On October 4, 2022, the Cybersecurity and Infrastructure Security Agency (CISA) published a joint Cybersecurity Advisory (CSA) with the FBI and the NSA detailing the tactics, techniques, and procedures (TTPs) used by multiple Chinese-sponsored threat actors during their attack against a Defense Industrial Base (DIB) organization.
The alert details activity from what they believe is likely multiple advanced persistent threat (APT) actors who first compromised the victim in January 2021. The initial access vector is unknown, but the actors first gained access to the organization’s Microsoft Exchange Server where they gathered information about the Exchange environment and performed mailbox searches for sensitive information.
The following month, actors began accessing Exchange Web Services with compromised credentials while connecting from commercial VPN providers. The actors also expanded their access and began exploring the victim’s network using native command shell applications and started to harvest data for exfiltration. They also began using the open-source Python toolkit Impacket to move laterally and execute commands against other remote systems.
In March, the actors continued to extend their access by exploiting other Microsoft Exchange vulnerabilities which allowed them to drop China Chopper webshells and later a bespoke backdoor known as HyperBro. Finally, in July the actors deployed a new custom exfiltration tool called CovalentStealer which was used to exfiltrate the remaining sensitive files to OneDrive.
While the alert doesn’t attribute the activity directly to any specific actors or country of origin, the tactics and malware used in the attack clearly point to Chinese-sponsored threat groups. The Exchange vulnerabilities were first discovered and used by the Chinese threat actor Hafnium but were later adopted by many other groups. The HyperBro backdoor has been exclusively used by Chinese threat actors and specifically attributed to APT27 / Iron Tiger / Emissary Panda. This threat actor has a long historical record of targeting U.S.-based DIB companies and has been focused on the Middle East and North Africa (MENA) region in the last couple of years.
These attacks could be the start of a renewed interest in economical focused cyber espionage by Chinese threat actors against U.S. companies that had significantly decreased since the Cyber Agreement signed by then U.S. President Barack Obama and Chinese Premier Xi Jinping. AttackIQ has released a new fully featured attack graph that emulates the TTPs described in this alert to help our customers protect themselves against these threat actors.
Validating your security program performance against AttackIQ’s new attack graph is paramount in reducing risk. By using the AttackIQ Security Optimization Platform, security teams will be able to:
- Evaluate security control performance against common living-off-the-land discovery techniques abused by many different threat actors.
- Assess their security posture against a threat actor with a long successful record of stealing sensitive information.
- Continuously validate detection and prevention pipelines beyond the multitude of initial access exploits used by actors.
[US-CERT AA22-277A] Chinese Threat Actors Steal Sensitive Information from DIB Organization
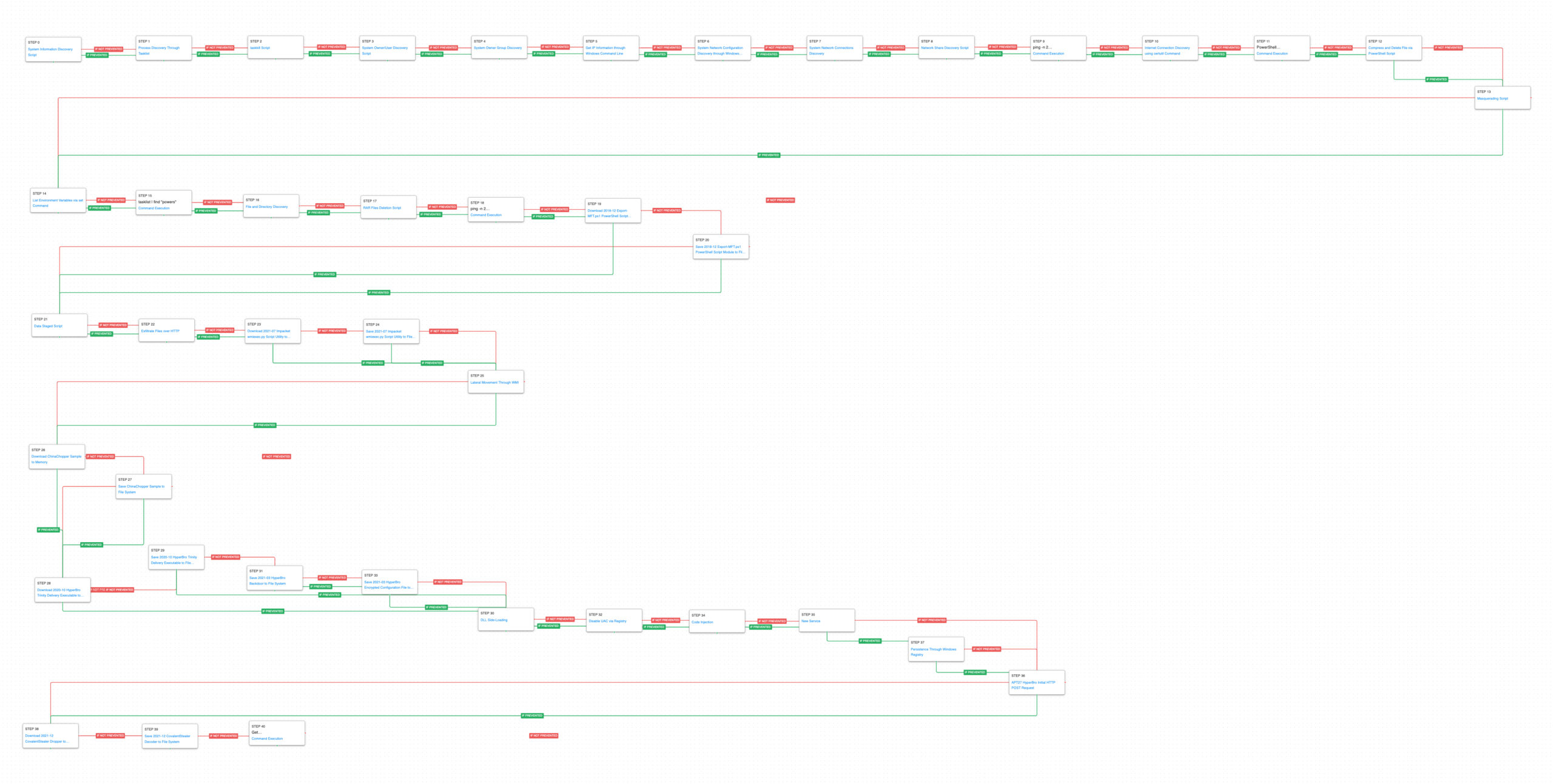
Our attack graph begins after an unknown initial compromise method and starts with the execution of discovery commands. The threat actor used native built-in tools and commands to begin to learn about the compromised host. Information about the system’s configuration, running processes, currently logged in user, and administrative groups was first collected.
System Information Discovery (T1082): The native hostname and systeminfo commands are used to get the infected host’s computer name and basic details about the system.
Process Discovery (T1057): Window’s built-in tasklist command is executed as a command process and the results are saved to a file in a temporary location.
Impair Defenses: Disable or Modify Tools (T1562.001): taskkill is executed and passed a Process ID to stop a running process. The actors used this to disable a security tool running on the Exchange server.
System Owner/User Discovery (T1033): query user and whoami are called to determine what account is the webshell currently operating under.
Permission Groups Discovery: Local Groups (T1069.001): The actor is interested in finding out the memberships of privileged local groups like Remote Desktop Users and Local Administrators. They accomplish this by executing net localgroup lookups.
After learning about the infected host, the actor needs to gather information about the network of the compromised asset. Collecting details about the network adapters, open network connections, and any available network shares will arm the threat actor with the data required to begin moving laterally and discovering additional targets of interest.
System Network Configuration Discovery (T1016): The network configuration of the asset is collected using standard Windows utilities like ipconfig, arp, route, and nltest.
System Network Connections Discovery (T1049): Using netstat the actors are able to get a list of remote connections established to and from the infected asset.
Network Share Discovery (T1135): The native net tools are used to list all of the local mapped network shares with net share.
Prior to moving laterally, the adversaries needed to evaluate if they could communicate with the internet and prepare for initial exfiltration of the data harvested from the Exchange server.
Internet Connection Discovery (T1016.001): The actors used two different commands to see if they could access external websites. The first attempt used ping to see if they could resolve the IP address of a legitimate site. Once they confirmed they could resolve an external IP address they used certutil to try and download a file from a website and save it to a temporary directory.
File and Directory Discovery (T1083): The actors used the PowerShell dir cmdlet to recursively query a drive and list all of the files.
Archive Collected Data: Archive via Utility (T1560.001): Continuing to leverage PowerShell cmdlets, the actors used Compress-Archive to compress files they intended to exfiltrate from the server.
Masquerading (T1036): The actors renamed winrar.exe to vmware.exe to attempt to blend in as a normal system utility that the victim would expect to run on their host. This scenario renames a legitimate tool to vmware.exe and attempts to execute it.
When the actors returned on the following day, they continued their exploration of the infected hosts by examining environmental variables and searching for specific running processes. The actor continued to explore and search for additional files of interest. Artifacts and files created by the actor were cleaned up.
System Information Discovery (T1082): This time the actors executed set to print all the environmental variables. These variables can be a great source for credentials and important configuration settings used by different applications.
File and Directory Discovery (T1083): Instead of using PowerShell this scenario uses the traditional dir command to find files of interest and output to a temporary file.
Indicator Removal on Host: File Deletion (T1070.004): The rar files and other artifacts created by the actor were removed with the del command.
The last thing the actors wanted to get was a full file listing of everything on the hard drive including any hidden files. They again confirmed they could resolve an external IP using ping before bringing in PowerShell script that can export the Master File Table.
Ingress Tool Transfer (T1105): This scenario downloads to memory and saves to disk in two separate scenarios to test network and endpoint controls and their ability to prevent the delivery of known malicious content. This scenario downloads and saves the Export-MFT.ps1 script.
Having collected everything needed from the initial host, it was time to exfiltrate the data back to the actor’s server. The actors first staged the files in directory named debug before exfiltrating over an unreported protocol. They additional brought in the Impacket script utility to move laterally and execute commands on remote systems.
Data Staged (T1074): This scenario identifies Office documents and copies them to a temporary staging directory.
Exfiltration Over Unencrypted Non-C2 Protocol (T1048.003): The report doesn’t identify how exactly the initial files were exfiltrated. This scenario exfiltrates data using HTTP POSTs to an AttackIQ controlled server.
Windows Management Instrumentation (T1047): The attackers used Impacket’s wmiexec.py script to use WMI to execute commands and payloads on remote systems. This scenario uses the same wmic commands to execute commands on a remote target.
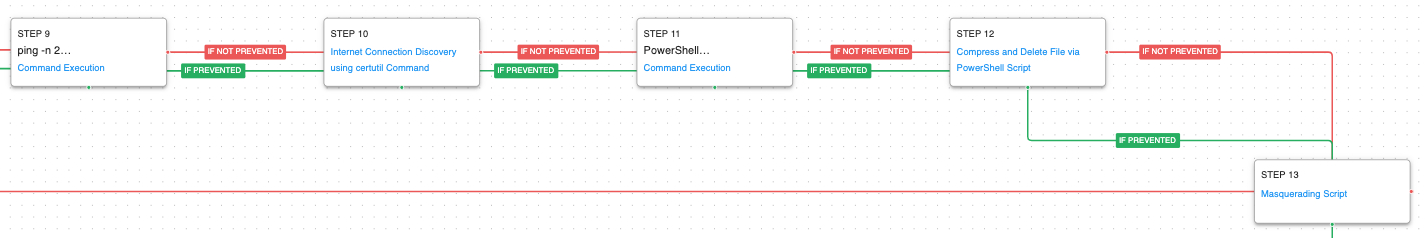
When the actors began moving to other systems using other exploits or WMI commands, they started bringing down their additional payloads. The actors used China Chopper webshells and their bespoke HyperBro backdoor.
Ingress Tool Transfer (T1105): HyperBro is typically delivered as a self-extracting executable that drops three files to disk. A legitimate binary, a malicious dll that gets side-loaded, and an encrypted configuration file which contains the settings and command-and-control servers for the malware.
HyperBro is a DLL file that gets executed by using the DLL side-loading technique which launches a legitimate executable that loads what it thinks are its own DLL files. When the DLL file is opened, program execution control is taken over and HyperBro begins its malicious activities. The malware will execute a svchost process and inject its own code into that processes’ memory. They use a service or registry run key for persistence before making its initial command-and-control request.
DLL Side-Loading (T1574.002): A legitimate executable is executed that loads a DLL file stored in the same directory that has been replaced with an AttackIQ dll file.
Bypass User Account Control (T1548.002): The malware attempts to disable UAC by setting a registry key.
Process Injection (T1055): This scenario injects a DLL file into another running process and validates if a canary file can be created.
Windows Service (T1543.003): Use the native sc command line tool to create a new service that will executed at reboot.
Registry Run Keys / Startup Folder (T1547.001): If the attack graph is unable to create the service it will pivot and attempt to create new registry startup values in the Run key.
Application Layer Protocol: Web Protocols (T1071.001): HyperBro uses HTTP for command-and-control traffic. This scenario makes the initial HTTP POST request to an AttackIQ controlled server emulating the exact web request made by a true HyperBro infection.
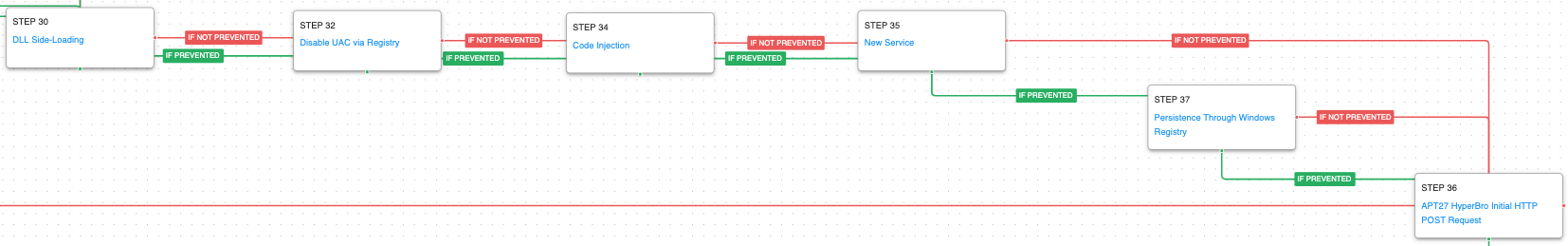
The last payload utilized by the threat actors is CovalentStealer. This malware is used to exfiltrate files to a Microsoft OneDrive share. CovalentStealer is delivered in two pieces, a decoder executable and the encrypted CovalentStealer. The decoder uses WMI to get disk information which it uses as a key to decrypt the CovalentStealer.
Windows Management Instrumentation (T1047): The decoder uses a WMI query to retrieve the disk serial number: SELECT volumeserialnumber FROM win32_logicaldisk WHERE Name='C:'
Opportunities for Extending the Attack Graph
The scenario ‘Export Master File Table via Export-MFT.ps1 Module’ was developed for this attack graph, but it has not been included by default as it can generate from more than half a gigabyte or more of data, which may fill the file system in assets with limited free space. If users would like to add it, that scenario can be included after saving the MFT file to the file system (step 20) to test the execution of that file against security controls.
Detection and Mitigation Opportunities
With so many different techniques being utilized by threat actors, it can be difficult to know which to prioritize for prevention and detection opportunities. AttackIQ recommends first focusing on the following techniques emulated in our scenarios before moving on to the remaining techniques.
1. System Network Configuration Discovery: Internet Connection Discovery (T1016.001):
Description
Adversaries may check for Internet connectivity on compromised systems. This may be performed during automated discovery and can be accomplished in numerous ways such as using Ping, tracert, certutil, and GET requests to websites.
1a. Detection
Using an EDR or SIEM product, you can create detections to alert when non-authorized users are using living off the land binaries to check for internet connectivity on compromised devices. In this case, the threat actor has been observed using certutil as the tool of choice.
Process Name == (“cmd.exe” OR “Powershell.exe”)
Command Line CONTAINS (“Certutil” AND “-urlcache” AND “-split” AND “-f”)
Username NOT IN (<List of expected admins utilizing certutil>)
1b. Mitigations
Although MITRE does not provide mitigations for this technique, it is possible to stay ahead of this by disabling interpreters and certutil for users in a non-administrative group. You can accomplish this by application whitelisting.
2. Abuse Elevation Control Mechanism: Bypass User Account Control (T1548.002):
Description
Adversaries may bypass UAC mechanisms to elevate process privileges on system. Windows User Account Control (UAC) allows a program to elevate its privileges (tracked as integrity levels ranging from low to high) to perform a task under administrator-level permissions, possibly by prompting the user for confirmation
2a. Detection
Using an EDR or SIEM Product, you can create detections to alert when UAC is attempting to be disabled via the Windows Registry.
Process Name = (“cmd.exe” OR powershell.exe”)
Command Line CONTAINS (“reg add” AND “HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System” AND “EnableLUA” AND “/d 0”)
2b. Mitigations
MITRE gives the following mitigations for Abuse Elevation Control Mechanism: Bypass User Account Control (T1548.002):
- M1047 – Audit
- M1026 – Priviileged Account Management
- M1051 – Update Software
- M1052 – User Account Control
3. Create or Modify System Process: Windows Service (T1543.003):
Description
Adversaries may create or modify Windows services to repeatedly execute malicious payloads as part of persistence. When Windows boots up, it starts programs or applications called services that perform background system functions.
3a. Detection
Using an EDR or SIEM product, you can create detections to alert when a possibly malicious service has been created due to adversarial behavior. In this case, the threat actor will attempt to create a service called “windefenders”. This is not to be confused with the benign windows defender service “windefend”:
Process Name = (“cmd.exe” OR “powershell.exe”)
Command Line CONTAINS (“sc” AND “Create” AND “windefenders”)
3b. Mitigations
MITRE gives the following mitigations for Create or Modify System Process: Windows Service (T1543.003 ):
- M1047 – Audit
- M1040 – Behavioral Protection on Endpoint
- M1045 – Code Signing
- M1028 – Operating System Configuration
- M1018 – User Account Management
Wrap-up
In summary, this attack graph will evaluate security and incident response processes and support the improvement of your security control posture against an actor who uses both native system tools, shared open-source scripts, and their own bespoke malware to achieve their goals. With data generated from continuous testing and use of this attack graph, you can focus your teams on achieving key security outcomes, adjust your security controls, and work to elevate your total security program effectiveness against a known and dangerous threat.
AttackIQ stands at the ready to help security teams implement this attack graph and other aspects of the AttackIQ Security Optimization Platform, including through our co-managed security service, AttackIQ Vanguard.