Author: AttackIQ Team
September 23, 2022
AttackIQ has released a new fully featured attack graph that emulates the tactics, techniques, and procedures (TTPs) used by Iranian nation-state adversaries against the government of Albania.
September 21, 2022
AttackIQ has released a content bundle including two new attack graphs covering two historical APT28 campaigns involving their SkinnyBoy and Zebrocy malware families and standalone scenarios emulating command-and-control traffic to test boundary controls.
September 16, 2022
AttackIQ has released a new attack graph emulating the techniques used by Iranian actors to compromise and encrypt systems — without the need for malware — to help customers defend against threats that try to operate while living solely off the land.
September 8, 2022
AttackIQ has released a new attack graph emulating a Vice Society attack to help customers validate their security controls and their ability to defend against this threat actor and others who utilize similar behaviors.
August 2, 2022
AttackIQ’s Adversary Research Team has released a new Malware Emulation Attack Graph that emulates the Linux behaviors of the multi-platform backdoor known as SysJoker.
July 29, 2022
In this guest blog post, Bradley Schaufenbuel of Paychex writes about how security teams can leverage the MITRE ATT&CK framework to mount a “threat-informed” defense. This post originally appeared as an article in SC Magazine.
July 11, 2022
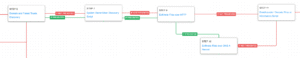
AttackIQ has released two new attack graphs that emulate different aspects of OilRig’s operations against multiple sectors around the globe. With these attack graphs, you can test and validate your defenses to improve cybersecurity readiness.
June 28, 2022
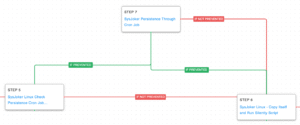
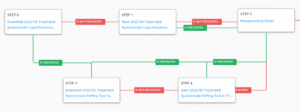
AttackIQ has released two new fully featured attack graphs emulating the tactics, techniques, and procedures (TTPs) used by likely nation-state adversaries that continue exploiting the Log4Shell vulnerability in VMware Horizon Systems.
June 24, 2022
In response to US-CERT Alert AA22-174A, AttackIQ has released new malware transfer scenarios to the platform and recommends validating security controls using previously released scenarios addressing Log4Shell and the VMware CVE-2022-22954 vulnerability.