Andariel, also known as Silent Chollima, is a politically motivated adversary of North Korean origin that has been active since at least 2009. Andariel has been reported to operate in support of the Reconnaissance General Bureau (RGB) of the Democratic People’s Republic of Korea (DPRK) and is recognized, along with BlueNoroff, as one of the subgroups of the notorious and widely publicized Lazarus group.
Andariel has shown particular interest in cyberespionage attacks for intelligence gathering against mainly South Korean government agencies and military organizations. During 2018, Andariel was observed using an Active X zero-day against targets in South Korea, by using watering hole attacks on South Korean websites for the purpose of conducting reconnaissance activities during an operation codenamed GoldenAxe.
However, since at least 2021, Andariel has also been seeking financial gain through attacks that leveraged customized ransomware during the final phase of activity. US-CERT released at joint FBI, CISA, and Department of the Treasury alert in July 2022 detailing historical attacks against U.S.-based Healthcare and Public Health (HPH) organizations through the Maui ransomware.
AttackIQ has released three new attack graphs emulating the actor’s historical campaigns to help customers validate their security controls and their ability to defend against this group. Validating your security program performance against these behaviors is vital in reducing risk. By using these new attack graphs in the AttackIQ Security Optimization Platform, security teams will be able to:
- Evaluate security control performance against an actor with both financial and political motivations.
- Assess their security posture against a threat actor who isn’t afraid to commit to destruction actions.
- Continuously validate detection and prevention pipelines against another subset of North Korean actors who share successful techniques with other regional threat groups.
Andariel – 2021-04 – Ransomware Campaign against South Korea
This first attack graph describes a multi-stage campaign against South Korea reported by SecureList and MalwareBytes in April 2021, culminating in the deployment of custom ransomware.
The attack graph begins with the downloading and saving of the different stages of the actor’s malware. First Andariel uses a malicious access file which then downloads and executes a remote payload using Mshta. Finally, the next payload is downloaded and saved before attempting to communicate with the adversary’s infrastructure and obtaining persistence through the Startup folder and staging files of interest.
Ingress Tool Transfer (T1105): This scenario downloads to memory and saves to disk in independent scenarios to test both network and endpoint controls and their ability to prevent the delivery of known malicious Andariel samples.
System Binary Proxy Execution: Mshta (T1218.010): Mshta.exe is a native Windows utility that threat actors can abuse to download remote payloads that include VBScript code.
Application Layer Protocol: Web Protocols (T1071.001): Andariel’s Simple Agent malware uses HTTP for command-and-control traffic. This scenario makes the initial HTTP POST request to an AttackIQ controlled server emulating the exact web request made by a true Simple Agent infection.
Logon Autostart Execution: Startup Folder (T1547.001): The Startup folder is a directory associated with the Windows Start Menu that can be used to launch a process at Windows logon. This scenario creates a binary file in this directory that would execute at next logon for users.
Local Data Staging (T1074.001): A batch file is executed looking for any office files found in the Users directory and copies any matching files to a staged directory in a temporary folder.
In the second stage, a variant of the Akdoor malware is downloaded and saved on the system, which will be executed via RunDLL32. The actor will then seek to discover information about files and directories, and disk information.
System Binary Proxy Execution: Rundll32 (T1218.011): RunDll32 is a native system utility that can be used to execute DLL files and call a specific export inside the file. This scenario executes RunDll32 with an AttackIQ DLL and calls an export to mimic previously reported malicious activity.
File and Directory Discovery (T1083): This scenario uses the native dir command to find files of interest and output to a temporary file.
System Information Discovery (T1082): Windows Management Instrumentation (WMI) commands like logicaldisk and diskdrive are executed to collect details on the system’s disk drives.
Finally, in the last stage, a sample of the Maui ransomware will be downloaded and saved, which will collect and encrypt files present on the system.
Data Encrypted for Impact (T1486): This scenario performs the file encryption routines used by common ransomware families. Files matching an extension list are identified and encrypted in place using the same encryption algorithms observed in the Maui ransomware family.
Andariel – 2021-04 – Maui Ransomware Campaign
The second attack graph details a Kaspersky report which is a response to the US-CERT Alert AA22-187A “North Korean State-Sponsored Cyber Actors Use Maui Ransomware to Target the Healthcare and Public Health Sector”. During these attacks, Andariel deployed their DTrack malware and the Maui ransomware against targets located primarily in Japan, India, Russia, and Vietnam.
The attack graph starts with a BITS Jobs, which is used for downloading and executing the DTrack malware. Next, the attack graph will seek to emulate the information discovery phase of the attack focused on the collection of running process, system networking configuration.
BITS Jobs (T1197): Background Intelligent Transfer Service (BITS) is a native mechanism used by legitimate applications to use a system’s idle bandwidth to retrieve files without disrupting other applications. Commands are executed using bitsadmin to create a BITS job and configure it to download a remote payload.
Process Discovery (T1057): From a command window the tasklist command is run to download a list of all running processes.
System Network Configuration Discovery (T1016): The network configuration of the asset is collected using standard Windows utilities like ipconfig, arp, route, nltest, and netsh.
System Network Connections Discovery (T1049): The native Windows command line tool netstat is used to collect active connections and any listening services running on the host.
Internet Connection Discovery (T1016.001): This scenario uses the ping command to determine outbound access to the internet by attempting to reach Google’s public DNS servers.
In its last stage, the actor will stage their collected information to prepare for its subsequent exfiltration. Finally, the Maui ransomware will be downloaded and saved, which then attempts to encrypt files of interest.
Browser Bookmark Discovery (T1217): This scenario implements through a PowerShell script the technique in which an attacker enumerates browser bookmarks to gain information about the hosts and their users using the Get-Content command.
Exfiltration Over C2 Channel (T1041): Files are sent to an AttackIQ controlled server using HTTP POST requests.
Andariel – 2021-09 – Operation ByteTiger
The last attack graph is based on the Operation ByteTiger report by the Korean CERT (KrCERT) in September 2021, which is based on a series of attacks against South Korean entities using two pieces of malware named TigerDownloader and TigerRAT.
The actor starts with the delivery of a remote payload using MSHTA, a native Windows utility capable of executing JavaScript and VBScript code. The TigerDownloader malware seeks to execute multiple discovery techniques and ends with a communication to the adversary’s infrastructure and subsequent download and execution of the next and last stage of the attack. Andariel begins the discovery phase of their attack by gathering information on the infected system.
System Information Discovery (T1082): The native systeminfo command is executed to retrieve all the Windows system information.
Peripheral Device Discovery (T1120): The fsutil command is executed to list connected drives on the system.
In the last stage, TigerRAT is downloaded and saved on the system, which seeks to evade defenses by masquerading as legitimate system processes and obtain persistence either through a scheduled task or Registry Run Keys.
Masquerading: Match Legitimate Name or Location (T1036.005): Execute an AttackIQ executable using the name of a legitimate Microsoft application.
Scheduled Task/Job: Scheduled Task (T1053.005): This scenario creates a new scheduled task using the schtasks utility.
Registry Run Keys (T1547.001): Windows has many registry keys that identify applications or commands to be run at startup.
System Owner/User Discovery (T1033): Executes the native query user and whoami commands to receive details of the running user account.
Query Registry (T1012): The HKCU\Software\Microsoft\Windows\CurrentVersion registry key contains information about Windows properties for the user accessing that registry key.
Detection and Mitigation Opportunities
With so many different techniques being used by threat actors, it can be difficult to know which to prioritize for prevention and detection assessment. AttackIQ recommends first focusing on the following techniques emulated in our scenarios before moving on to the remaining techniques.
1. Ingress Tool Transfer (T1105)
Andariel, like other North Korean groups, heavily leverage different stages of malware in both the initial compromise and post compromise stages of their attacks. Endpoint and Network security controls should both be employed to try and detect the delivery of these malicious payloads.
1a. Detection
The following signatures can help identify when native utilities are being used to download malicious payloads.
PowerShell Example:
Process Name == (Cmd.exe OR Powershell.exe)
Command Line CONTAINS ((“IWR” OR “Invoke-WebRequest") AND “DownloadData” AND “Hidden”)
certutil Example:
Process Name == Certutil.exe
Command Line Contains (“-urlcache” AND “-f” AND “http”)
Bitsadmin Example:
Process Name == Bitsadmin.exe
Command Line CONTAINS (“/transfer” AND “http”)
Curl Example:
Process Name == Curl.exe
Command Line CONTAINS (“http” AND “-o”)
1b. Mitigation
MITRE ATT&CK has the following mitigation recommendations
2. System Binary Proxy Execution: Mshta (T1218.010)
MSHTA is a native Windows tool that can either be used to open .hta files directly or be passed a URL in the command line arguments to download and execute a remote file. This tactic is very commonly used as part of a phishing attack where either the Mshta.exe process is executed as part of Office macros or a Shortcut .lnk file.
2a. Detection
The following pseudo-signature can help detect abuse of the MSHTA process.
Process Name == mshta.exe
Command Line CONTAINS (“http” OR “vbscript” OR “jscript”)
Process Name == Mshta.exe
Parent Process Name CONTAINS (“word” OR “excel” OR “powerpoint”)
2b. Mitigation
MITRE ATT&CK has the following mitigation recommendations for <Technique>
3. Data Encrypted for Impact (T1486)
It should go without saying that as a last resort, preventing your systems and files from being encrypted should be your number one focus. Ensuring that you have the layered endpoint defenses including Antivirus and EDR solutions is critical.
3a. Detection
Ransomware attacks are best prevented and alerted by your EDR/AV Policies. Typically, a configuration for ransomware protection is presented and we strongly encourage that it is enabled in your security controls.
There are three telling signs of ransomware activity in an environment that you could query for and possibly make preventative detections if your security controls allow. Those three are deletion of shadow volumes, suspicious amounts of exfiltrated data, and of course, wide set file encryption.
Detecting deletion of shadow volumes is usually the first step that occurs and can be detected by looking at command line activity:
Via vssadmin.exe:
Process Name == (cmd.exe OR powershell.exe)
Command Line CONTAINS (“vssadmin” AND “Delete Shadows”)
Via PowerShell:
Process Name == powershell.exe
Command Line == “Get-WmiObject Win32_Shadowcopy | ForEach-Object ($_.Delete();)”
Detecting suspicious Data Exfiltration:
Detecting exfiltration is well suited for IDS/IPS and DLP solutions. These products should be configured to identify sensitive files. If sensitive files, or a large amount of web traffic is sent to a rare external IP, it should be detected or prevented depending on security policies for the security control. Historical NetFlow data logging can also bubble up hosts that are experience uncommon peaks in outgoing traffic.
Detecting Ransomware-like File Encryption:
Utilizing an EDR or SIEM/SOAR product can help detect and prevent suspicious file encryption related to ransomware attacks. Utilizing these tools to look for excessive file modifications (greater than 1000 on a system) within less than a minute of time is a good starting indicator. To increase the fidelity a bit, you could include file modification file extension to popular ransomware extensions such as .conti, .Locky, .Ryuk, etc. If possible, with a SOAR or preventative EDR platform, we recommend setting these detections to kill all processes involved in creating the alert as it will most likely stop the spread of the Ransomware.
3b. Mitigation
MITRE ATT&CK has the following mitigation recommendations for <Technique>
Wrap-up
In summary, this attack graph will evaluate security and incident response processes and support the improvement of your security control posture against another North Korean threat actor who isn’t afraid to destroy your data. With data generated from continuous testing and use of these attack graphs, you can focus your teams on achieving key security outcomes, adjust your security controls, and work to elevate your total security program effectiveness against a known and dangerous threat.
AttackIQ stands at the ready to help security teams implement this attack graph and other aspects of the AttackIQ Security Optimization Platform, including through our co-managed security service, AttackIQ Vanguard.
 (Click for Larger)
(Click for Larger)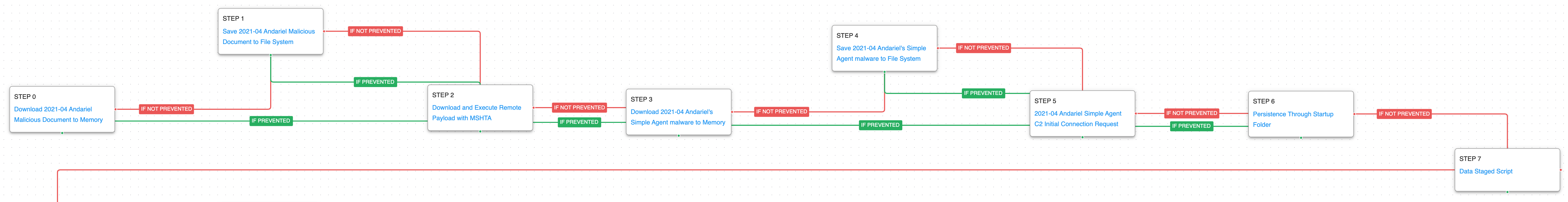 (Click for Larger)
(Click for Larger) (Click for Larger)
(Click for Larger) (Click for Larger)
(Click for Larger)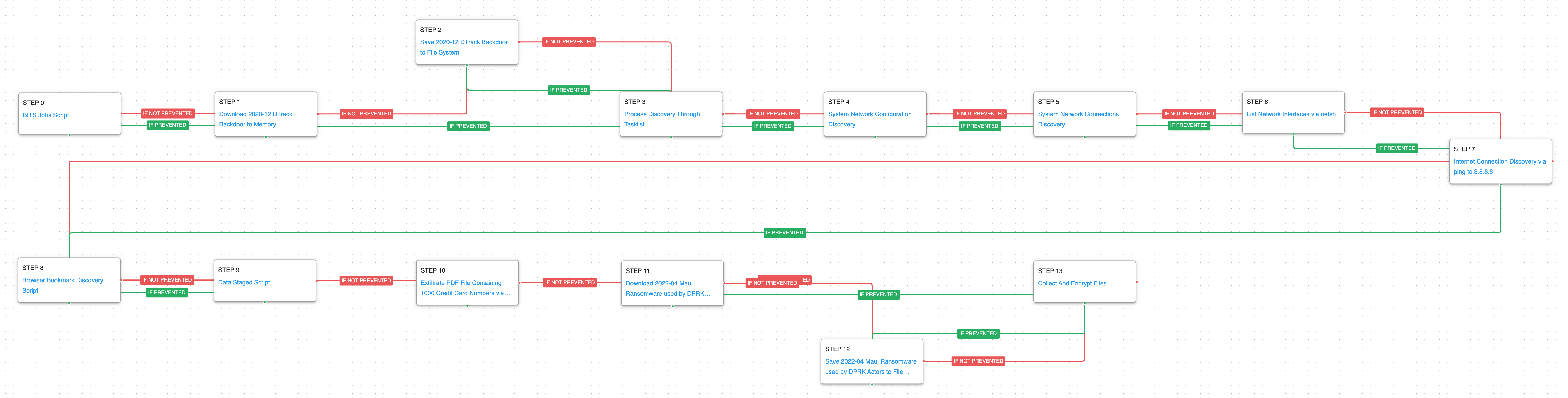 (Click for Larger)
(Click for Larger) (Click for Larger)
(Click for Larger) (Click for Larger)
(Click for Larger) (Click for Larger)
(Click for Larger) (Click for Larger)
(Click for Larger) (Click for Larger)
(Click for Larger)
