Targeted Sectors: Education, Small Business, Media, Critical Infrastructure, Government, Financial Services, Manufacturing, and Communications
On May 9, 2023, the Cybersecurity and Infrastructure Security Agency (CISA) released a joint Cybersecurity Advisory (CSA) detailing the efforts taken by U.S. and partner agencies to disrupt the peer-to-peer network infrastructure used by the Russian threat actor Turla and their Snake malware. Turla is the public alias given to the actors associated with cyberattacks conducted by Center 16 of Russia’s Federal Security Service (FSB).
Turla has leveraged a custom malware implant, known publicly as Snake, since 2003 to compromise victims across the globe to facilitate the theft of international relations documents and diplomatic communications from NATO countries. The malware was used to infect hosts across more than 50 countries including U.S.-based institutions in the education, small businesses, media, government, financial, critical manufacturing, and communication sectors.
Infected hosts operated as a peer-to-peer (P2P) network that allowed for redundant and proxied control of victims from multiple avenues. The Federal Bureau of Investigation (FBI) spent years analyzing the malware and network communications before being able to develop their own tool, Perseus, that was able to exploit weaknesses in the malware’s authentication process to issue shutdown commands to all the infected hosts.
While the threat from Snake has been (temporarily) neutralized, it is not the only tool in Turla’s arsenal. Researchers at Mandiant published a report in January 2023 detailing compromises made against targets located in Ukraine using an old commodity stager known as ANDROMEDA, which was widely popular in the early 2010s. During this activity, Turla was observed re-registering several expired ANDROMEDA C2 domains and identifying victims to selectively deploy the JavaScript-based reconnaissance utility known as KOPILUWAK with the purpose of facilitating C2 communications and victim profiling. Once profiling of compromised systems is complete, Turla deploys QUIETCANARY, a lightweight .NET backdoor used primarily to collect and extract files of interest.
AttackIQ has released two new attack graphs emulating the capabilities of Snake and Turla’s additional malware families to help customers validate their security controls and their ability to defend against one of the most prolific and advanced Russian threat actors.
Validating your security program performance against these behaviors is vital to reducing risk. By using these new attack graph(s) in the AttackIQ Security Optimization Platform, security teams will be able to:
- Evaluate security control performance against an actor with two decades of experience in remaining stealthily entrenched in victim environments.
- Assess their security posture against multiple paths of success that Turla has used to be successful.
- Continuously validate detection and prevention pipelines against one of the main cyber-arms of Russia’s intelligence services.
[CISA AA23-129A] Turla – Hunting Russian Intelligence “Snake” Malware
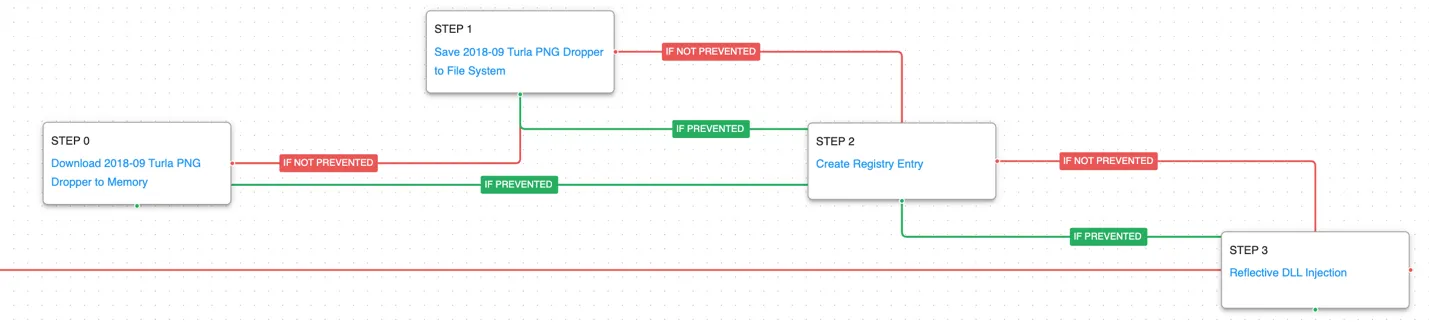
This first graph covers the overall capabilities of Turla’s Snake malware. It begins with the dropping of their PNG Dropper which decrypts and loads the Snake payload into memory. The malware offers the ability for the actors to perform many hands-on keyboard activities to discover more about the infected environment. The final stage of the attack graph allows for the loading of additional payloads that would be delivered through Snake’s HTTP communications.
The first stage downloads and saves the PNG dropper. Encrypted data is written to registry keys that will be accessed by later stages to load configuration settings. The Snake payload is decoded from embedded resources before being injected into the existing process.
Ingress Tool Transfer (T1105): This scenario downloads to memory and saves to disk in independent scenarios to test both network and endpoint controls and their ability to prevent the delivery of known malicious files.
Modify Registry (T1112): This scenario sets the same registry key’s used by Snake to configure future encryption settings.
Reflective DLL Injection (T1620): This scenario takes a default AttackIQ DLL and loads it into the memory space of its own process in order to execute the desired DLL function.
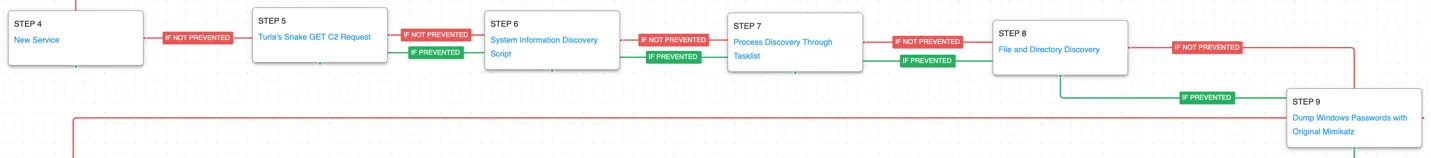
The malware establishes persistence using a new service before making an initial command and control request to the actor’s infrastructure to register the new infection. The actor then has the capability to begin executing discovery commands to learn more about the infected host by querying details about the system information, the running processes, and its file contents. Additionally, Snake has the capability to dump additional credentials that could later be used to expand their reach into the victim’s network.
Windows Service (T1543.003): Use the native sc command line tool to create a new service that will be executed at next reboot.
Application Layer Protocol: Web Protocols (T1071.001): This scenario emulates the HTTP requests made by Snake by making an HTTP GET to an AttackIQ server that mimics the cookie format and data sent by a real infection.
System Information Discovery (T1082): The native hostname and systeminfo commands are used to get the infected host’s computer name and basic details about the system.
Process Discovery (T1057): Window’s built-in tasklist command is executed as a command process and the results are saved to a file in a temporary location.
File and Directory Discovery (T1083): This scenario uses the native dir command to find files of interest and output to a temporary file.
OS Credential Dumping (T1003): Uses the open-source tool Mimikatz to dump passwords and hashes for Windows accounts.
Armed with the information about the initially infected foothold, Snake can begin to learn more about the network configuration and identify additional systems of interest. Snake heavily utilizes a rootkit capability and uses named pipes to communicate between its user and system components.
Network Sniffing (T1040): One of the methods Snake uses to receive commands is to install a driver that allows for the sniffing of packets. The malware can then intercept commands sent to the box using the same ports and protocols normally used by the other listening services on the host. This scenario uses the native Windows pktmon utility to capture incoming and outgoing packets.
Network Service Discovery (T1046): This scenario uses nmap for scanning hosts that are open on ports 139, 445, and 3389 that would identify remotely accessible hosts to the attacker.
Domain Trust Discovery (T1482): PowerView is used to replace Window’s net commands that enumerate details on the connected domain and forests of the infected host.
Inter-Process Communication (T1559): This scenario uses PowerShell and a Windows service to create, listen, and send data over a named pipe.
The final stage is focused on Snake’s multiple capabilities to execute additional payloads. Additional data is staged and exfiltrated over HTTP POST requests.
Process Injection (T1055): This scenario injects a DLL file into another running process and validates if a canary file can be created.
System Binary Proxy Execution: InstallUtil (T1218.004): Compiles and executes an executable using the native Windows utility csc.exe.
Hijack Execution Flow: DLL Side-Loading (T1547.002): Bundles a DLL with a Windows executable that is susceptible to DLL Side-Loading to execute actor code.
Data Staged: Local Data Staging (T1074.001): Files are collected and stored in a temporary directory so they can be exfiltrated later.
Exfiltration Over C2 Channel (T1041): Files are sent to an AttackIQ controlled server using HTTP POST requests.
Turla – 2023-01 – Reconnaissance Campaign Against Entities and Individuals in Ukraine
The second attack graph covers a full-scale compromise from Turla using a combination of their different malware families. These techniques were taken from a Mandiant report detailing a compromise of Ukrainian organizations. The final goal is the same, identify files of interest and exfiltrate back to the actor’s infrastructure.
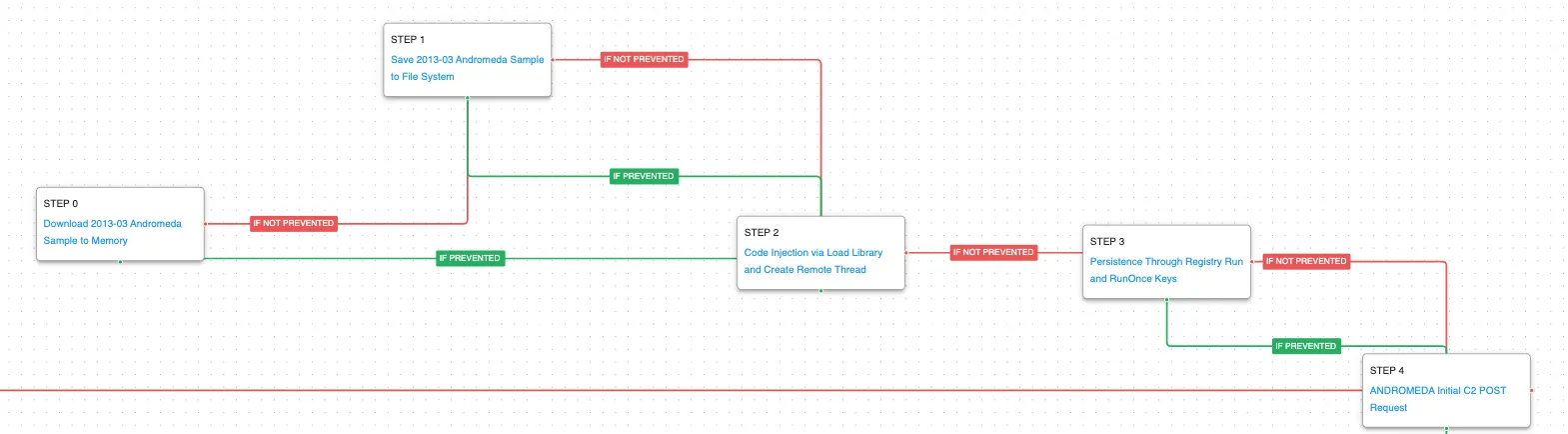
The first stage covers the deployed of the commodify cyber-crime malware ANDROMEDA. This malware from 2013 was likely infected from a thumb drive and when executed, its malicious capabilities are injected into another running process. ANDROMEDA sets persistence using a registry key and then makes network requests to the actor’s infrastructure to receive additional payloads.
Logon Autostart Execution: Registry Run Keys (T1547.001): This scenario sets the HKLM\Software\Microsoft\Windows\CurrentVersion\Run registry key that Windows uses to identify what applications should be run at system startup.
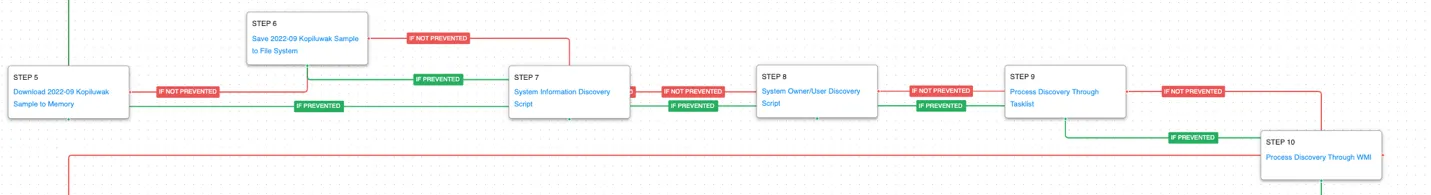
After hijacking the legacy command and control server, the actor deploys their own custom malware KOPILUWAK that is used to perform all the initial profiling actions that will highlight targets of interest.
System Owner/User Discovery (T1033): query user and whoami are called to determine what account is the webshell currently operating under.
Process Discovery (T1057): WMIC is used to get a list of running processes on the host.
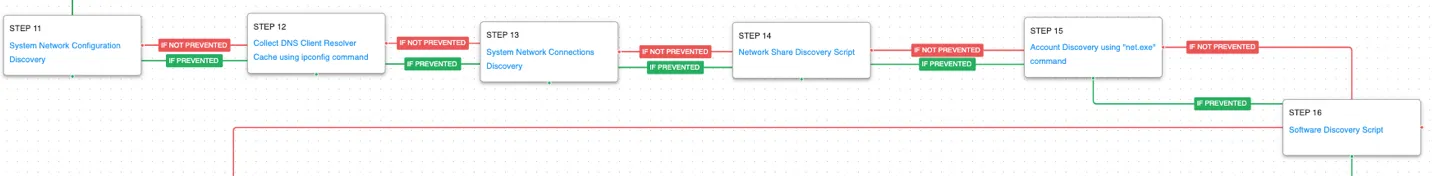
KOPILUWAK has additional network discovery capabilities looking for details about the system’s network configuration and other potential remote resources that could be accessible.
System Network Configuration Discovery (T1016): The network configuration of the asset is collected using standard Windows utilities like ipconfig, arp, route, and nltest.
System Network Connections Discovery (T1049): The native Windows command line tool netstat is used to collect active connections and any listening services running on the host.
Network Share Discovery (T1135): The native net tools are used to list all of the local mapped network shares with net share.
Account Discovery: Local Account (T1087.001): A list of local accounts configured on this host is collected by executing the net user command. Knowing what other accounts are present on the host will allow the actor to potentially re-use previously known credentials or identify disabled legitimate accounts they can re-enable to blend in with everyday activity.
Software Discovery (T1518): A registry key containing entries for all the software installed on the victim asset. Reg.exe is used to access HKLM\Software\Microsoft\Windows\CurrentVersion\Uninstall.
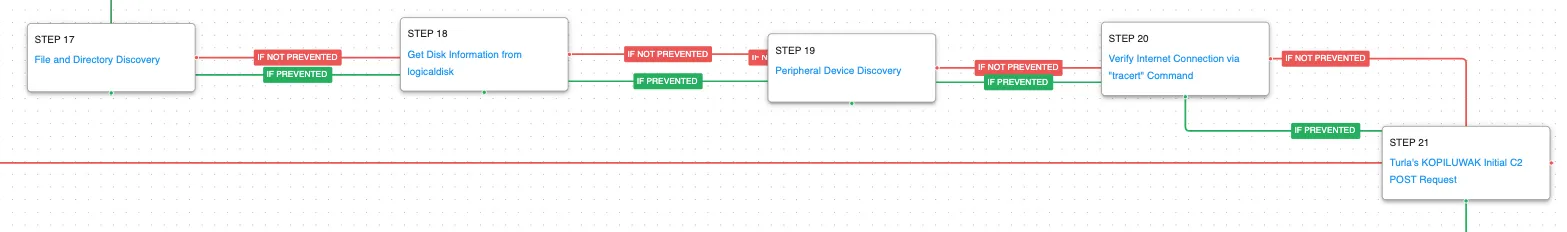
The malware continues in torrent of automated discovery actions by getting file and disk information along with details about connected peripheral devices. Finally, external network connectivity is tested before making an initial request to the command-and-control server to receive the actor’s final payload.
Windows Management Instrumentation (WMI) (T1047): WMI is a native Windows administration feature that provides a method for accessing Windows system components. These two scenarios execute the logicaldisk and diskdrive commands to retrieve details on the system’s disks.
Peripheral Device Discovery (T1120): This scenario retrieves information about systems peripherals such as logical drives, physical memory, and network cards through the execution of commands and binaries.
Internet Connection Discovery (T1016.001): This scenario uses tracert to check connectivity to Google’s external DNS (8.8.8.8). The actors utilize this command to determine if they will be able to potentially gain outbound unrestricted access to the internet.
The final stage of the attack graph is the delivery of the actor’s final payload, QUIETCANARY. This malware is focused on data exfiltration of sensitive data using similar techniques described in the Snake attack graph.
Detection and Mitigation Opportunities
With so many different techniques being used by threat actors, it can be difficult to know which to prioritize for prevention and detection assessment. AttackIQ recommends first focusing on the following techniques emulated in our scenarios before moving on to the remaining techniques.
1. Review CISA’s Detection and Hunting Recommendations
Turla leverages a rootkit with their Snake infections that makes detection and identification of Snake compromises very difficult. CISA has provided a significant number of detection signatures and hunting queries that could be used to identify victims of Snake compromises.
AttackIQ highly recommends reviewing their signatures and adapting to your environment first to see if you have any existing impact before reviewing the results from the attack graphs.
2. Process Injection (T1055)
Turla uses both reflective and remote process injection to hide their malicious code in other processes. This allows them to hide behind legitimate executables to masquerade their activities.
2a. Detection
Searching for common processes that are performing uncommon actions can help identify when a process has been compromised. Looking for standard Windows discovery commands would not normally be executed by legitimate processes. You can look for similar activity using a signature like:
Parent Process Name == svchost.exe
Command Line CONTAINS (‘set’ OR ‘whoami’ OR ‘ping’ OR ‘dir’)
2b. Mitigation
3. Windows Service (T1543.003)
Actors can create or modify Windows services to repeatedly execute malicious payloads as part of persistence. When Windows boots up, it starts programs or applications called services that perform background system functions.
3a. Detection
The following rules can help identify when that persistence mechanism is being set.
Process Name == (Cmd.exe OR Powershell.exe)
Command Line CONTAINS (‘sc’ AND ‘create’ AND ‘start= “auto”’)
3b. Mitigation
MITRE ATT&CK has the following mitigation recommendations:
Wrap-up
In summary, this attack graph will evaluate security and incident response processes and support the improvement of your security control posture against one of the top threat actors in the world. With data generated from continuous testing and use of these attack graphs, you can focus your teams on achieving key security outcomes, adjust your security controls, and work to elevate your total security program effectiveness against a known and dangerous threat.
AttackIQ stands at the ready to help security teams implement this attack graph and other aspects of the AttackIQ Security Optimization Platform, including through our fully managed service, AttackIQ Ready!, and our co-managed security service, AttackIQ Vanguard.