Breach and Attack Simulation
September 7, 2023
The rise of remote work, branch networks, and the entwining of IoT and OT systems have created vast network footprints, making identifying vulnerabilities more challenging than ever. Cyber threats loom large, and with the stakes higher than ever, ensuring your defenses are impervious is paramount.
August 23, 2023
The implications of not conducting security control testing are profound. Adversaries are relentless and will exploit vulnerabilities if given the chance. The potential impact includes data breaches, financial losses, damage to reputation, and regulatory penalties.
August 3, 2023
AttackIQ has helped hundreds of companies across the global 2000 to conduct automated testing at scale, powered by MITRE ATT&CK. Building on a decade of success, we are now making testing available for everyone. Here’s what that means.
July 10, 2023
AttackIQ has released a new attack graph in response to the recently published CISA Advisory (AA23-187A) that seeks to emulate the activities carried out by the financially motivated and highly sophisticated criminal adversary known as TA505.
May 10, 2023
AttackIQ has released two new attack graphs in response to the recently published CISA Advisory (AA23-129A) that details the efforts taken by U.S. agencies to disrupt the peer-to-peer network infrastructure used by the Russian threat actor Turla and their Snake malware. Turla is the public name given to actors associated with cyberattacks conducted by Center 16 of Russia’s Federal Security Service (FSB).
February 14, 2023
AttackIQ is democratiziing the practice of threat-informed defense and adversary emulation, including by funding research from the Center for Threat-Informed Defense on micro-emulation planning. Learn more out how we put adversary emulation into practice in the AttackIQ Security Optimization Platform.
December 13, 2022
OpenAI’s ChatGPT can tell you exactly how to use BAS to improve your cyberdefense effectiveness. But it won’t help you with the Russian military specifically, and that’s a very good thing. See below for why OpenAI deserves credit for this algorithmic limit.
December 12, 2022
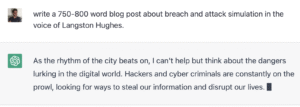
We asked OpenAI’s ChaptGPT to write a 750-800 word blog post about breach and attack simulation (BAS) in the voice of Langston Hughes. It did great; see below. And well-done, team OpenAI.
December 8, 2022
A look back at how AttackIQ’s customers and advanced research, as well as key players in the analyst community, helped propel the breach and attack simulation market forward in 2022.
September 23, 2022
AttackIQ has released a new fully featured attack graph that emulates the tactics, techniques, and procedures (TTPs) used by Iranian nation-state adversaries against the government of Albania.
September 21, 2022
AttackIQ has released a content bundle including two new attack graphs covering two historical APT28 campaigns involving their SkinnyBoy and Zebrocy malware families and standalone scenarios emulating command-and-control traffic to test boundary controls.
August 11, 2022
AttackIQ’s Adversary Research Team has released a new assessment to test endpoint and network controls’ ability to prevent Zeppelin Ransomware.
July 29, 2022
In this guest blog post, Bradley Schaufenbuel of Paychex writes about how security teams can leverage the MITRE ATT&CK framework to mount a “threat-informed” defense. This post originally appeared as an article in SC Magazine.
July 11, 2022
AttackIQ has released two new attack graphs that emulate different aspects of OilRig’s operations against multiple sectors around the globe. With these attack graphs, you can test and validate your defenses to improve cybersecurity readiness.
June 28, 2022
AttackIQ has released two new fully featured attack graphs emulating the tactics, techniques, and procedures (TTPs) used by likely nation-state adversaries that continue exploiting the Log4Shell vulnerability in VMware Horizon Systems.
June 3, 2022
AttackIQ has released a new fully featured attack graph emulating the tactics, techniques, and procedures used by the Karakurt Data Extortion Group recently reported in US-CERT Alert AA22-152.
May 25, 2022
Why adopt purple teaming? This IDC analyst brief explains how blending red and blue mindsets helps you holistically prepare for cyberattacks.
April 29, 2022
Uncover new attacks from a threat actor likely operating out of Belarus known as UNC1151 or Ghostwriter.
April 1, 2022
AttackIQ has released a new attack graph for organizations to test and validate their cyberdefense effectiveness against the HAVEX strain of malware. This attack graph follows a pair of Department of Justice indictments of Russia-based threat actors and a new joint FBI-CISA Cybersecurity Advisory about HAVEX released last week. An enduring and dangerous threat, HAVEX targeted the energy and power sectors in 135 countries from 2012-2018, and the tactics and techniques within it continue to threaten organizations today.
March 29, 2022
Following an up-tick in the activity of Russia-based cyberthreat actors, this blog discusses the practical steps you can take to validate your network security controls against known Russian tactics, techniques, and procedures to improve your security readiness. It walks readers through Russia-specific emulations included in the AttackIQ Network Control Validation module.
March 11, 2022
AttackIQ and the Center for Threat-Informed Defense are furthering the art of adversary emulation with the Center’s new Attack Flow project. Building on our deep research partnership with the Center, AttackIQ’s Attack Graphs emulate the adversary with specificity and realism to test advanced cyberdefense technologies against multi-stage attacks. Read on for more.
March 8, 2022
To prepare for a potential cyberattack from Russia-based actors, you can begin by testing your security controls against known adversary tactics. The vast majority of cyberattacks use tactics and techniques that have been employed in the past. This blog walks you through key known tactics and techniques, and highlights scenarios in the AttackIQ Security Optimization Platform that you can use today to test your defenses and improve your cybersecurity readiness.
June 24, 2021
This past week, AttackIQ launched its inaugural Purple Hats Conference—where more than 3,000 cybersecurity practitioners, partners, and pros joined to collaborate, share ideas, and learn how to evolve from a reactive to proactive threat informed defense strategy.