BumbleBee is a loader first discovered by Google’s Threat Analysis Group (TAG) in September 2021 that is linked to multiple adversaries in the cybercrime world. Threat actors began transitioning from BazarLoader and BokBot in February 2022 and over to BumbleBee which improved and gained new functionality quickly.
BumbleBee is under constant development and contains elaborate evasion techniques including complex anti-virtualization checks making detection and analysis difficult. This malware family acts as an initial delivery mechanism and has been observed dropping Cobalt Strike and Meterpreter. Attacks using BumbleBee detected by TAG were linked to Conti and Diavol ransomware intrusions.
The adversary behind BumbleBee delivery campaigns is known as Exotic Lily, a financially motivated actor first discovered in September 2021. Exotic Lily is suspected of acting as an Initial Access Broker (IAB) on behalf of a Russian-based adversary known as FIN12 or Wizard Spider. Primarily attacking via spearphishing, at the height of Exotic Lily’s activity it is estimated that they were sending more than 5,000 emails per day to 650 organizations worldwide.
AttackIQ has released two new attack graphs that emulate attacks involving the BumbleBee loader to help our customers validate their security controls and defend against an essential commodity widely used by cybercriminals. Validating the performance of your security program against these behaviors is vital to reducing risk. By using these new attack graphs in the AttackIQ Security Optimization Platform, security teams will be able to:
- Evaluate security control performance against multiple attacks who initiate attacks using BumbleBee.
- Assess their security posture against a malware family that evolves over time but relies on similar techniques to be successful.
- Continuously validate detection and prevention pipelines against attacks with different motivations including ransomware.
BumbleBee – 2022-05 – Lateral Movement using RDP and Cobalt Strike
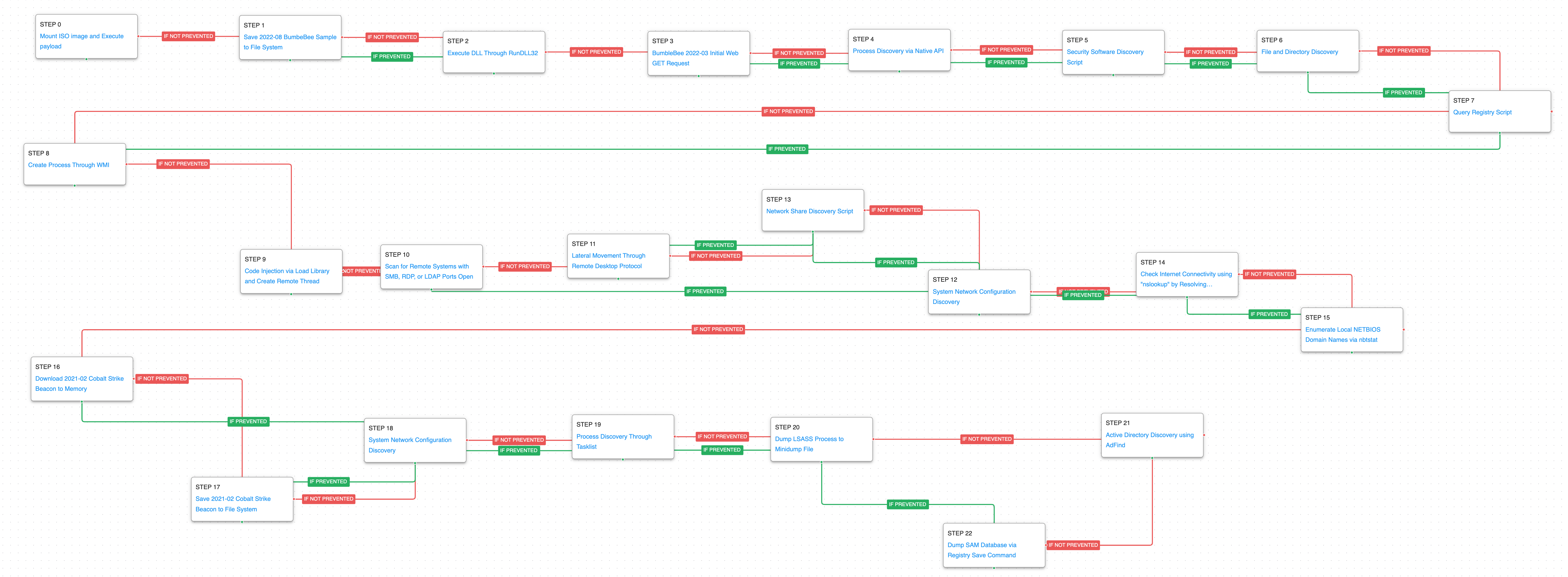
The first attack graph is based on activity detected in May 2022, when adversaries were observed using BumbleBee through the delivery of ISO files containing a malicious LNK and DLL file. After the execution of BumbleBee, multiple processes were spawned with the goal of injecting Meterpreter into another running process to conduct reconnaissance on the workstation and network. The actor queried domain controllers, mapped domain joined computers, enumerated Active Directory trusts, and listed Domain Admin accounts.
The attack graph begins with the mounting of an ISO image and dropping of a malicious BumbleBee sample. Execution is emulated by leveraging RunDLL32 which initiates an initial check-in request to a simulated command and control server. The malware would then begin some initial discovery of what software is running and files that are available.
Subvert Trust Controls: Mark-of-the-Web (MOTW) Bypass (T1553.005): This scenario bypasses MOTW by downloading and mounting an ISO image on the system to execute the payload contained inside.
Ingress Tool Transfer (T1105): This scenario saves to disk a known sample of the BumbleBee loader to test endpoint controls and their ability to prevent the delivery of known malicious files.
System Binary Proxy Execution: Rundll32 (T1218.011): RunDll32 is a native system utility that can be used to execute DLL files and call a specific export inside the file. This scenario executes RunDll32 with an AttackIQ DLL and calls an export to mimic previously reported malicious activity.
Application Layer Protocol: Web Protocols (T1071.001): This scenario emulates the HTTP request made by BumbleBee during an initial infection by making an HTTP POST to an AttackIQ server that mimics the URL format and data sent by a real infection.
Process Discovery (T1057): The Windows API is used to receive a list of running processes by calling CreateToolhelp32Snapshot and iterating through each process object with Process32FirstW and Process32NextW.
Software Discovery (T1518.001): A PowerShell script is executed to determine which software has been installed as an AntiVirusProduct class.
File and Directory Discovery (T1083): This scenario uses the native dir command to find files of interest and record output to a temporary file.
Query Registry ( A registry key observed during BumbleBee infections is queried using reg.exe.
The second stage of the attacks begins with a new process spawned using WMI later used to inject Meterpreter. Subsequently, the adversary will seek to move laterally by means of RDP and will continue with another round of environment discovery focused on the victim’s network.
Windows Management Instrumentation (T1047): This scenario uses wmic commands to launch an executable when a common event consumer is triggered.
Process Injection (T1055): This scenario injects a DLL file into another running process using Windows API calls to LoadLibrary and CreateRemoteThread.
Network Service Discovery (T1046): This scenario uses nmap for scanning hosts that are open on ports 139,389,445,636,3389 that would identify remotely accessible hosts to the attacker.
Remote Services: Remote Desktop Protocol (T1021.001): Remote Desktop is the built-in remote access utility used by Windows. This scenario attempts to remotely connect to another accessible asset with stolen credentials.
Network Share Discovery (T1135): The native net tools are used to list all the local mapped network shares with net share.
System Network Configuration Discovery (T1016): The network configuration of the asset is collected using standard Windows utilities like ipconfig, arp, route, and nltest.
Internet Connection Discovery (T1016.001): This scenario uses nslookup to query an external domain using Google’s DNS (8.8.8.8). The actors utilize this command to determine if they will be able to potentially gain outbound unrestricted access to the internet.
System Network Connections Discovery (T1049): The NETBIOS name table for the host is collected with the nbtstat -n command.
In the final stage, a Cobalt Strike Beacon is downloaded and saved to disk, which will again seek to collect additional system information, and obtain a dump of the LSASS process that can be used to dump credentials. The last step involves using AdFind to learn more about the Active Directory environment of their victim.
Ingress Tool Transfer (T1105): This scenario downloads to memory and saves to disk in two separate scenarios to test network and endpoint controls and their ability to prevent the delivery of known Cobalt Strike samples.
Process Discovery (T1057): Window’s built-in tasklist command is executed as a command process and the results are saved to a file in a temporary location.
OS Credential Dumping: LSASS Memory (T1003.001): LSASS memory is dumped to disk by creating a minidump of the lsass process. This process is used for enforcing security policy on the system and contains many privileged tokens and accounts that are targeted by threat actors.
OS Credential Dumping: Security Account Manager (T1003.002): The built-in reg save command is executed to dump the Windows SAM hive.
Account Discovery: Domain Account (T1087.002): The Adfind utility is used to discover details about the victim’s Active Directory configuration including accounts, groups, computers, and subnets.
BumbleBee – 2022-04 – Lateral Movement using WMIC and Kerberoasting
The second attack graph is based on the activity detected in April 2022, when researchers observed a wave of attacks that used BumbleBee using a password-protected ZIP. These attacks occurred prior to the previously described activity and share many of the same techniques.
The main difference was in the way they accessed additional remote systems. This time the actors remotely executed command through the command line and leveraged Kerberoasting to gain privileged access to additional hosts.
The attack graph starts the same way as before with the delivery and mounting of an ISO file that leads to execution of the malicious payload using RunDll32. The malware checks in with the command-and-control server before moving on to the second stage of activity.
Another sample of a Cobalt Strike Beacon is downloaded and saved to disk which is injected into an existing process in the system. The actor then leverages the Kerberoasting technique to gain additional credentials it could use for lateral movement before executing a couple of commands and tools to learn about the infected environment.
Steal or Forge Kerberos Tickets – Kerberoasting (T1558.003): Kerberoasting allows an attacker to attempt to extract password hashes for accounts using their Service Principal Name (SPN) ticket. The attack graph tries using the Invoke-Kerberoast PowerShell cmdlet.
System Time Discovery (T1124): The scenario identifies the time and time zone of the compromised system through the net time command.
The last phase begins with dumping the LSASS process and scanning for additional Windows hosts. Remote commands are executed by using WMIC and a Windows service is established to maintain persistence.
Windows Management Instrumentation (T1047): This scenario uses wmic commands to execute commands on a remote target.
Windows Service (T1543.003): Use the native sc command line tool to create a new service that will executed at reboot.
Detection and Mitigation Opportunities
With so many different techniques being used by threat actors, it can be difficult to know which to prioritize for prevention and detection assessment. AttackIQ recommends first focusing on the following techniques emulated in our scenarios before moving on to the remaining techniques.
1. Mark-of-the-Web (MOTW) Bypass (T1553.005) and Rundll32 (T1218.011)
BumbleBee has most commonly been delivered inside an ISO file that uses a shortcut file to execute a DLL file. When an ISO file is opened in Windows a new DVD drive is mounted to the host and the LNK file will execute RunDll32 with the current directory set to that new drive.
1a. Detection
Search for files that are being executed from those drives or don’t have the standard .dll file extension.
Process Name == (rundll32.exe)
Current Directory CONTAINS (‘D:\’ OR ‘E:\’)
1b. Mitigation
2. OS Credential Dumping: LSASS Memory (T1003.001)
The Local Security Authority Subsystem Service (LSASS) process contains in memory a variety of credentials for logged in users. Actors commonly use the Windows utility procdump to create a minidump of the memory for the running process.
2a. Detection
Search for executions of procdump that attempt to access the lsass process.
Process Name == (procdump)
Command Line CONTAINS (‘lsass’)
2b. Mitigation
- M1050 – Behavior Prevention on Endpoint
- M1043 – Credential Access Protection
- M1028 – Operating System Configuration
- M1027 – Password Policies
- M1026 – Privileged Account Management
- M1025 – Privileged Process Integrity
- M1017 – User Training
3. Process Injection (T1055)
Malware will commonly inject malicious code into other running processes to attempt to blend in with legitimate applications.
3a. Detection
Searching for common processes that are performing uncommon actions can help identify when a process has been compromised.
3b. Mitigation
Wrap-up
In summary, these attack graphs will evaluate security and incident response processes and support the improvement of your security control posture against many actors using the same initial access broker. With data generated from continuous testing and use of these attack graphs, you can focus your teams on achieving key security outcomes, adjust your security controls, and work to elevate your total security program effectiveness against a known and dangerous threat.
AttackIQ stands at the ready to help security teams implement this attack graph and other aspects of the AttackIQ Security Optimization Platform, including through our co-managed security service, AttackIQ Vanguard.
 Click for Larger
Click for Larger Click for Larger
Click for Larger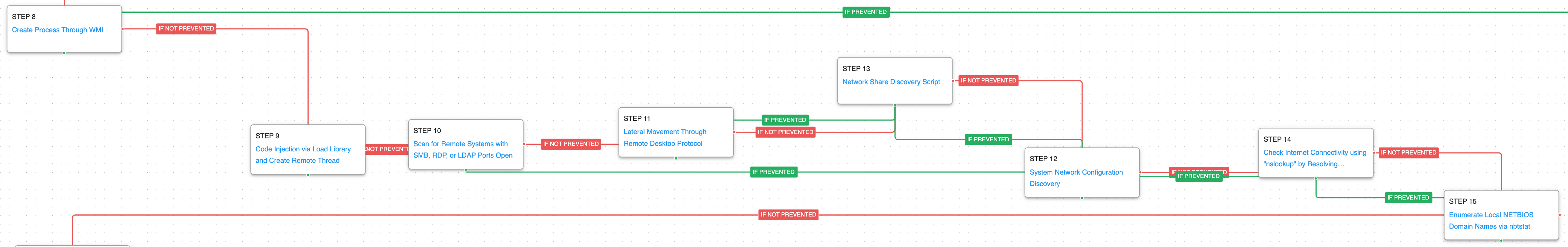 Click for Larger
Click for Larger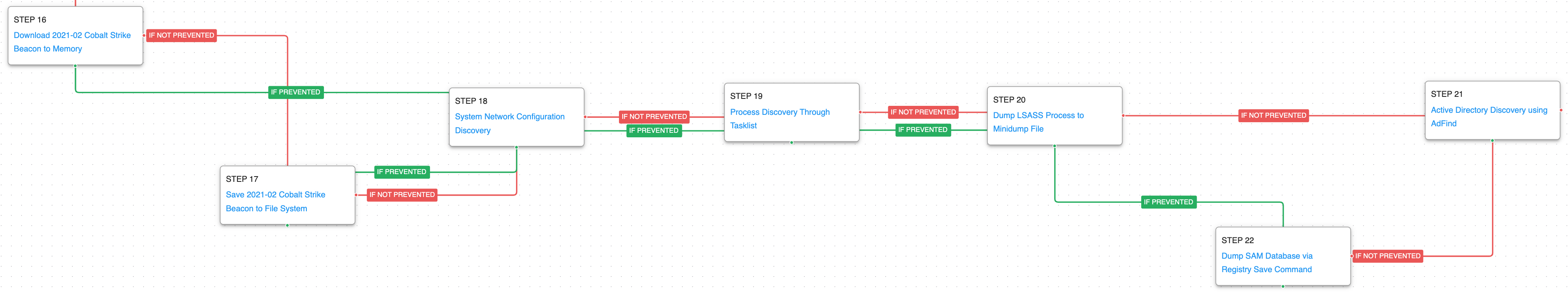 Click for Larger
Click for Larger Click for Larger
Click for Larger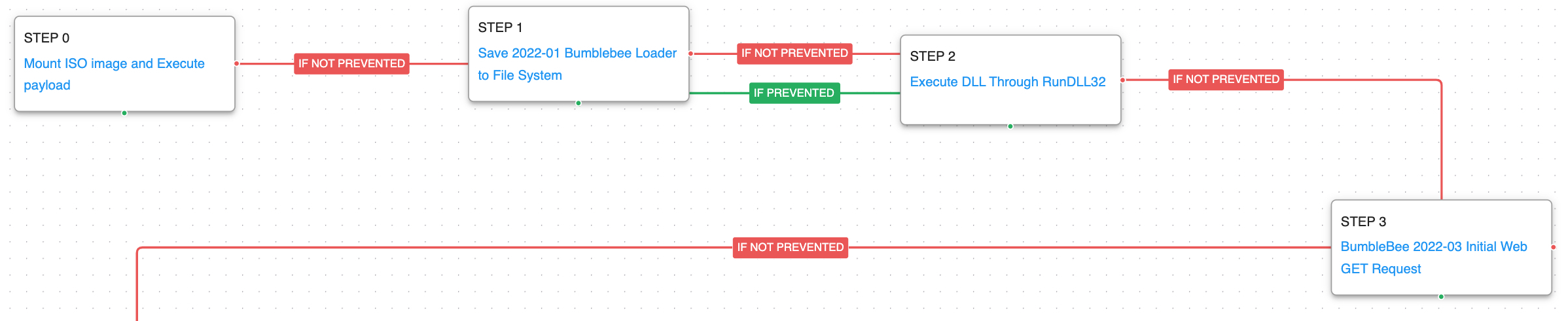 Click for Larger
Click for Larger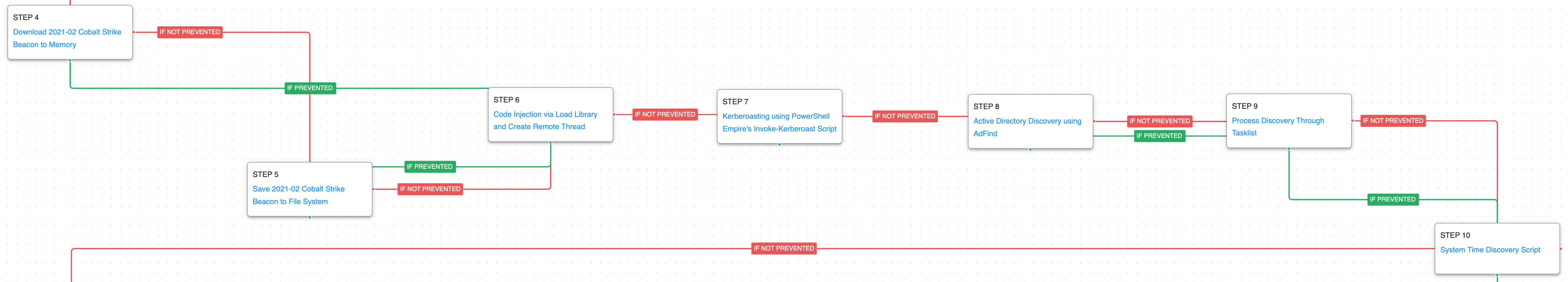 Click for Larger
Click for Larger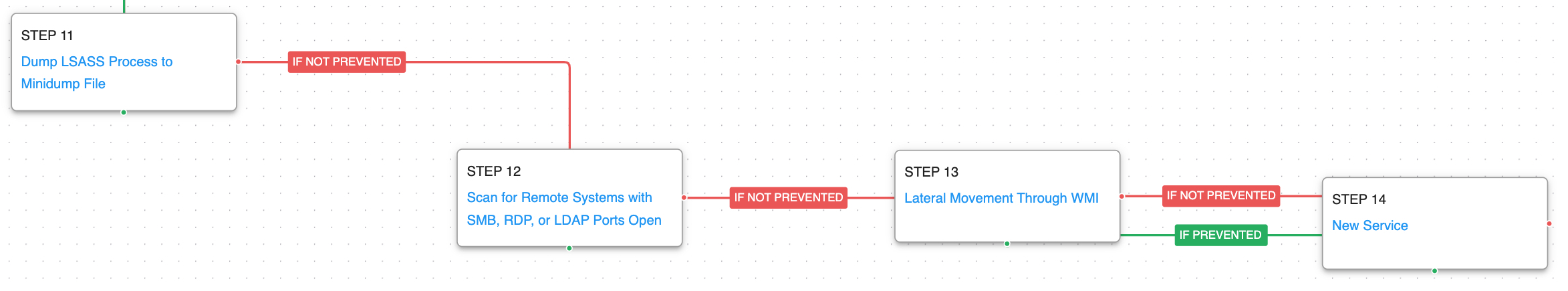 Click for Larger
Click for Larger
