Ransomware continues to dominate the threat landscape with increasing frequency and sophistication. According to Check Point, the first quarter of 2025 experienced a staggering 126% increase in ransomware attacks compared to the same period in 2024. This is not a statistical anomaly; it reflects an evolving landscape where financially motivated adversaries continue to leverage increasingly advanced techniques to maximize disruption and extortion.
Given this escalation, it is imperative that organizations extend beyond reactive security measures and adopt a more proactive, threat-informed defense strategy. As ransomware operators continue to evolve their tradecraft, defenders must rise to the challenge with equally adaptive and intelligence-driven strategies. The increasing prevalence of ransomware is not a temporary phase but a strategic shift that demands sustained vigilance and operational readiness.
To address this challenge, AttackIQ introduces Ransom Tales, an initiative focused on routinely emulating the Tactics, Techniques, and Procedures (TTPs) associated with the prolific ransomware families currently dominating the threat landscape. Each volume in this series is designed to dissect the operational behaviors of multiple ransomware families and translate them into realistic emulations that defenders can employ to rigorously challenge their security controls and enhance resilience against disruptive and extortive threats.
AttackIQ has released three new attack graphs that emulate the Tactics, Techniques and Procedures (TTPs) associated with the BlackLock, Embargo and Mamona ransomware families with the objective of assisting customers in validating their security controls and their ability to defend against these disruptive and extortive threats.
Validating your security program performance against these behaviors is vital in reducing risk. By employing these assessment templates in the AttackIQ Security Optimization Platform, security teams will be able to:
- Evaluate security control performance against baseline behaviors associated with prolific and sophisticated ransomware strains.
- Assess their security posture against opportunistic and financially motivated adversaries that do not discriminate when selecting their targets.
- Continuously validate detection and prevention pipelines against a playbook similar to those of many of the adversaries currently focused on ransomware activities.
[Malware Emulation] BlackLock Ransomware – 2024-07 – Associated Tactics, Techniques and Procedures (TTPs)
This emulation replicates the sequence of behaviors associated with the deployment of BlackLock ransomware on a compromised system with the intent of providing customers with the opportunity to detect and/or prevent a compromise in progress.
BlackLock is a ransomware strain operated under the Ransomware-as-a-Service (RaaS) model that emerged in March 2024. Initially known as ElDorado, the group rebranded to BlackLock in late 2024 and has since become one of the most prolific ransomware operations of 2025.
Developed in GoLang for cross-platform compatibility, BlackLock payloads are generated through a proprietary builder capable of producing variants for Linux and Windows, supporting both x86 and x64 architectures. The builder allows for extensive customization, including specification of targeted networks or organizations, ransom note details, and credential-related parameters, such as the domain administrator’s password or the Windows New Technology LAN Manager (NTLM) hash, while the username is retrieved from the system environment.
BlackLock employs ChaCha20 for file encryption and Rivest–Shamir–Adleman with Optimal Asymmetric Encryption Padding (RSA-OAEP) for key encryption. It is also capable of encrypting files located on shared network drives via the Server Message Block (SMB) protocol.
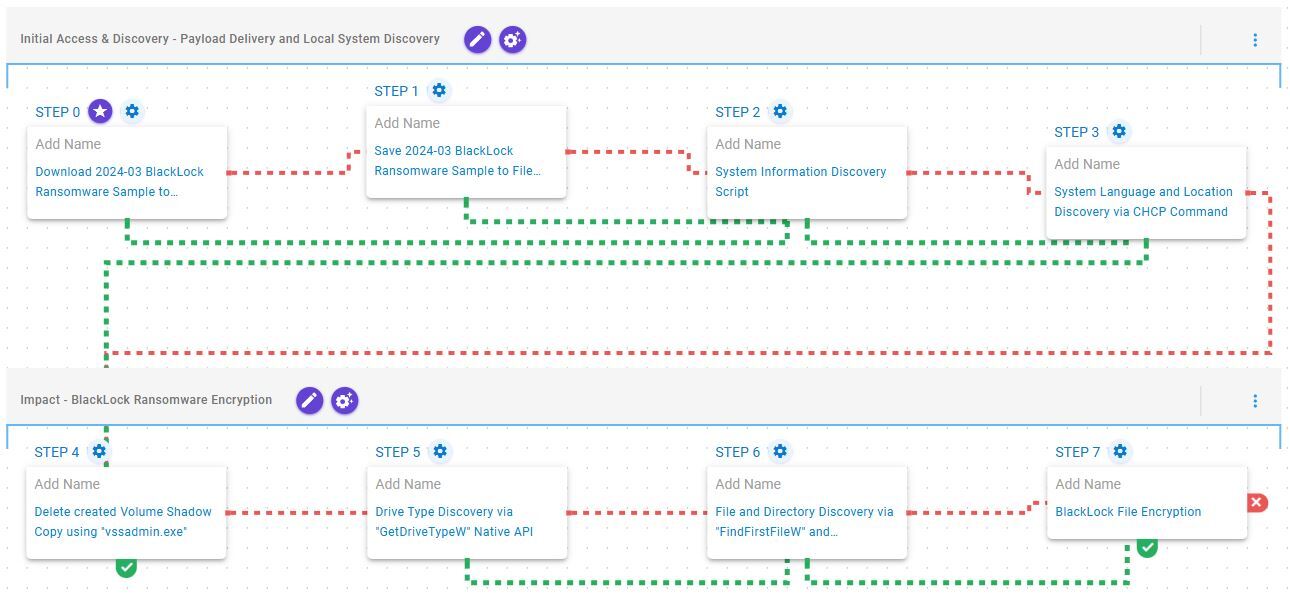
Initial Access & Discovery – Payload Delivery and Local System Discovery
This stage begins with the deployment of BlackLock ransomware which, once operational, retrieves general information about the local environment, including the system language and geographic location.
Ingress Tool Transfer (T1105): This scenario downloads to memory and saves to disk in independent scenarios to test network and endpoint controls and their ability to prevent the delivery of known malicious samples.
System Information Discovery (T1082): This scenario executes the native systeminfo command to retrieve all the Windows system information.
System Language Discovery (T1614.001): This scenario executes the chcp command to collect information on the active console code page of the system.
Impact – BlackLock Ransomware Encryption
This stage begins with the deletion of volume shadow copies via vssadmin.exe followed by drive type identification via GetDriveTypeW. Finally, the identified drives are recursively traversed using FindFirstFileW and FindNextFileW to locate files of interest, which are subsequently encrypted using a combination of ChaCha20 and RSA-2048.
Inhibit System Recovery (T1490): This scenario executes the vssadmin.exe utility to delete a recent Volume Shadow Copy created by the assessment template.
System Information Discovery (T1082): This scenario executes the GetDriveTypeW Windows API call to retrieve information regarding the system’s physical drives.
File and Directory Discovery (T1083): This scenario executes the FindFirstFileW and FindNextFileW Windows API calls to perform the enumeration of the file system.
Data Encrypted for Impact (T1486): This scenario performs the file encryption routines used by common ransomware families. Files matching an extension list are identified and encrypted in place using similar encryption algorithms as used by BlackLock ransomware.
[Malware Emulation] Embargo Ransomware – 2024-10 – Associated Tactics, Techniques and Procedures (TTPs)
This emulation replicates the sequence of behaviors associated with the deployment of Embargo ransomware on a compromised system with the intent of providing customers with the opportunity to detect and/or prevent a compromise in progress.
Embargo is a ransomware strain operated under the Ransomware-as-a-Service (RaaS) model that emerged in May 2024. Notable for targeting high-profile organizations, Embargo gained notoriety for being developed in Rust, a cross-platform programming language that enables the development of versatile payloads capable of affecting both Windows and Linux environments.
The operation behind Embargo appears to be well-resourced, maintaining its infrastructure to communicate with victims while also allowing communication through Tox. Its activities employ a double extortion strategy, combining exfiltration of sensitive information with the encryption of information on compromised systems. Failure to comply with ransom demands results in the publication of the exfiltrated information on the Dedicated Leak Site (DLS). This tactic increases pressure by introducing reputational damage, legal consequences, and financial risks, including the potential loss of customer confidence.
According to public reporting, Embargo has been deployed in operations associated with affiliates of the BlackLock ransomware group.
Initial Access & Discovery – Payload Delivery and Local System Discovery
This stage begins with the deployment of Embargo ransomware which, once operational, retrieves general information about the local environment, explores running processes, and enumerates system services via the Windows API.
Ingress Tool Transfer (T1105): This scenario downloads to memory and saves to disk in independent scenarios to test network and endpoint controls and their ability to prevent the delivery of known malicious samples.
System Information Discovery (T1082): This scenario executes the GetNativeSystemInfo Native API call to retrieve information associated to the system.
Process Discovery (T1057): This scenario uses Windows API to receive a list of running processes by calling CreateToolhelp32Snapshot and iterating through each process object with Process32FirstW and Process32NextW.
System Service Discovery (T1007): This scenario executes the EnumServiceStatus Windows API to gather critical information about configured services.
Impact – Embargo Ransomware Encryption
This stage begins with volume enumeration using the FindFirstVolumeW and FindNextVolumeW APIs. It then performs network resource discovery by invoking WNetOpenEnumW and WNetEnumResourceW, followed by drive type identification via GetDriveTypeW. Finally, the identified volumes are recursively traversed using FindFirstFileW and FindNextFileW to locate files of interest, which are subsequently encrypted using a combination of ChaCha20 and Elliptic Curve Cryptography (ECC) with Curve25519.
System Information Discovery (T1082): This scenario executes the FindFirstVolumeW and FindNextVolumeW Windows API calls to iterate through the available volumes of the system.
System Network Connections Discovery (T1049): This scenario executes the WNetOpenEnumW and WNetEnumResourceW Windows API calls to enumerate network resources from the local computer.
System Information Discovery (T1082): This scenario executes the GetDriveTypeW Windows API call to retrieve information regarding the system’s physical drives.
File and Directory Discovery (T1083): This scenario executes the FindFirstFileW and FindNextFileW Windows API calls to perform the enumeration of the file system.
Data Encrypted for Impact (T1486): This scenario performs the file encryption routines used by common ransomware families. Files matching an extension list are identified and encrypted in place using similar encryption algorithms as used by Embargo ransomware.
[Malware Emulation] Mamona Ransomware – 2025-05 – Associated Tactics, Techniques and Procedures (TTPs)
This emulation replicates the sequence of behaviors associated with the deployment of Mamona ransomware on a compromised system with the intent of providing customers with the opportunity to detect and/or prevent a compromise in progress.
Mamona is a ransomware strain that has been active since at least May 2025. It operates entirely offline, with no external Command and Control (C2) communication and no confirmed file exfiltration, suggesting that its extortion claims may be false. The payload only performs local encryption, executing all cryptographic operations locally while employing custom routines that do not rely on standard libraries. Encrypted files are renamed with the .HAes extension while ransom notes are dropped in multiple directories.
Despite its short lifespan, Mamona has gained notoriety after being deployed in activities associated with BlackLock ransomware affiliates.
Initial Access & Discovery – Payload Delivery and Local System Discovery
This stage begins with the deployment of Mamona ransomware, which, once operational, retrieves general information about the local environment, including debugger detection, MachineGUID identification, and proceeds to enumerate running processes and system services via the Windows API.
Ingress Tool Transfer (T1105): This scenario downloads to memory and saves to disk in independent scenarios to test network and endpoint controls and their ability to prevent the delivery of known malicious samples.
Virtualization/Sandbox Evasion (T1497): This scenario will execute the IsDebuggerPresent Windows API to detect the presence of a debugger attached to the current process.
System Information Discovery (T1082): This scenario executes the GetNativeSystemInfo Native API call to retrieve information associated to the system.
Query Registry (T1012): This scenario queries the MachineGUID value located within the HKLM\SOFTWARE\Microsoft\Cryptography registry key which contains the unique identifier of the system.
Process Discovery (T1057): This scenario uses Windows API to receive a list of running processes by calling CreateToolhelp32Snapshot and iterating through each process object with Process32FirstW and Process32NextW.
System Service Discovery (T1007): This scenario executes the QueryServiceStatusEx and EnumDependentServices Windows API calls to retrieve information pertaining to a given service.
Impact – Mamona Ransomware Encryption
This stage begins with logical drive enumeration through the GetLogicalDrives and GetLogicalDriveStringsW APIs, followed by drive type identification via GetDriveTypeW. The identified drives are then recursively traversed using FindFirstFileW and FindNextFileW to locate files of interest, which are subsequently encrypted using a combination of AES-128 in CBC mode and RSA-2048.
System Information Discovery (T1082): This scenario executes the GetLogicalDrives Windows API call to retrieve the currently available disk drives.
System Information Discovery (T1082): This scenario executes the GetLogicalDriveStringsW Windows API call to retrieve information regarding the system’s physical drives.
System Information Discovery (T1082): This scenario executes the GetDriveTypeW Windows API call to retrieve information regarding the system’s physical drives.
File and Directory Discovery (T1083): This scenario executes the FindFirstFileW and FindNextFileW Windows API calls to perform the enumeration of the file system.
Data Encrypted for Impact (T1486): This scenario performs the file encryption routines used by common ransomware families. Files matching an extension list are identified and encrypted in place using similar encryption algorithms as used by multiple ransomware strains.
Detection and Mitigation Opportunities
Given the number of different techniques being utilized by these threats, it can be difficult to know which to prioritize for prevention and detection opportunities. AttackIQ recommends first focusing on the following techniques emulated in our scenarios before moving on to the remaining techniques.
1. Ingress Tool Transfer (T1105):
Adversaries depend on the deployment of payloads, often across multiple stages, within targeted environments to achieve their objectives. Given this dependency, it is essential to employ both Endpoint and Network security controls to detect and block these throughout the multiple phases of delivery and execution.
1a. Detection
The following signatures can help identify when native utilities are being used to download malicious payloads.
PowerShell Example:
Process Name == (Cmd.exe OR Powershell.exe)
Command Line CONTAINS ((“IWR” OR “Invoke-WebRequest") AND “DownloadData” AND “Hidden”)
1b. Mitigation
MITRE ATT&CK has the following mitigation recommendations.
2. Inhibit System Recovery (T1490):
Adversaries often delete Volume Shadow Copies to prevent the possibility of restoring files back to their original state. This is a common technique used by ransomware as it prevents the recovery of files once the ransomware encryption routine successfully completes execution.
2a. Detection
Detecting deletion of Volume Shadow Copies is usually the first step that occurs and can be detected by looking at the command line activity
Process Name == (cmd.exe OR powershell.exe)
Command Line CONTAINS (“vssadmin” AND “Delete Shadows”)
2b. Mitigation
MITRE ATT&CK has the following mitigation recommendations for Inhibit System Recovery:
Wrap-up
In summary, these attack graphs will evaluate security and incident response processes and support the improvement of your security control posture against the behaviors exhibited by BlackLock, Embargo and Mamona ransomware operators. With data generated from continuous testing and use of this assessment template, you can focus your teams on achieving key security outcomes, adjust your security controls, and work to elevate your total security program effectiveness against a known and dangerous threat.
AttackIQ, the leading provider of Adversarial Exposure Validation (AEV) solutions, is trusted by top organizations worldwide to validate security controls in real time. By emulating real-world adversary behavior, AttackIQ closes the gap between knowing about a vulnerability and understanding its true risk. AttackIQ’s AEV platform aligns with the Continuous Threat Exposure Management (CTEM) framework, enabling a structured, risk-based approach to ongoing security assessment and improvement. The company is committed to supporting its MSSP partners with a Flexible Preactive Partner Program that provides turn-key solutions, empowering them to elevate client security. AttackIQ is passionate about giving back to the cybersecurity community through its free award-winning AttackIQ Academy and founding research partnership with MITRE Center for Threat-Informed Defense.

 Click for Larger
Click for Larger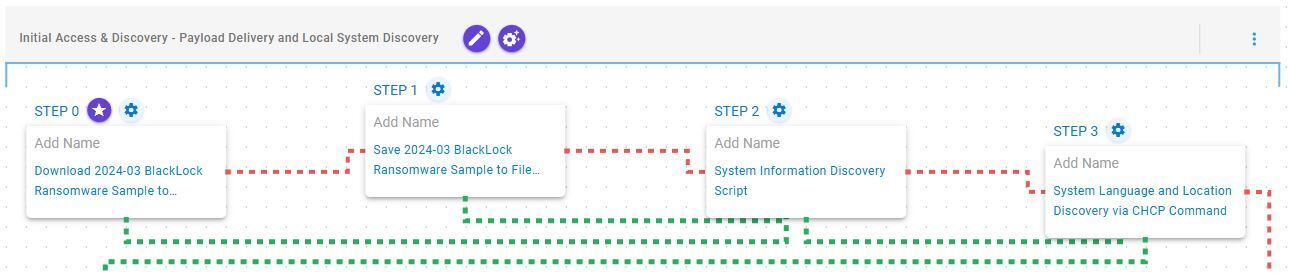 Click for Larger
Click for Larger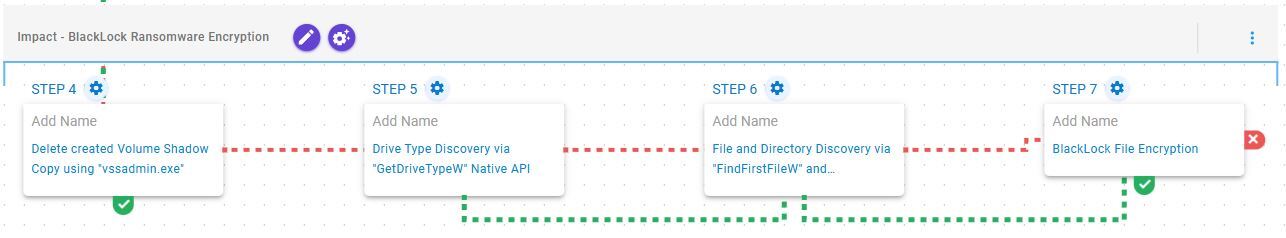 Click for Larger
Click for Larger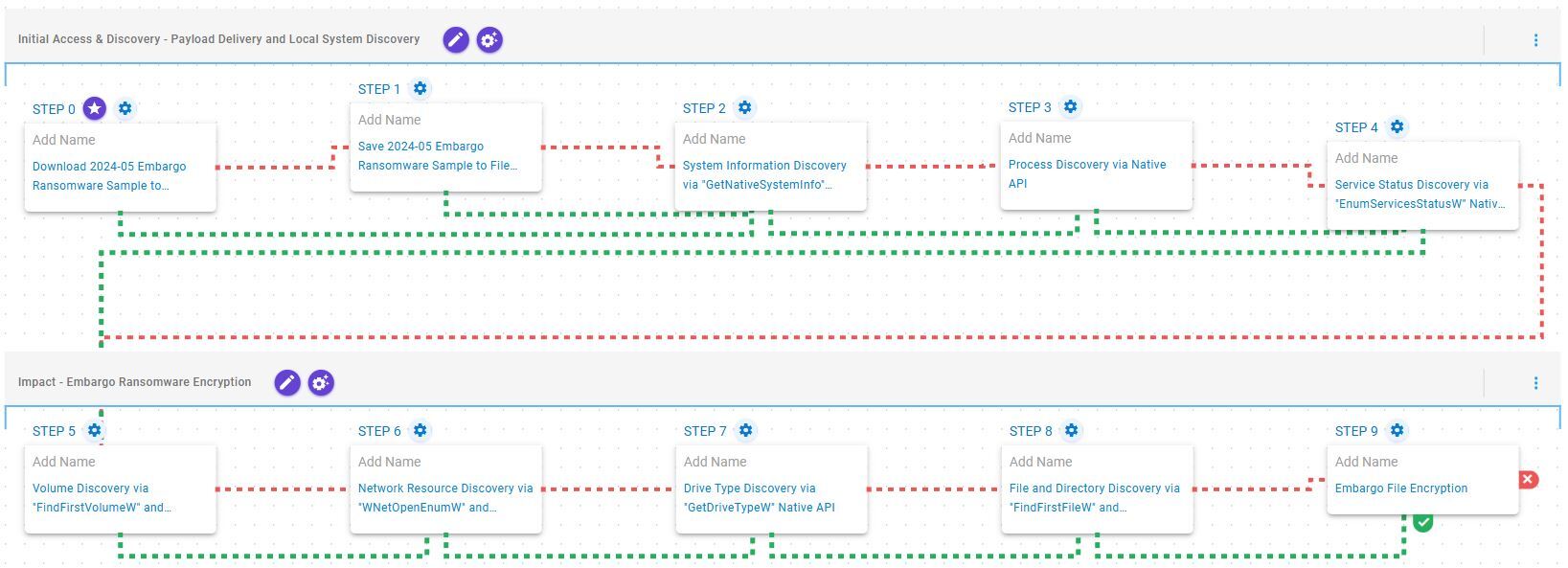 Click for Larger
Click for Larger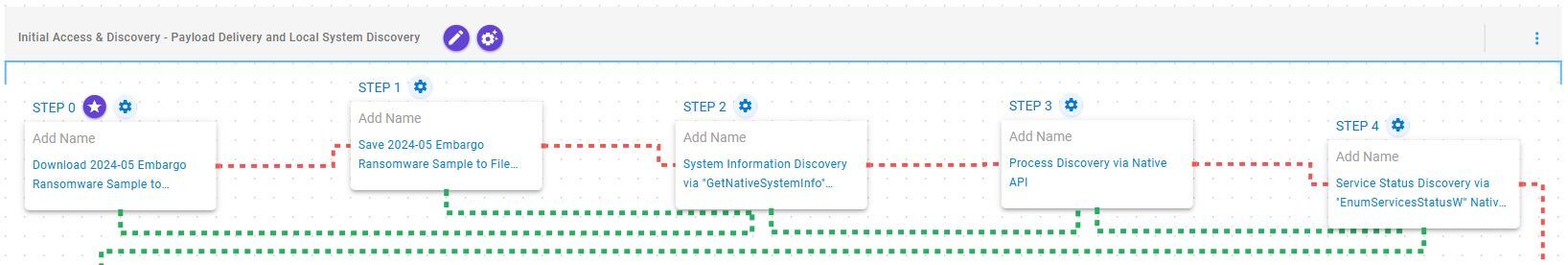 Click for Larger
Click for Larger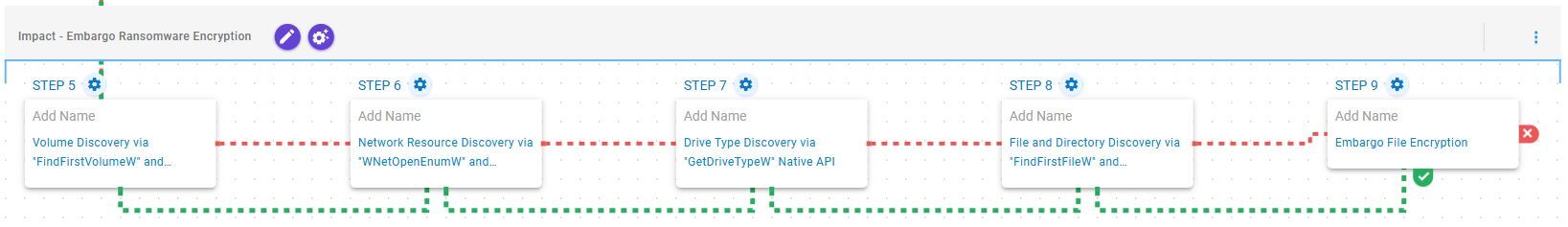 Click for Larger
Click for Larger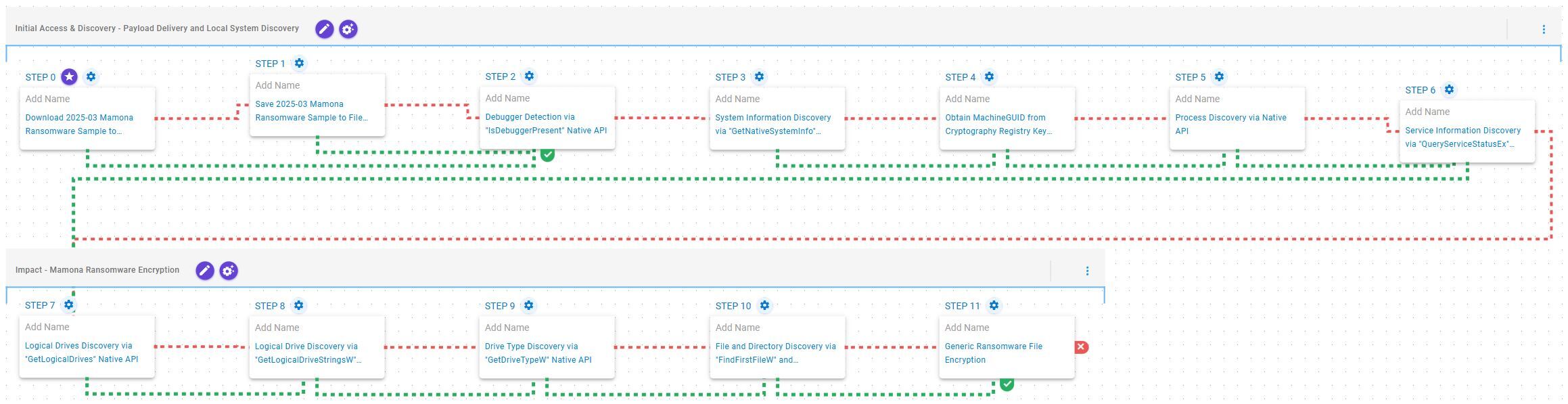 Click for Larger
Click for Larger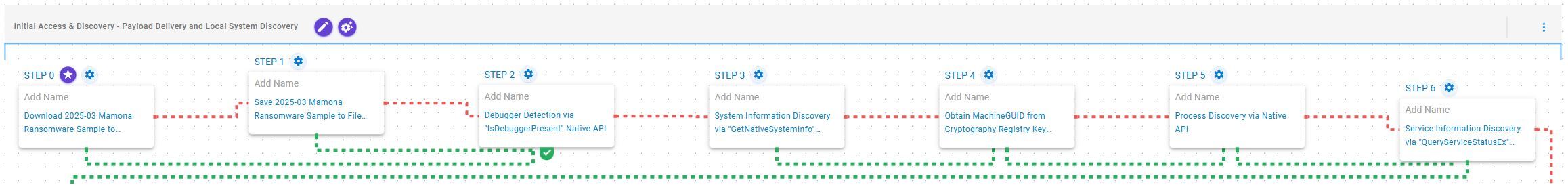 Click for Larger
Click for Larger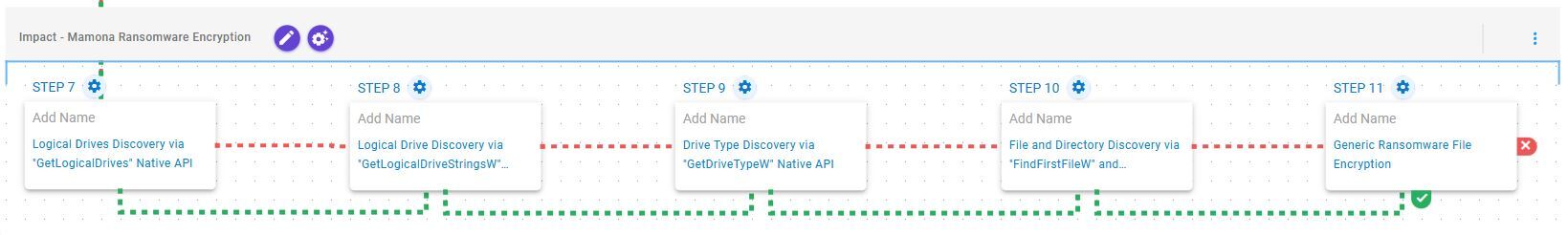 Click for Larger
Click for Larger