AttackIQ has recently released two new attack graphs covering historical campaigns by a group aligned to Russia’s General Staff Main Directorate of the Armed Forces (the GRU). The threat group, known as APT28, was attributed to the GRU in a U.S. Department of Justice indictment of July 2018. These new attack graphs involve the SkinnyBoy and Zebrocy malware families used in the campaign, along with standalone boundary posture management scenarios emulating APT28’s command-and-control traffic. This content emulates attacks APT28 has performed against multiple nations and sectors around the world and will help organizations test and validate their defenses against the threat more effectively.
In 2018, the U.S. Department of Justice indicted five GRU Unit 26165 officers associated with APT28 for their cyberspace operations conducted between 2014 and 2018 against the World Anti-Doping Agency (WADA), the U.S. Anti-Doping Agency, a U.S. nuclear facility, the Organization for the Prohibition of Chemical Weapons (OPCW), the Spiez Swiss Chemicals Laboratory, and other organizations. Some of these attacks were conducted with the assistance of the Sandworm Team, part of the GRU Unit 74455.
The adversary has conducted extensive cyberattacks across the globe, targeting all relevant sectors and organizations, aligned to the strategic interests of the Russian government. Heavily focused on governments and security organizations, data from victim organizations would give the Russian government a greater ability to predict policymaker intentions and influence public opinion. The Russian government has long cited European security organizations like NATO and the OSCE as existential threats, particularly during periods of increased tension in Europe.
To help customers validate their security controls against APT28, AttackIQ has released two new attack graphs that emulate different campaigns carried out by this adversary.
Validating your security program performance against these specific threat actor behaviors is paramount in reducing risk. By using these new attack graphs in the AttackIQ Security Optimization Platform, security teams will be able to:
- Evaluate security control performance against the repeated techniques that an active threat actor has utilized to be successful for years.
- Assess their security posture for attacks that are typically technically unsophisticated and noisy, but which have still allowed the actor to achieve their goals.
- Continuously validate detection and prevention pipelines as your security controls and posture improve.
APT28 Zebrocy – Nim and Golang variants lead to HTTP Exfiltration
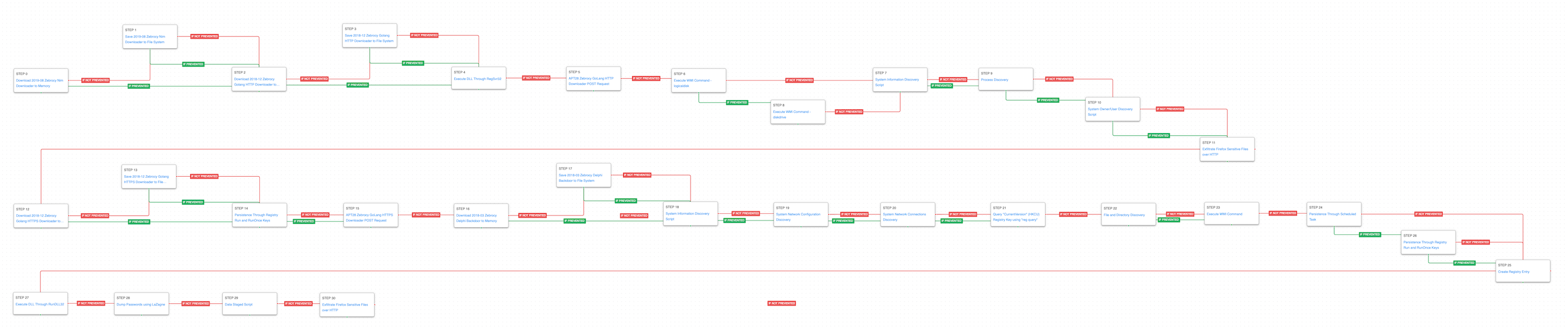
This attack graph covers a multitude of attacks conducted by APT28 between 2018 and 2019 that involved the use of their multi-family set of malware known as Zebrocy. Zebrocy consists of a set of downloaders, droppers, and backdoors written in several languages, such as Delphi, Golang, Nim, and AutoIT.
This attack graph begins with the use of a first stage downloader written in Nim that has as objective to fetch and deploy another downloader this time written in Golang. The second downloader is executed with RegSvr32 and proceeds to make an HTTP POST to complete an initial check-in with the actor’s infrastructure.
Ingress Tool Transfer (T1105): This scenario downloads to memory and saves to disk in two separate scenarios to test network and endpoint controls and their ability to prevent the delivery of known malicious webshells. These scenarios are used for each stage of the malware delivered in these attacks.
System Binary Proxy Execution: Regsvr32 (T1218.010): RegSvr32 is a native Windows utility that threat actors can use to register Common Object Model (COM) DLLs. This functionality allows an actor to deploy a malicious DLL and have a native Windows tool execute the code as the parent process. This scenario executes RegSvr32 with an AttackIQ binary.
Application Layer Protocol: Web Protocols (T1071.001): This scenario emulates the HTTP requests made by the Zebrocy Golang HTTP downloader by making an HTTP POST to an AttackIQ server that mimics the URL format and data sent by a real infection.
The downloader then proceeds to execute a series of automated discovery commands to collect profiling data it will later send to the actor before receiving its next stage. Details on the disk drives, basic system information, running process, and the system owner are first targeted. Sensitive browser data is then collected and exfiltrated over HTTP.
Windows Management Instrumentation (WMI) (T1047): WMI is a native Windows administration feature that provides a method for accessing Windows system components. These two scenarios execute the logicaldisk and diskdrive commands to retrieve details on the system’s disks.
System Information Discovery (T1082): The native systeminfo command is executed to retrieve all of the Windows system information.
Process Discovery (T1057): From a command window the tasklist command is run to download a list of all running processes.
System Owner/User Discovery (T1033): “query user” and whoami are called to determine what account is the webshell currently operating under.
Exfiltration Over C2 Channel (T1041): This scenario exfiltrates Firefox sensitive information using the HTTP POST requests. Our scenario exfiltrates the “cert9.db”, “key4.db” from a FireFox session filled with staged credentials.
The actor’s infrastructure will return a third-stage downloader if the collected information matches a target of interest. This third downloader is also written in Golang but uses HTTPS for its network requests instead of unencrypted in the second stage. Persistence is established using a registry run key before sending a POST to the command-and-control server where the final Zebrocy backdoor written in Delphi is received.
Logon Autostart Execution: Registry Run Keys (T1547.001): This scenario sets the “HKLM\Software\Microsoft\Windows\CurrentVersion\Run” and “RunOnce” registry keys that Windows uses to identify what applications should be run at system startup.
Application Layer Protocol: Web Protocols (T1071.001): Similar to the previous HTTP command-and-control scenario, this one mimics the Zebrocy HTTPS Golang downloader POST request which uses a different format then the previous stages.
Some of the same discovery and collection commands are re-executed by this last stage in addition to collection of information about the system’s network, current OS version, available files and directories, and a list of user accounts on the system. Persistence is established using a scheduled task or registry keys if the scheduled task creation was prevented.
System Network Configuration Discovery (T1016): The network configuration of the asset is collected using standard Windows utilities like ipconfig, arp, route, and nltest.
System Network Connections Discovery (T1049): The native Windows command line tool netstat is used to collect active connections and any listening services running on the host.
Query Registry (T1012): The "HKCU\Software\Microsoft\Windows\CurrentVersion" registry key contains information about Windows properties for the user accessing that registry key.
File and Directory Discovery (T1083): A batch script is executed that lists all files and directories in %ProgramFiles% and the %systemdrive%\Users directory.
Scheduled Task/Job: Scheduled Task (T1053.005): This scenario creates a new scheduled task using the schtasks utility.
Modify Registry (T1112): The “HKCU\Software\Classes\CLSID\{0CD069CF-AC9B-41F4-9571-3A95A62C36A1}” registry value is modified that Zebrocy uses to hijack COM objects and establish persistence.
Finally, the actors will execute their payloads using RunDll32 before dumping credentials from memory. Data of interest is staged before being exfiltrated with additional browser data.
System Binary Proxy Execution: Rundll32 (T1218.011): RunDll32 is another native system utility that can be used to execute DLL files and a specific export inside the file. This scenario executes RunDll32 with an AttackIQ DLL and export mimic previously reported malicious activity.
OS Credential Dumping (T1003): This scenario uses the open-source tool LaZagne to dump all possible credentials available on the host.
Local Data Staging (T1074.001): A batch file is executed looking for any office files found in the Users directory and copies any matching files to a staged directory in a temporary folder.
APT28 – 2021-05 – SkinnyBoy Campaign
This attack graph is based on a report with detailed analysis of the SkinnyBoy malware, also known as AceLog, that was observed targeting the defense industrial base and government sectors in May 2021.
The attack graph starts immediately after APT28 gained access to the victim’s network. It begins by downloading and executing the SkinnyBoy dropper. The dropper decodes its embedded payload and writes the second stage to disk.
Deobfuscate/Decode Files or Information (T1140): This scenario uses the certutil.exe to decode a base64 encoded executable.
Persistence is established using the Startup folder and the final SkinnyBoy payload is written to disk.
Logon Autostart Execution: Startup Folder (T1547.001): The Startup folder is a directory associated with the Windows Start Menu that can be used to launch a process at Windows logon. This scenario creates a binary file in this directory that would execute at next Logon for all users.
Similar discovery commands to the ones used in the Zebrocy attack are executed to collect details on the system configuration, running processes, and available files and directories. SkinnyBoy then begins to registry with the command-and-control server before requesting new commands. Files of interest are exfiltrated using HTTP.
Application Layer Protocol: Web Protocols (T1071.001): These two custom scenarios emulate the command-and-control requests made during a SkinnyBoy infection. The first request is to register with the c2 server while the second requests a command to be executed.
Opportunities for Extending the Attack Graph
In addition to these new attack graphs, there are additional stand-alone scenarios that can be added to the attack graph or as part of a separate assessment if customer’s have the appropriate environments.
The AttackIQ Security Optimization Platform contains many additional scenarios used in other APT28 campaigns. These can be identified by searching for any scenarios tagged with “APT28” under “Threat Actors.” Additionally, we have released two new PCAP replay scenarios that can be used to test network boundary controls by replaying malicious traffic captured during a APT28 infection.
PCAP Replay – APT28 Zebrocy Command and Control over SMTP: This PCAP replay scenario can be used to play back the command-and-control traffic associated with a Zebrocy infection that uses SMTP to send profiling data and screenshots to an actor-controlled server.
PCAP Replay – APT28 Zebrocy Delphi Downloader: This scenario replays PCAP traffic from a Zebrocy backdoor infection that includes system profiling data.
Detection and Mitigation Opportunities
With so many different techniques being used by threat actors, it can be difficult to know which to prioritize for prevention and detection opportunities. AttackIQ recommends first focusing on the following techniques emulated in our scenarios before moving on to the remaining techniques.
1. System Binary Proxy Execution: Rundll32 (T1218.011)
Description:
Adversaries may abuse rundll32.exe to proxy execution of malicious code. Using rundll32.exe instead of executing directly, may avoid triggering security tools that may not monitor execution of the rundll32.exe process because of allow-lists or false positives from normal operations.
1a. Detection:
Using a SIEM or EDR product, you can monitor the use of benign tools such as rundll32.exe being used to execute possibly malicious DLLs. A common way to detect this activity is to detect when DLLs are being executed from a globally writable directory, such as C:\Windows\Temp\
Process Name = (“cmd.exe” OR “powershell.exe”)
Command Line CONTAINS (“rundll32” AND “.dll”)
Target File Path CONTAINS (“\temp\” OR “\tmp\”)
1b. Mitigations:
MITRE ATT&CK Recommends the following mitigations for System Binary Proxy Execution: Rundll32 (T1218.011):
2. Windows Management Instrumentation (T1047)
Description:
Adversaries may abuse Windows Management Instrumentation (WMI) to execute malicious commands and payloads. WMI is an administration feature that provides a uniform environment to access Windows system components. The WMI service enables both local and remote access
2a. Detection:
Using an EDR or SIEM product, you can monitor when possible malicious actors are attempting to gather information on disk drives via WMI
Process Name = (“wmic.exe”)
Command Line Contains (“logicaldisk get”)
Username NOT IN (<list of authorized WMI Users>)
2b. Mitigations:
MITRE ATT&CK Recommends the following mitigations for Windows Management Instrumentation (T1047):
- M1040 – Behavioral Prevention on Endpoint
- M1038 – Execution Prevention
- M1026 – Privileged Account Management
- M1018 – User Account Management
3. Logon Autostart Execution: Registry Run Keys (T1547.001)
Description:
A common form of persistence for threat actors is to modify the CurrentVersion runonce/run keys to initialize access once the use on the infected endpoint has logged into the machine.
3a. Detection:
Using an EDR or SIEM product, you can monitor for possibly suspicious run/runonce registry key modifications
Process Name = “reg.exe”
Command Line CONTAINS (“/add” AND (“\CurrentVersion\Run” OR “\CurrentVersion\RunOnce”) AND (“cmd” or “powershell”)
Username NOT IN (<list of expected reg.exe users>)
3b. Mitigations:
Although MITRE does not have any recommended mitigations for this technique, it is still possible to reduce this from occurring from lower privileged users. Utilize application whitelisting and group policy permissions to prevent non-administrators the right to modify run/runonce keys via cmd.exe, powershell.exe, regedit.exe, or reg.exe.
Wrap-up
In summary, these two attack graph will evaluate security and incident response processes and support the improvement of your security control posture against an actor who has been successful for over a decade. With data generated from continuous testing and use of this attack graph, you can focus your teams on achieving key security outcomes, adjust your security controls, and work to elevate your total security program effectiveness against a known and dangerous threat.
AttackIQ stands at the ready to help security teams implement this attack graph and other aspects of the AttackIQ Security Optimization Platform, including through our co-managed security service, AttackIQ Vanguard.
 (Click for Larger)
(Click for Larger)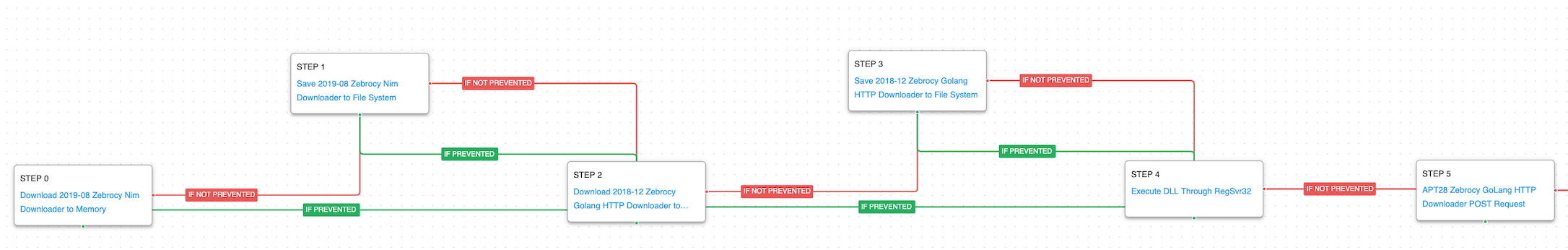 (Click for Larger)
(Click for Larger)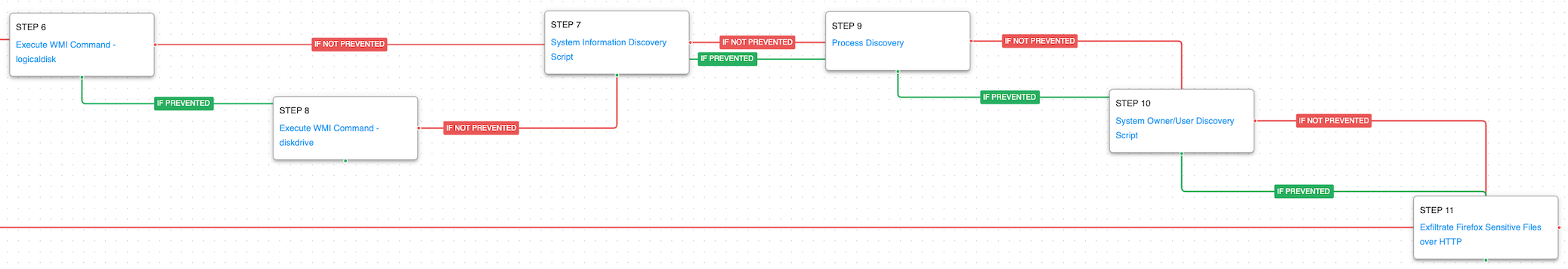 (Click for Larger)
(Click for Larger)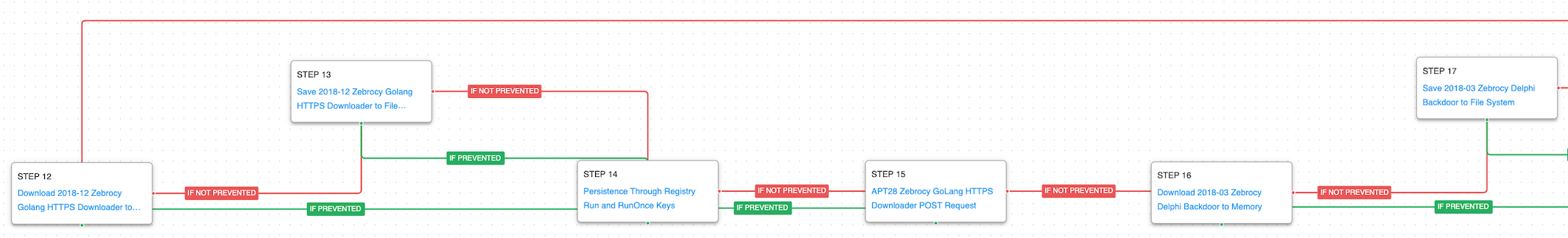 (Click for Larger)
(Click for Larger)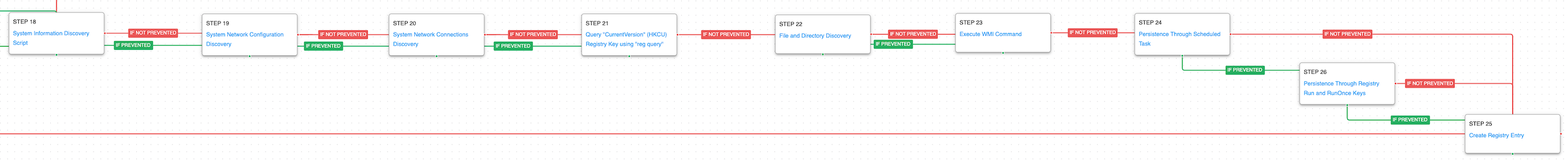 (Click for Larger)
(Click for Larger) (Click for Larger)
(Click for Larger) (Click for Larger)
(Click for Larger) (Click for Larger)
(Click for Larger)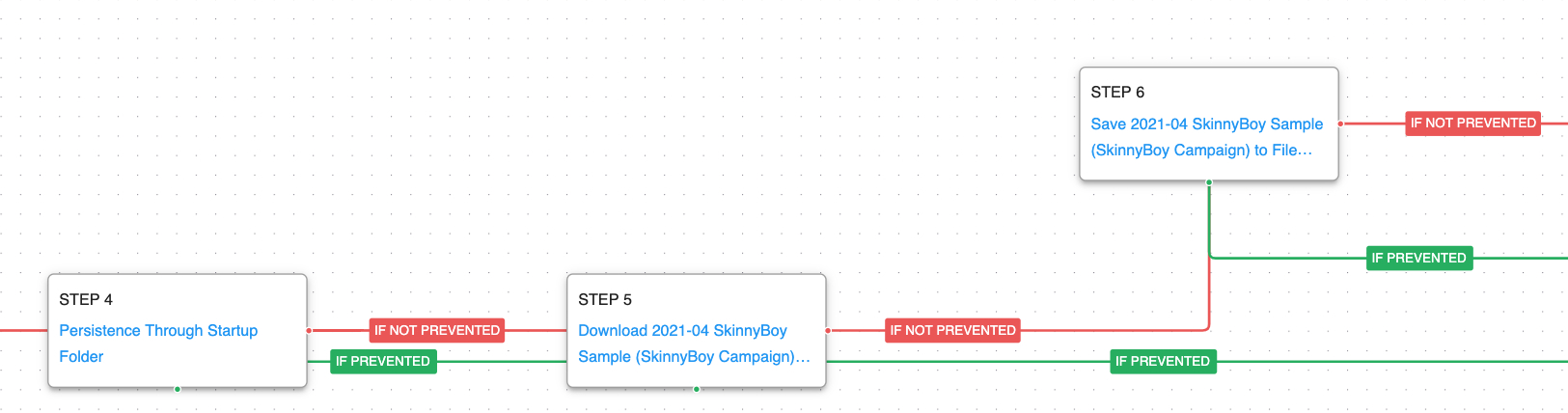 (Click for Larger)
(Click for Larger) (Click for Larger)
(Click for Larger)

