sc” AND “Create”)
2b. Mitigations
MITRE ATT&CK Recommends the following mitigations:
- M1047 – Audit
- M1040 – Behavioral Protection on Endpoint
- M1045 – Code Signing
- M1028 – Operating System Configuration
- M1018 – User Account Management
3. Create Account: Local Account (T1136.001)
The actor will either create a new account or change the password of an existing user. They accomplish this by using the net user utility through the command line.
3a. Detection
With an EDR or SIEM product, you can utilize custom queries and detections to alert when non authorized/ unexpected users attempt to create a user account on the local machine. Although this is a benign windows feature, visibility of users utilizing this feature could lead to earlier detections of malicious entities in your environment.
Process Name = (“cmd.exe” OR “Powershell.exe”)
Command Line CONTAINS (“net user” AND “/add”)
3b. Mitigation
MITRE ATT&CK Recommends the following mitigations:
Wrap-up
In summary, this attack graph will evaluate security and incident response processes and support the improvement of your security control posture against multiple affiliate actors who operate independently but in similar manners. With data generated from continuous testing and use of this attack graph, you can focus your teams on achieving key security outcomes, adjust your security controls, and work to elevate your total security program effectiveness against a known and dangerous threat.
AttackIQ stands at the ready to help security teams implement this attack graph and other aspects of the AttackIQ Security Optimization Platform, including through our co-managed security service, AttackIQ Vanguard.
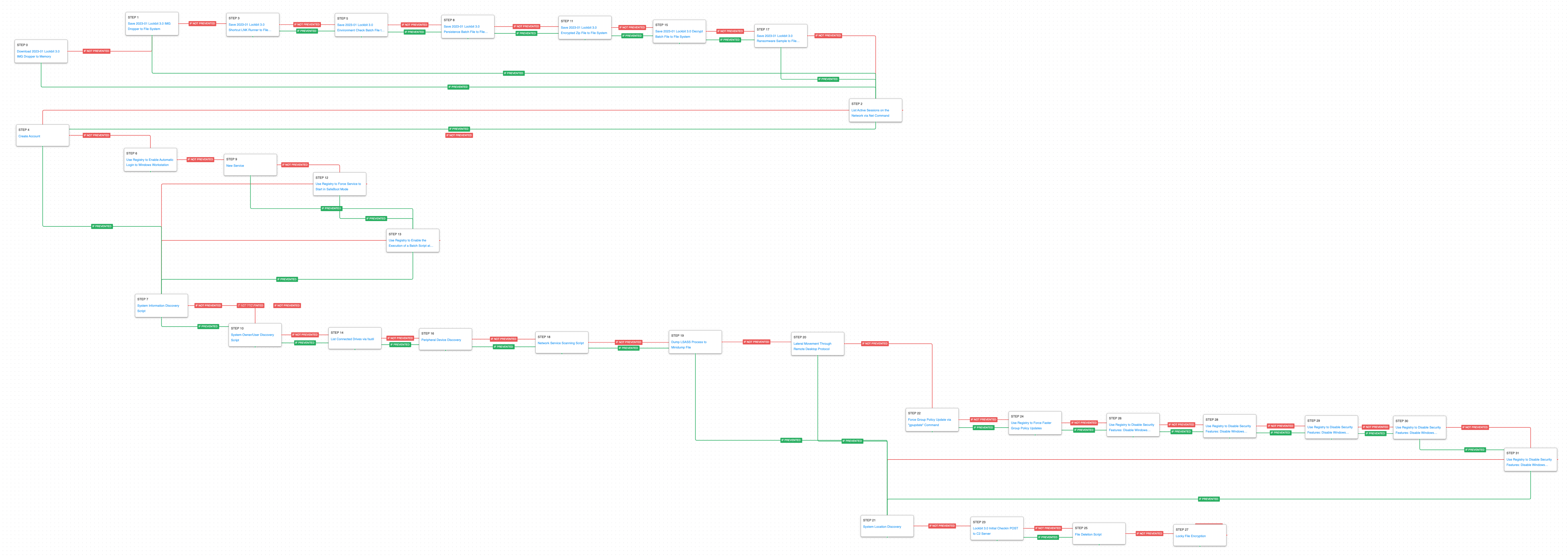 (Click for Larger)
(Click for Larger)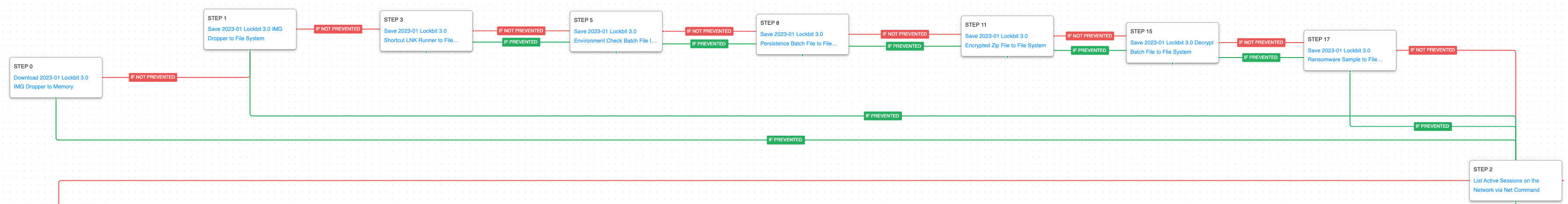 (Click for Larger)
(Click for Larger)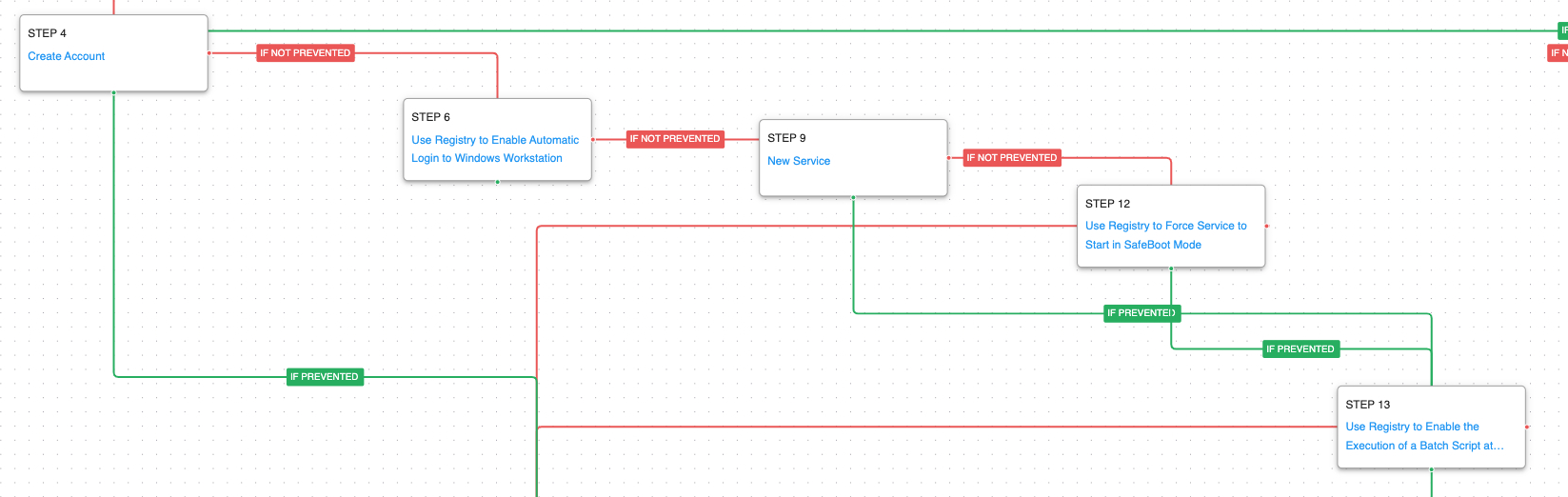 (Click for Larger)
(Click for Larger)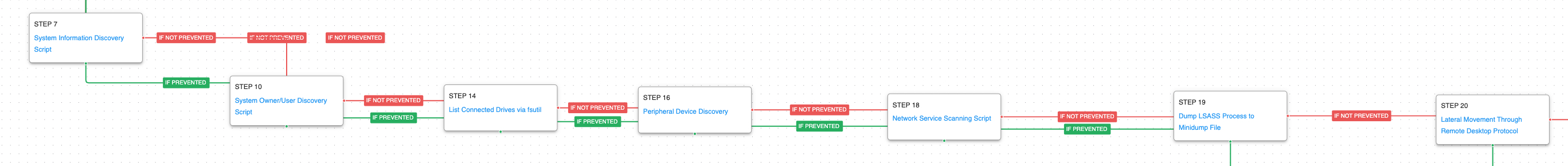 (Click for Larger)
(Click for Larger)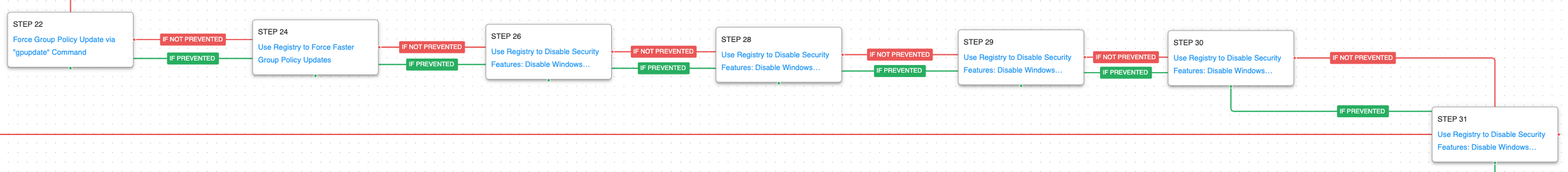 (Click for Larger)
(Click for Larger) (Click for Larger)
(Click for Larger)
