Kimsuky, also known as Thallium or Velvet Chollima, is a state-sponsored politically motivated adversary believed to be operating on behalf of North Korea. Active since at least 2012, Kimsuky has been observed leading numerous activities with the primary objective of gathering intelligence on South Korea and other targets of interest to the Democratic People’s Republic of Korea (DPKR).
The adversary has been associated with attacks targeting entities related to South Korean politics, government, and military, as well as on individuals and organizations involved in Korean reunification efforts. Numerous reconnaissance campaigns have been led by Kimsuky, with the goal of gathering valuable information to support future full-scale operations.
Kimsuky is widely recognized for its expert use of social engineering techniques, employing them to great effect in its malicious campaigns. The adversary is known to leverage upcoming geopolitical events, such as inter-Korean summits, to lure unsuspecting targets into opening malicious documents received via spear-phishing emails.
Kimsuky has shown a remarkable level of consistency in its infection chains over the years, often relying on the same or similar malware families. However, the adversary has demonstrated flexibility in its approach, changing the infection vector used in different cases to avoid detection and improve its chances of success.
AttackIQ has released four new attack graphs emulating the adversary’s reconnaissance operations to help customers validate their security controls and their ability to defend against a highly effective and dangerous threat actor. Validating your security program performance against these behaviors is vital to reducing risk. By using these new attack graphs in the AttackIQ Security Optimization Platform, security teams will be able to:
- Emulate a significant portion of North Korea’s intelligence-centric clandestine operations.
- Assess the security posture against a threat actor that specializes in social engineering and employs deceptive attacks as their primary tactics.
- Continuously validate detection and prevention effectiveness against the techniques continuously used by this North Korean adversary.
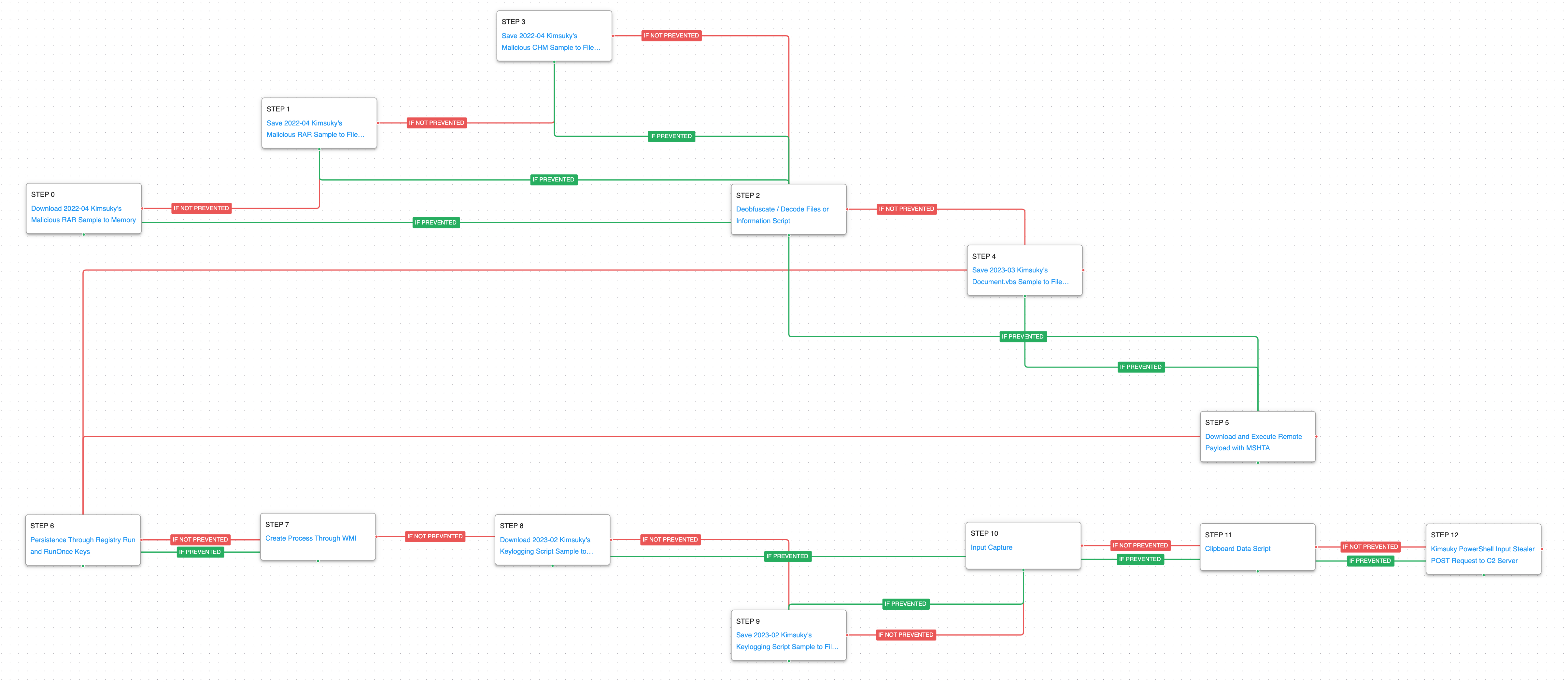
Kimsuky – 2023-03 – Compiled HTML Help (CHM) File Leads USER-based Infection Chain
The first attack graph is primarily based on a series of attacks reported by AhnLab in March 2023, May 2022, and March 2022. This infection chain focuses on the use of Compiled HTML Help (CHM) files as a delivery vector to perform user-specific reconnaissance operations. These CHM files typically arrive compressed and are distributed as email attachments, often containing information related to the political situation between South and North Korea.
This emulation starts with downloading and saving the malicious RAR file used by Kimsuky as the initial access vector. This RAR file contains the Compiled HTML Help (CHM) file used to carry out the attack, which is then deobfuscated using the certutil utility and, if not prevented, continues with the saving of a Visual Basic Script (VBS) on the system. In case the deobfuscation task is prevented, the attack graph will use the MSHTA utility, which aims to download and execute Microsoft HTML Applications (HTA).
Ingress Tool Transfer (T1105): This scenario downloads to memory and saves to disk in two separate scenarios to test network and endpoint controls and their ability to prevent the delivery of known malicious samples.
Deobfuscate/Decode Files or Information (T1140): This scenario uses the legitimate certutil binary to decode a base64 encoded payload.
System Binary Proxy Execution: Mshta (T1218.010): Mshta.exe is a native Windows utility that threat actors can abuse to download remote payloads that include VBScript code.
In the attack’s second stage, the adversary will seek persistence through a Registry Run Key, which is followed by the creation of a new process through Windows Management Instrumentation (WMI). This process will be responsible for downloading and saving the script used to collect system information, such as keystrokes and clipboard data. This stage culminates with the exfiltration of the information via an HTTP POST request to the C2 server.
Logon Autostart Execution: Registry Run Keys (T1547.001): This scenario sets the HKLM\Software\Microsoft\Windows\CurrentVersion\Run and RunOnce registry keys that Windows uses to identify what applications should be run at system startup.
Windows Management Instrumentation (WMI) (T1047): This scenario creates a new process using WMI, a native Windows administration feature that provides a method for accessing Windows system components.
Input Capture: Keylogging (T1056.001): A keylogger is executed that hooks API callbacks to collect keystrokes typed by a logged in user.
Clipboard Data (T1115): This scenario copies data stored in the clipboard through the execution of a PowerShell script.
Application Layer Protocol: Web Protocols (T1071.001): This scenario emulates the HTTP requests made by Kimsuky by making an HTTP POST to an AttackIQ server that mimics the format used during the real infection.
Kimsuky – 2023-02 – Office Document-based Campaign against Security-related Organizations
This second emulation is based on a series of reports released by AhnLab in February 2023, January 2023, and March 2021.
In this infection chain Kimsuky used a malicious Microsoft Office Word document to distribute malware to security-related companies. The adversary made use of malicious Word macros, the goal of which was to generate and execute a batch script. This batch script would download and save a decoy document and a malicious script via curl commands.
It is suspected that the main objective of this wave of attacks was to identify potential victims for more complex infection chains in the future.
During the first stage of the attack, all files used by Kimsuky are downloaded and saved. At the beginning, a malicious Office document is downloaded and saved, which in turn contains the relationships XML file that will be saved in the file system when opened. Once this step is completed, the attack graph continues the delivery of a remote template Office document, which contains macros that are used to drop additional payloads to disk. This first stage ends with downloading a batch file called version.bat.
The second stage continues the delivery of additional files used in the attack including a decoy document and a malicious VBScript. This is followed by the creation of a service via WMI and ending with the download of a malicious PowerShell script.
In the third and last stage of the attack, the actor performs a handful of discovery actions to collection information about the infected system. The creation of a scheduled task results in the exfiltration of the collected data by means of HTTP POST requests.
System Information Discovery (T1082): The native systeminfo command is executed to retrieve all of the Windows system information.
File and Directory Discovery (T1083): This scenario uses the native dir command to find files of interest and output to a temporary file.
Process Discovery (T1057): Window’s built-in tasklist command is executed as a command process and the results are saved to a file in a temporary location.
Security Software Discovery (T1518.001): A PowerShell script is executed to determine which software has been installed as an AntiVirusProduct class.
Scheduled Task/Job: Scheduled Task (T1053.005): This scenario creates a new scheduled task using the schtasks utility.
Exfiltration Over C2 Channel (T1041): System profiling data is sent to an AttackIQ controlled server using HTTP POST requests.
Kimsuky – 2022-11 – Campaign against Nuclear Power Plant-related Companies with AppleSeed
The third Kimsuky attack graph is based on a report published by AhnLab in November 2022 and is supplemented by information published by an additional source in July 2022.
During this attack, Kimsuky was observed distributing the AppleSeed backdoor to companies related to Nuclear Power Plants located in South Korea. The files containing the AppleSeed droppers use a double file extension technique to trick users. Once the payload is executed, a DLL file is dropped and executed. At the same time, a decoy Excel document is opened, giving the appearance that the user has opened a benign document.
This attack’s objective was to obtain sensitive information from the compromised system, receive and execute commands via the backdoor, exfiltrate the collected information, and download and execute additional malware payloads.
The first stage begins with downloading and saving the AppleSeed JSE dropper, an encoded JScript file that is used to drop and execute the AppleSeed backdoor DLL. Subsequently, an encoded file is deobfuscated using a native Windows utility. Next, AppleSeed is saved and executed by means of RegSvr32 which continues with the initial command-and-control requests. This stage culminates with the obtaining of persistence by means of Registry Run Keys.
System Binary Proxy Execution: Regsvr32 (T1218.010): RegSvr32 is a native Windows utility that threat actors can use to register Common Object Model (COM) DLLs. This functionality allows an actor to deploy a malicious DLL and have a native Windows tool execute the code as the parent process. This scenario executes RegSvr32 with an AttackIQ binary.
The second stage of the attack is the system information discovery phase. During this stage, AppleSeed will seek to collect as much information as possible from the system for later exfiltration.
System Network Configuration Discovery (T1016): Native Window’s commands like route, ipconfig, and net use are executed to collect details about the infected host and network shares.
System Owner / User Discovery (T1033): Live off the land by running whoami and users to gain details about the currently available accounts and permission groups.
Account Discovery (T1087): Use living off the land commands like net user to obtain a list of additional accounts known to the infected host.
In the last stage of the attack, the information collected in the previous stage will be staged and exfiltrated by means of an HTTP POST request. Finally, a remote payload is downloaded and executed using the Microsoft HTML Application (MSHTA) utility.
Data Staged: Local Data Staging (T1074.001): Files are collected and stored in a temporary directory so they can be exfiltrated later.
Exfiltration Over C2 Channel (T1041): A large amount of data is exfiltrated over HTTP requests mimicking the data exfiltration method used by the adversary actors.
Kimsuky – 2022-11 – Malicious Word Document Culminates in Reconnaissance Campaign
The final attack graph is based on two reports published by AhnLab in November 2022 and September 2022.
Kimsuky was observed distributing a password-protected Word document, which masquerades as an interview document from a CNA Singapore TV show with the goal of enticing victims to open the file and enable the embedded VBA macro.
The successful execution of the malicious macro will create and execute a VBScript which is used to download and execute additional payloads in the compromised system. Kimsuky’s objective in this campaign was to conduct reconnaissance activities on the compromised systems, exfiltrate sensitive data, and potentially establish a foothold for future full-scale operations.
The emulation begins with download and saving the malicious Word document used by Kimsuky, which continues with the dropping of a Shortcut (LNK) file to system. Subsequently, a script is downloaded and saved, which obtains persistence by means of Registry Run Keys.
In the second stage of the attack, the discovery phase is carried out execute the same commands observed in previous reporting. This stage ends with the exfiltration of the collected profiling information.
In final stage of the attack, Kimsuky first seeks to achieve persistence through the startup folder, prior to modifying office security settings via Registry. Next, the actor will seek additional information regarding the files available on the system, which is later staged prior to exfiltration via an FTP connection.
Logon Autostart Execution: Startup Folder (T1547.001): The Startup folder is a directory associated with the Windows Start Menu that can be used to launch a process at Windows logon. This scenario creates a binary file in this directory that would execute at the next logon for users.
Exfiltration Over Asymmetric Encrypted Non-C2 Protocol (T1048.002): This scenario will start an FTP connection against an AttackIQ server, emulating the exfiltration of data performed by Kimsuky.
Detection and Mitigation Opportunities
With so many different techniques being used by threat actors, it can be difficult to know which to prioritize for prevention and detection assessment. AttackIQ recommends first focusing on the following techniques:
1. Ingress Tool Transfer (T1105)
This actor relies heavily in downloading additional stages of malware. Endpoint and Network security controls should both be employed to try and detect the delivery of these malicious payloads.
1a. Detection
The following signatures can help identify when native utilities are being used to download malicious payloads.
PowerShell Example:
Process Name == (Cmd.exe OR Powershell.exe)
Command Line CONTAINS ((“IWR” OR “Invoke-WebRequest") AND “DownloadData” AND “Hidden”)
1b. Mitigation
MITRE ATT&CK has the following mitigation recommendations.
2. System Binary Proxy Execution: Rundll32 (T1218.011) and Regsvr32 (T1218.010)
Kimsuky uses DLL files for many of their malware payloads and uses native Windows utilities to execute them. The primary native methods for executing these files is to call the RunDll32 or RegSvr32 utilities and pass along the path and export function to be executed.
2a. Detection
While these two native tools are commonly used by legitimate applications there are behaviors related to their execution that can stand out in your process logs. Searching for files that are being executed from temporary directories, that don’t have the standard .dll file extension, or call strange looking export names can stand out from regular user behavior.
Process Name == (rundll32.exe OR regsvr32.exe)
Command Line CONTAINS (‘TEMP’ OR ‘.png’ OR ‘Roaming’ OR ‘%APPDATA%’)
2b. Mitigation
3. Logon Autostart Execution: Registry Run Keys (T1547.001):
Preventing an actor from maintaining a foothold in your environment should always be one of the top priorities. In both campaigns, Registry Run keys were used to keep many of their malware families running after a reboot. The actor’s abused their access over multiple days and a simple reboot would have prevented their actions if the persistence couldn’t be established.
3a. Detection
Using a SIEM or EDR Platform to see modifications to the Run and RunOnce keys will alert when unauthorized users or software makes modifications to the keys that allow programs to run are startup.
Process Name == reg.exe
Command Line Contains (“ADD” AND “\CurrentVersion\Run”)
3b. Mitigation
MITRE ATT&CK does not have any direct mitigations as this is abusing legitimate Windows functionality. They recommend monitoring registry changes and process execution that may attempt to add these keys.
Wrap-up
In summary, these attack graphs will evaluate security and incident response processes and support the improvement of your security control posture against a North Korean threat actor who has abused the same techniques for years. With data generated from continuous testing and use of these attack graphs, you can focus your teams on achieving key security outcomes, adjust your security controls, and work to elevate your total security program effectiveness against a known and dangerous threat.
AttackIQ stands at the ready to help security teams implement this attack graph and other aspects of the AttackIQ Security Optimization Platform, including through our co-managed security service, AttackIQ Vanguard.
 (Click for Larger)
(Click for Larger) (Click for Larger)
(Click for Larger)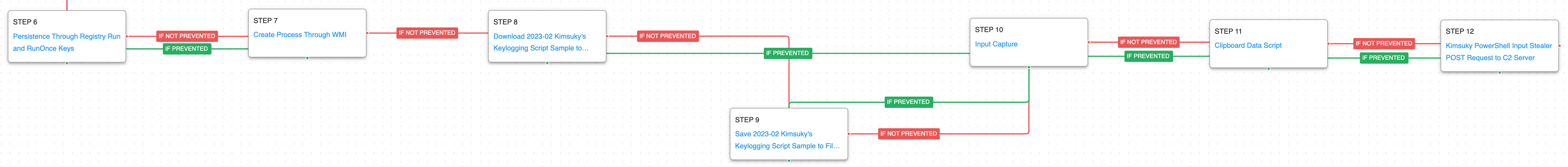 (Click for Larger)
(Click for Larger)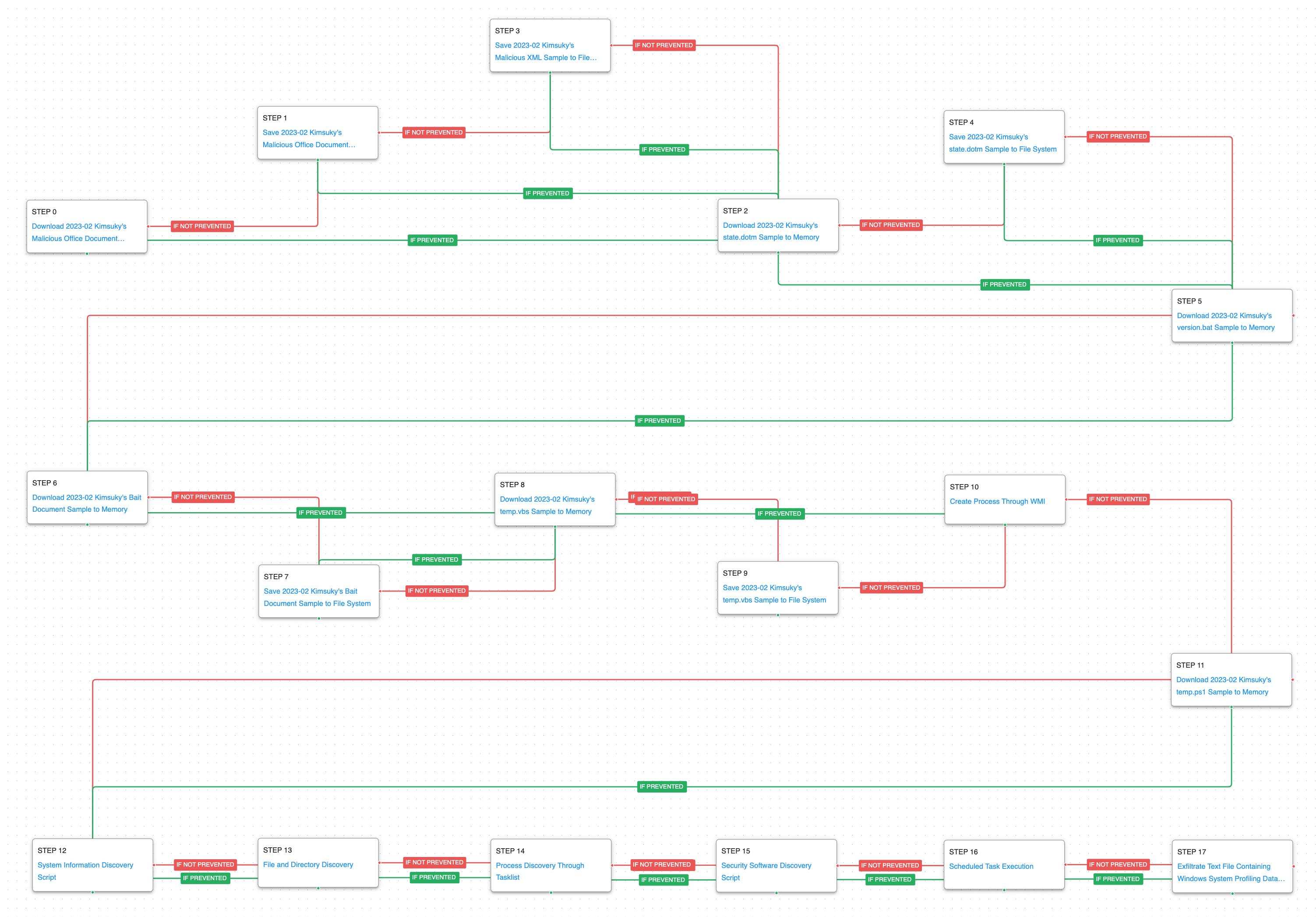 (Click for Larger)
(Click for Larger)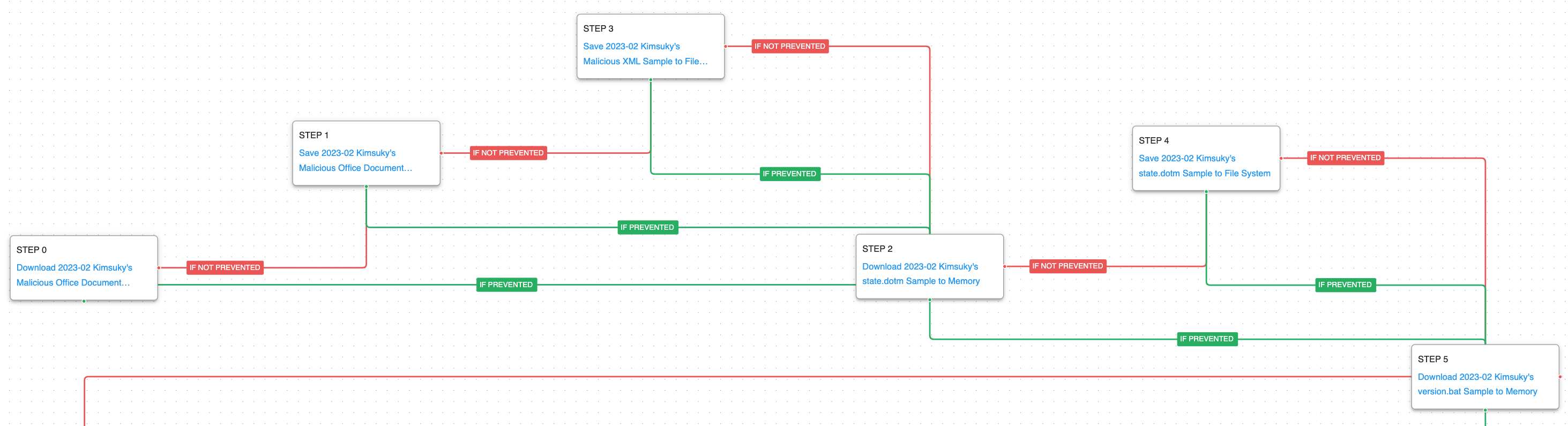 (Click for Larger)
(Click for Larger)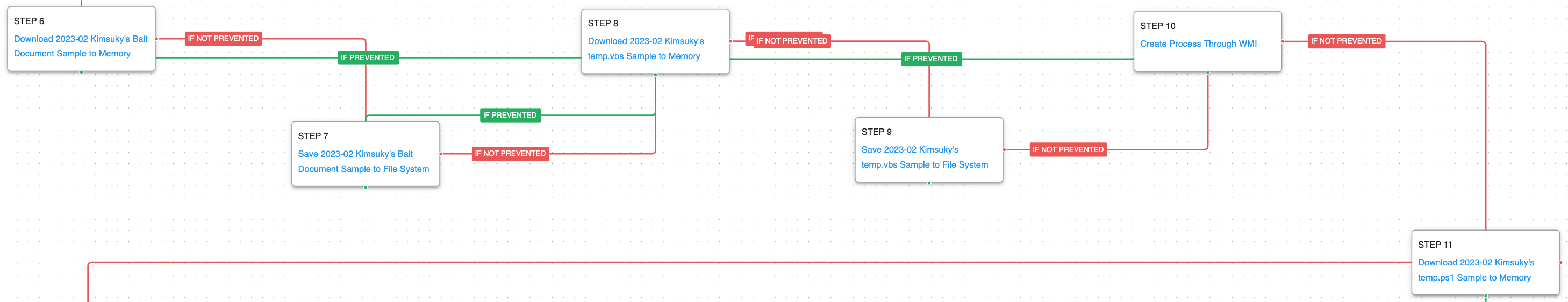 (Click for Larger)
(Click for Larger) (Click for Larger)
(Click for Larger)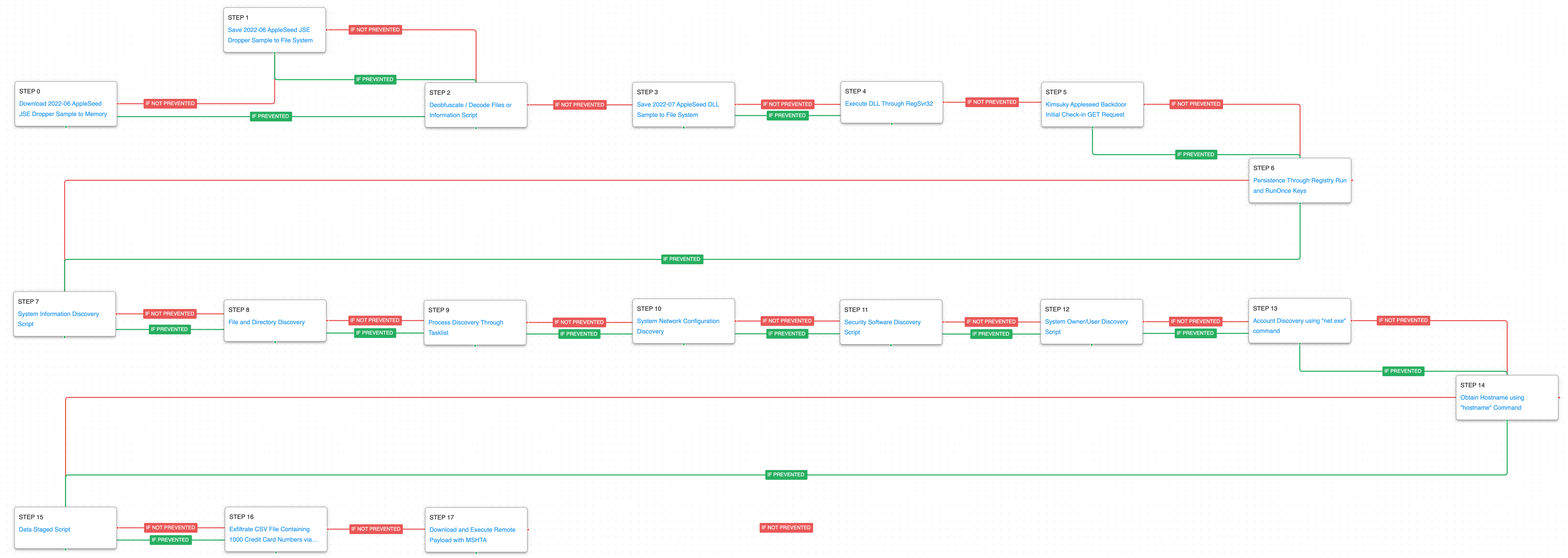 (Click for Larger)
(Click for Larger)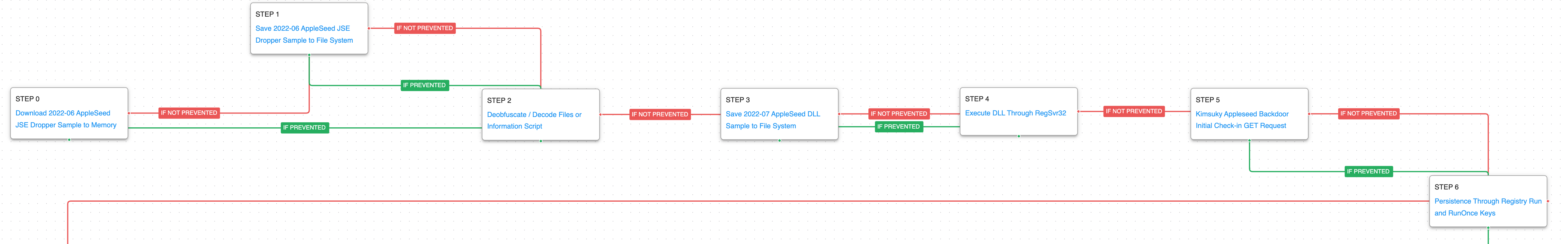 (Click for Larger)
(Click for Larger) (Click for Larger)
(Click for Larger) (Click for Larger)
(Click for Larger)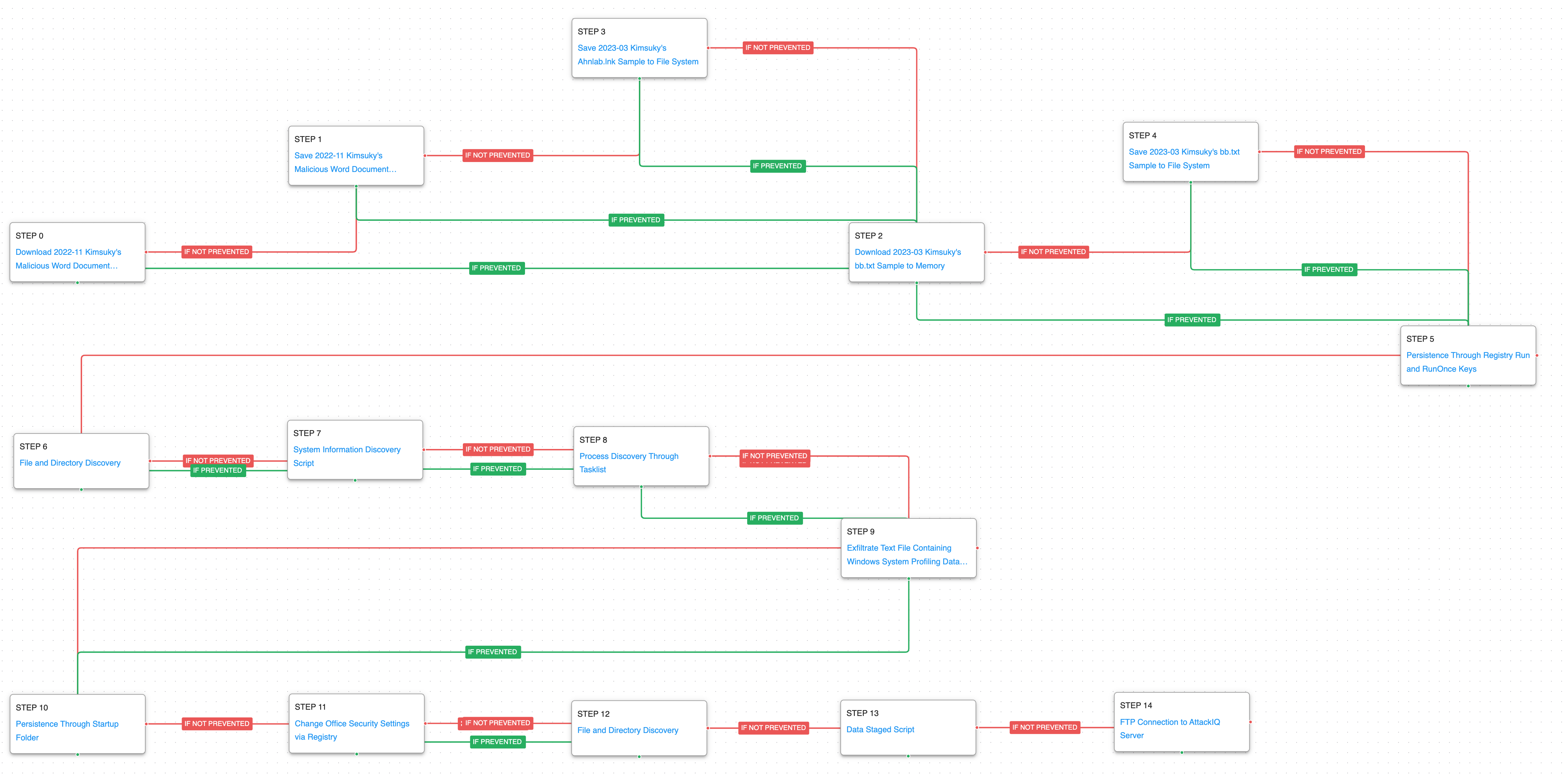 (Click for Larger)
(Click for Larger) (Click for Larger)
(Click for Larger)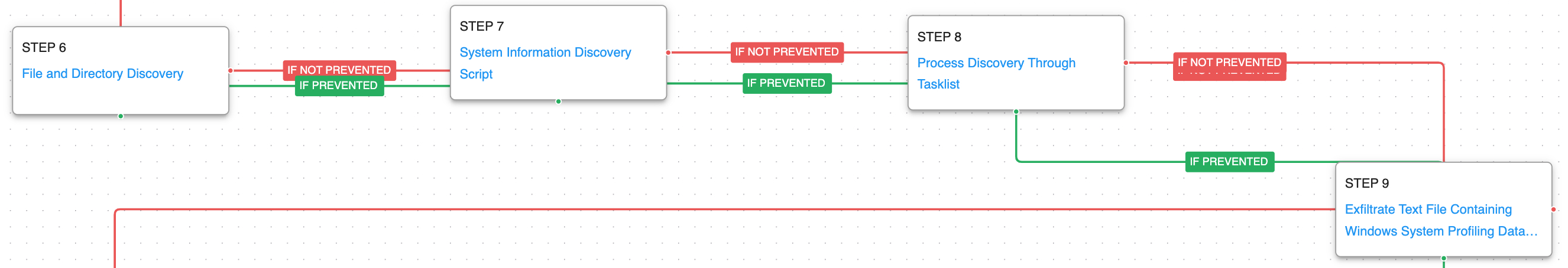 (Click for Larger)
(Click for Larger)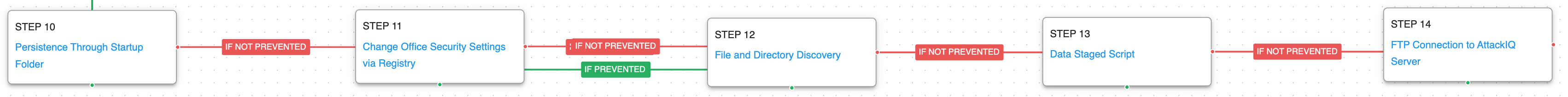 (Click for Larger)
(Click for Larger)
