Qilin is a ransomware strain operated under the Ransomware-as-a-Service (RaaS) model that emerged in July 2022. Initially, the group operated under the Agenda name, with its codebase written primarily in Go (Golang), targeting Windows environments and implementing basic double-extortion capabilities. Over time, the malware evolved into Qilin, rewritten in Rust, which provided enhanced performance, cross-platform support, and more sophisticated evasion techniques. This transition allowed the operators to expand targeting to Linux and ESXi environments, incorporate advanced mechanisms to bypass endpoint protections, improve encryption efficiency, and enable modular deployment for affiliates.
Qilin rapidly grew to be one of the most active ransomware groups in 2025, surpassing RansomHub in Q2, which was the leading ransomware for the previous three quarters. Qilin’s targets span various sectors, notably healthcare, education, and government, with high-profile incidents such as the 2024 attack on Synnovis, a UK-based medical laboratory, which disrupted services at multiple NHS hospitals.
The group employs advanced techniques like utilizing Bring Your Own Vulnerable Driver (BYOVD) to disable endpoint detection and response (EDR) tools, the ability to reboot systems into Safe Mode to evade defenses, and the deletion of shadow copies to prevent recovery. Qilin employs a combination of AES-256 and RSA-2048 encryption algorithms to encrypt files, making recovery without the decryption key virtually impossible.
AttackIQ has released a new attack graph that emulates the Tactics, Techniques, and Procedures (TTPs) associated with the deployment of Qilin ransomware to help customers validate their security controls and their ability to defend against this threat.
Validating your security program performance against these behaviors is vital in reducing risk. By using these new attack graphs in the AttackIQ Security Optimization Platform, security teams will be able to:
- Evaluate security control performance against baseline behaviors associated with the Qilin ransomware.
- Assess their security posture against an opportunistic adversary, which does not discriminate when it comes to selecting its targets.
- Continuously validate detection and prevention pipelines against a playbook similar to those of many of the groups currently focused on ransomware activities.
Malware Emulation
Qilin Ransomware – 2024-07 – Associated Tactics, Techniques and Procedures (TTPs)
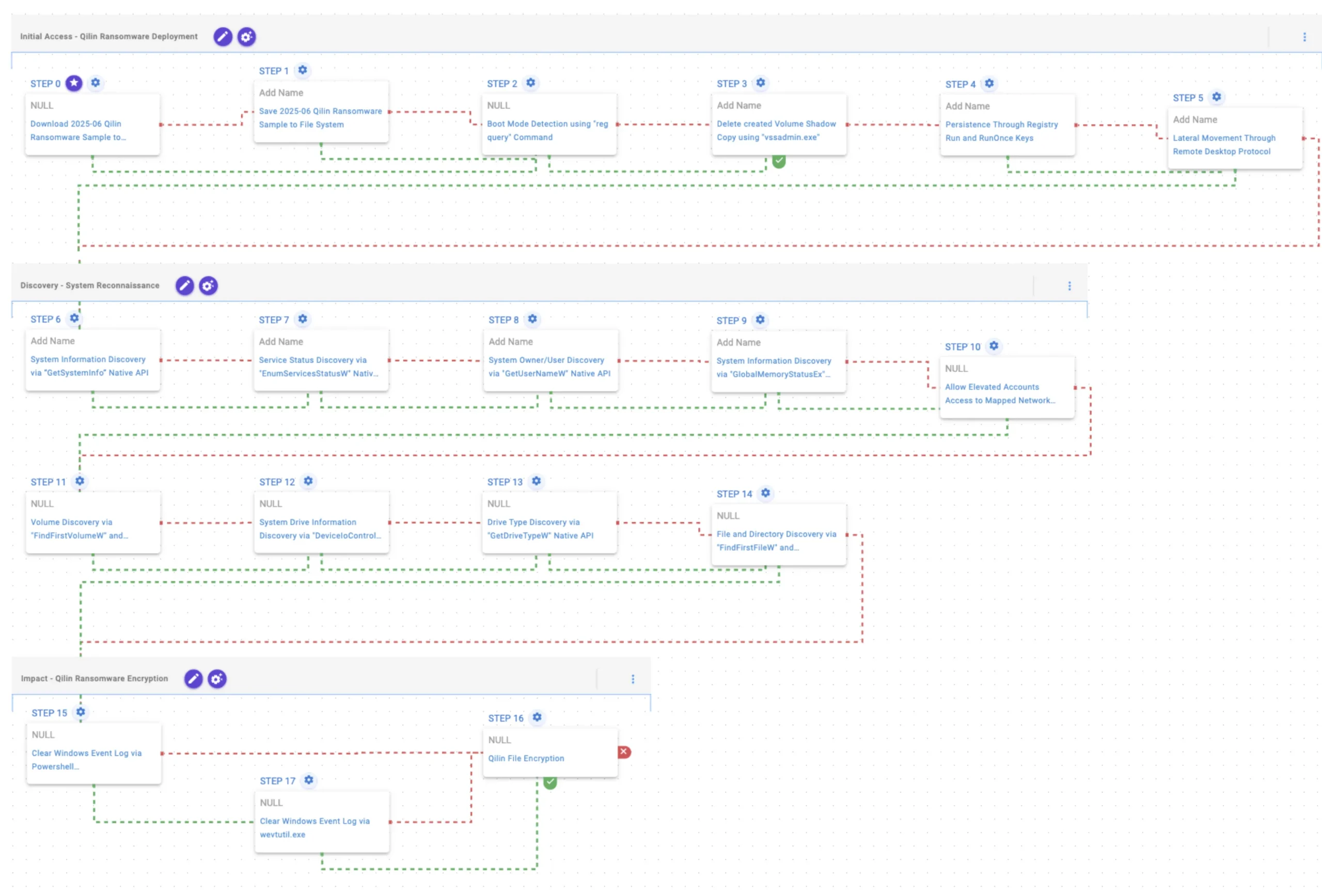
This emulation replicates the sequence of behaviors associated with the deployment of Qilin ransomware on a compromised system with the intent of providing customers with the opportunity to detect and/or prevent a compromise in progress.
The emulation is based on behaviors reported by TrendMicro on August 25, 2022, and December 16, 2022, and Group-IB on July 17, 2024.
Initial Access – Qilin Ransomware Deployment
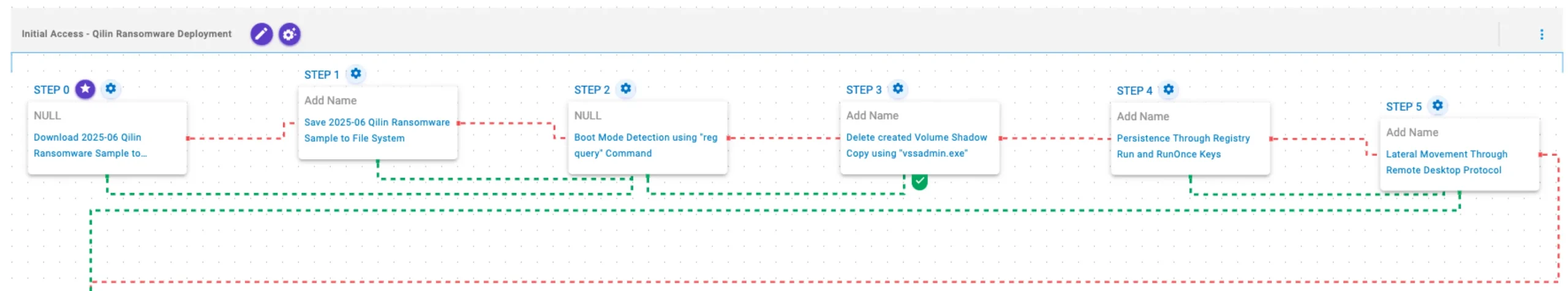
This stage starts with the deployment of Qilin ransomware, which first checks a registry value to determine whether the system is running in Safe Mode. After this validation, it executes vssadmin.exe to delete existing volume shadow copies, preventing system recovery. Then, it established persistence via a Windows Registry key. Finally, lateral movement is performed via Remote Desktop Protocol (RDP).
2025-06 Qilin Ransomware Sample (T1105): The Qilin Ransomware Sample (SHA256: e90bdaaf5f9ca900133b699f18e4062562148169b29cb4eb37a0577388c22527) is saved to disk in two separate scenarios to test network and endpoint controls and their ability to prevent the delivery of known malicious samples.
Boot Mode Detection using “reg query” Command (T1012): This scenario queries the SystemStartOptions registry key to uncover specific details about how the system is configured to start, for example to detect if the system was booted in Safe Mode.
Delete created Volume Shadow Copy using “vssadmin.exe” (T1490): This scenario executes the vssadmin.exe utility to delete a recent Volume Shadow Copy created by the assessment template.
Persistence Through Registry Run and RunOnce Keys (T1547.001): This scenario creates an entry under the HKLM\Software\Microsoft\Windows\CurrentVersion\Run registry key to be run at system startup and acquire persistence.
Lateral Movement Through Remote Desktop Protocol (T1021.001): This scenario attempts to move laterally within a network using the Remote Desktop Protocol (RDP) protocol.
Discovery – System Reconnaissance
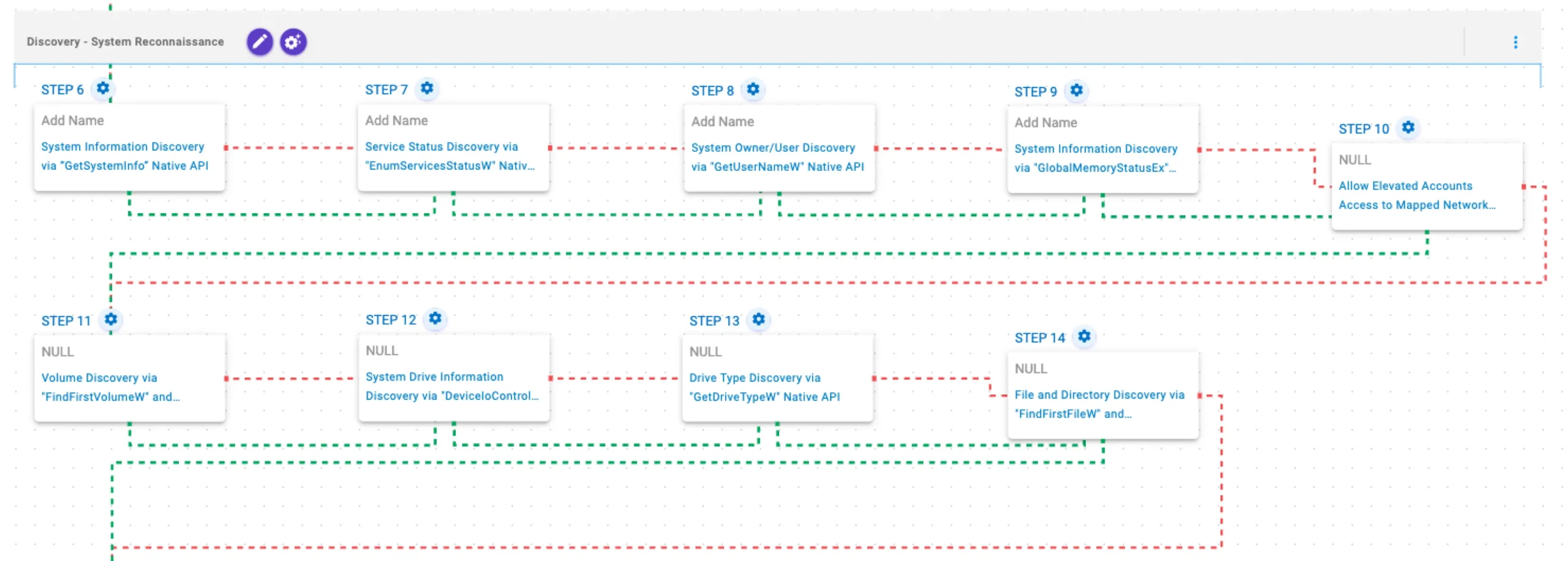
This stage performs a discovery routine to collect system information from the local computer through Windows APIs, with the purpose of supporting the subsequent encryption process. In addition, the EnableLinkedConnections registry value is modified to ensure that mapped network drives are accessible, allowing them to be included during encryption.
System Information Discovery via “GetSystemInfo” Native API (T1082): This scenario executes the GetSystemInfo Windows native API call to retrieve system information. This can be used to detect sandboxes, create unique identifiers, and adjust execution behaviors.
Service Status Discovery via “EnumServicesStatusW” Native API (T1007): This scenario executes the EnumServicesStatus Windows native API call to gather critical information about configured services on a compromised system, such as service name, service display name, and current service status.
System Owner/User Discovery via “GetUserNameW” Native API (T1033): This scenario executes the GetUserNameW Windows native API call to retrieve the account name associated with the local computer.
System Information Discovery via “GlobalMemoryStatusEx” Native API (T1082): This scenario executes the GlobalMemoryStatusEx Windows API call to gather information about physical and virtual memory.
Allow Elevated Accounts Access to Mapped Network Drives via Registry (T1112): This scenario modifies the EnableLinkedConnections registry key to make sure mapped drives are accessible even during User Account Control (UAC) launched processes.
Volume Discovery via “FindFirstVolumeW” and “FindNextVolumeW” Native API (T1082): This scenario executes the FindFirstVolumeW and FindNextVolumeW Windows API calls to iterate through the available volumes of the system.
System Drive Information Discovery via “DeviceIoControl” Native API (T1082): This scenario executes the DeviceIoControl Native API function to retrieve system drive information, such as the serial number, to profile the target’s system.
Drive Type Discovery via “GetDriveTypeW” Native API (T1120): This scenario retrieves information about the system’s physical disks using the GetDriveTypeW Windows API call.
File and Directory Discovery via “FindFirstFileW” and “FindNextFileW” Native API (T1083): This scenario executes the FindFirstFileW and FindNextFileW Windows native API calls to enumerate the file system.
Impact – Qilin Ransomware Encryption
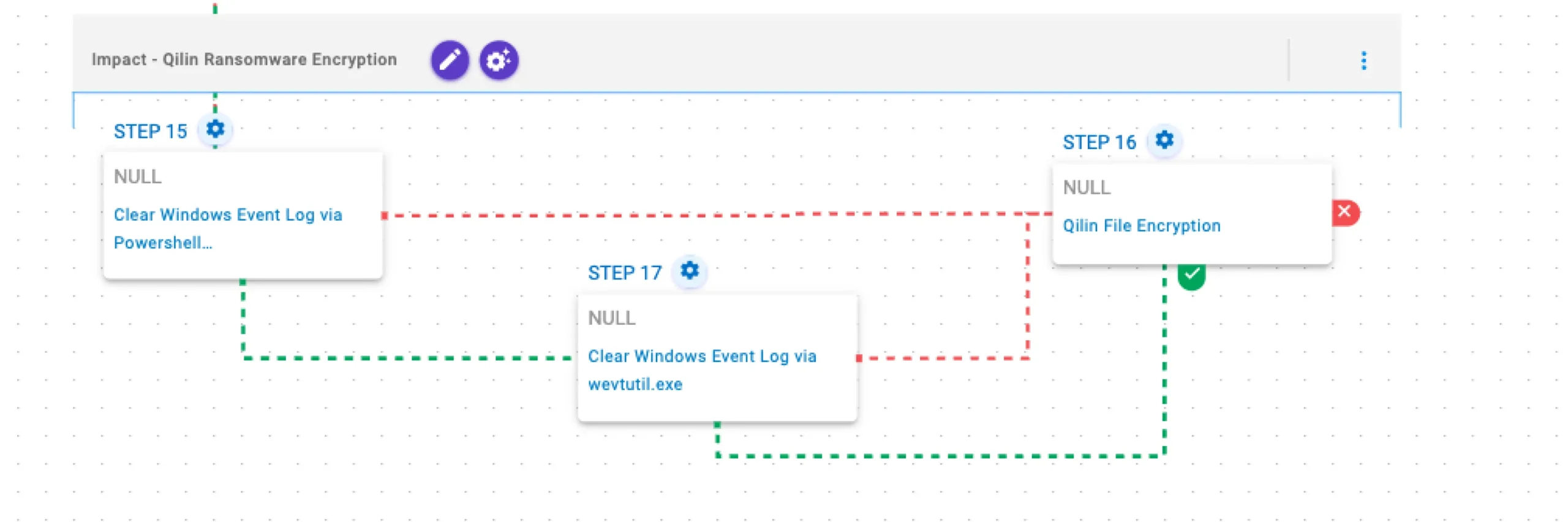
This stage begins with the clearing of Windows event logs using PowerShell, falling back to wevtutil.exe if the PowerShell method fails. Targeted files are subsequently encrypted with AES-256 in CTR mode for file encryption and RSA-2048 to protect the encryption key.
Clear Windows Event Log via Powershell GlobalSession.ClearLog (T1070.001): This scenario uses the GlobalSession.ClearLog Powershell cmdlet to clear Windows Event Logs from the system.
Qilin File Encryption (T1486): This scenario performs the file encryption routines used by common ransomware families. Files matching an extension list are identified and encrypted in place using similar encryption algorithms as used by Qilin ransomware.
Clear Windows Event Log via wevtutil.exe (T1070.001): The scenario uses the wevtutil.exe binary to clear event logs from the system.
Opportunities to Expand Emulation Capabilities
In addition to the released attack graph, AttackIQ recommends the following scenario to extend the emulation of the capabilities exhibited by Qilin Ransomware:
- Execute Power Shell Script in Remote System with PaExec: This scenario simulates the execution of a PowerShell script on a remote machine using PaExec, an open-source version of PSExec.
- Domain Controller Remote System Discovery via Powershell Script: This scenario executes the
Get-ADComputerPowershell cmdlet to get the list of Active Directory computers, showing the name, hostname and installed operating system.
Wrap-up
In summary, this emulation will evaluate security and incident response processes and support the improvement of your security control posture against the behaviors exhibited by Qilin ransomware. With data generated from continuous testing and use of this assessment template, you can focus your teams on achieving key security outcomes, adjust your security controls, and work to elevate your total security program effectiveness against a known and dangerous threat.
AttackIQ, the leading provider of Adversarial Exposure Validation (AEV) solutions, is trusted by top organizations worldwide to validate security controls in real time. By emulating real-world adversary behavior, AttackIQ closes the gap between knowing about a vulnerability and understanding its true risk. AttackIQ’s AEV platform aligns with the Continuous Threat Exposure Management (CTEM) framework, enabling a structured, risk-based approach to ongoing security assessment and improvement. The company is committed to supporting its MSSP partners with a Flexible Preactive Partner Program that provides turn-key solutions, empowering them to elevate client security. AttackIQ is passionate about giving back to the cybersecurity community through its free award-winning AttackIQ Academy and founding research partnership with MITRE Center for Threat-Informed Defense.