Cyberattack
June 9, 2023
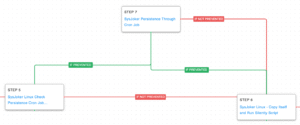
AttackIQ has released a new attack graph and two network security validation scenarios in response to the recently published CISA Advisory (AA23-158A) detailing the CL0P Ransomware Gang. This actor also known as TA505, is a financially motivated and highly sophisticated criminal adversary considered to be a major player in the e-crime scene that has left a significant impact on the global cybersecurity landscape.
September 23, 2022
AttackIQ has released a new fully featured attack graph that emulates the tactics, techniques, and procedures (TTPs) used by Iranian nation-state adversaries against the government of Albania.
August 2, 2022
AttackIQ’s Adversary Research Team has released a new Malware Emulation Attack Graph that emulates the Linux behaviors of the multi-platform backdoor known as SysJoker.
April 29, 2022
Uncover new attacks from a threat actor likely operating out of Belarus known as UNC1151 or Ghostwriter.
March 18, 2022
AttackIQ has released a new attack graph to emulate Russia-based threat actors as they exploit multi-factor authentication protocols to disable MFA. This blog describes the scenarios we have included in the new attack graph to emulate the adversary and then, to inform a purple team construct for cyberdefense operations, it provides detection and mitigation recommendations that you can use to improve your security program effectiveness. Read on for more.
March 11, 2022
AttackIQ and the Center for Threat-Informed Defense are furthering the art of adversary emulation with the Center’s new Attack Flow project. Building on our deep research partnership with the Center, AttackIQ’s Attack Graphs emulate the adversary with specificity and realism to test advanced cyberdefense technologies against multi-stage attacks. Read on for more.
March 8, 2022
To prepare for a potential cyberattack from Russia-based actors, you can begin by testing your security controls against known adversary tactics. The vast majority of cyberattacks use tactics and techniques that have been employed in the past. This blog walks you through key known tactics and techniques, and highlights scenarios in the AttackIQ Security Optimization Platform that you can use today to test your defenses and improve your cybersecurity readiness.
January 13, 2022
Attacks like Log4j, SolarWinds and Colonial Pipeline have board rooms across the nation questioning their preparedness in combating cybersecurity risks. What can boards do now to be more effective for the next big attack?
October 15, 2021
Recently, AttackIQ was notified that an Iranian threat actor had created a fake domain and fraudulent website (attackiq[.]ir) impersonating AttackIQ and abusing the company brand. This blog is an account of what happened and how AttackIQ responded, and it aims to provide insights to help organizations prepare to deal with similar Brand Reputation Abuse situations.
July 9, 2021
CFOs are often perceived as gatekeepers to the company’s cash coffers. With different functional leaders vying for project investments, it is true that the role of the CFO is to help prioritize the company’s spend, based on the business growth plan and trajectory.
March 23, 2021
AttackIQ’s new architecture upgrade makes it possible for customers to emulate comprehensive, multi-stage adversary cyberattack campaigns with realism and specificity, at every step in the kill chain. Check it out.
October 5, 2020
Last week, the U.S. government’s Cybersecurity and Infrastructure Security Agency (CISA) issued an alert to critical infrastructure owners and operators across the United States to be vigilant for potential Chinese cyberspace operations given heightened tensions between the two countries. What does the CISA alert recommend, and why is it important to follow it?
September 23, 2020
Cybersecurity does not exist in a vacuum and current socio-economic pressures make the United States more vulnerable to cyberattacks of all kinds. With the U.S. presidential election underway, Americans need to take practical steps to defend our democratic processes, online and off. This essay outlines some of the issues facing the United States in advance of the election, shares insights from AttackIQ’s recent podcast with leaders of Harvard’s Defending Digital Democracy project, and offers specific steps to manage the cybersecurity challenges of this moment.
August 19, 2020
Ransomware is on the rise, particularly against city government and hospitals. In advance of the 2020 U.S. presidential election, how does the AttackIQ Security Optimization Platform help businesses to defend themselves?
August 3, 2020
If you know AttackIQ, you probably know us as the leading independent vendor of Breach & Attack Simulation systems. We build the best security control validation solution available. So how is it that I say our business is not security testing?