OilRig, also known as APT34, is a state-sponsored Iranian adversary who was first identified in 2012 by Symantec during a wave of destructive attacks against the Middle East. The threat actor’s attacks have consistently aligned to Iran’s national interests and have targeted multiple sectors around the globe. Their victims have been primarily in Government, Financial Services, Energy, Resources & Utilities, Manufacturing, Telecommunications, and Technology industries.
Researchers reported in February 2023 that OilRig carried out an attack in August 2022 leveraging a malicious Word document as the initial access vector. Historical attacks from this adversary were previously emulated by AttackIQ in July 2022, and today we are releasing a new attack graph updated to cover their recent abilities.
The malicious document is masquerading as a job application form from a technology and telecommunications organization. Once the file was opened, embedded macros proceeded to multiple scripts and establish persistence with a scheduled task named “WindowsUpdate”.
During the attack, OilRig used native Windows utilities and PowerShell cmdlets to discover and collect system information. Additionally, OilRig used an AutoHotkey script to record keystrokes from the infected host and a PowerShell script to take screenshots of the active user.
AttackIQ has released this new attack graph emulating the latest activity carried out by OilRig in order to expand our emulation of this adversary’s behavior. Validating your security program performance against these behaviors is vital to reducing risk. By using these new attack graphs in the AttackIQ Security Optimization Platform, security teams will be able to:
- Evaluate security control performance against the latest iteration of this Iranian threat actor.
- Assess their security posture against an actor using native living off the land techniques to achieve their goals.
- Continuously validate detection and prevention pipelines against attacks that leverages PowerShell functionality to complete their discovery objectives.
OilRig – 2022-08 – VBA Macro leads to Discovery, Collection and Exfiltration Routines
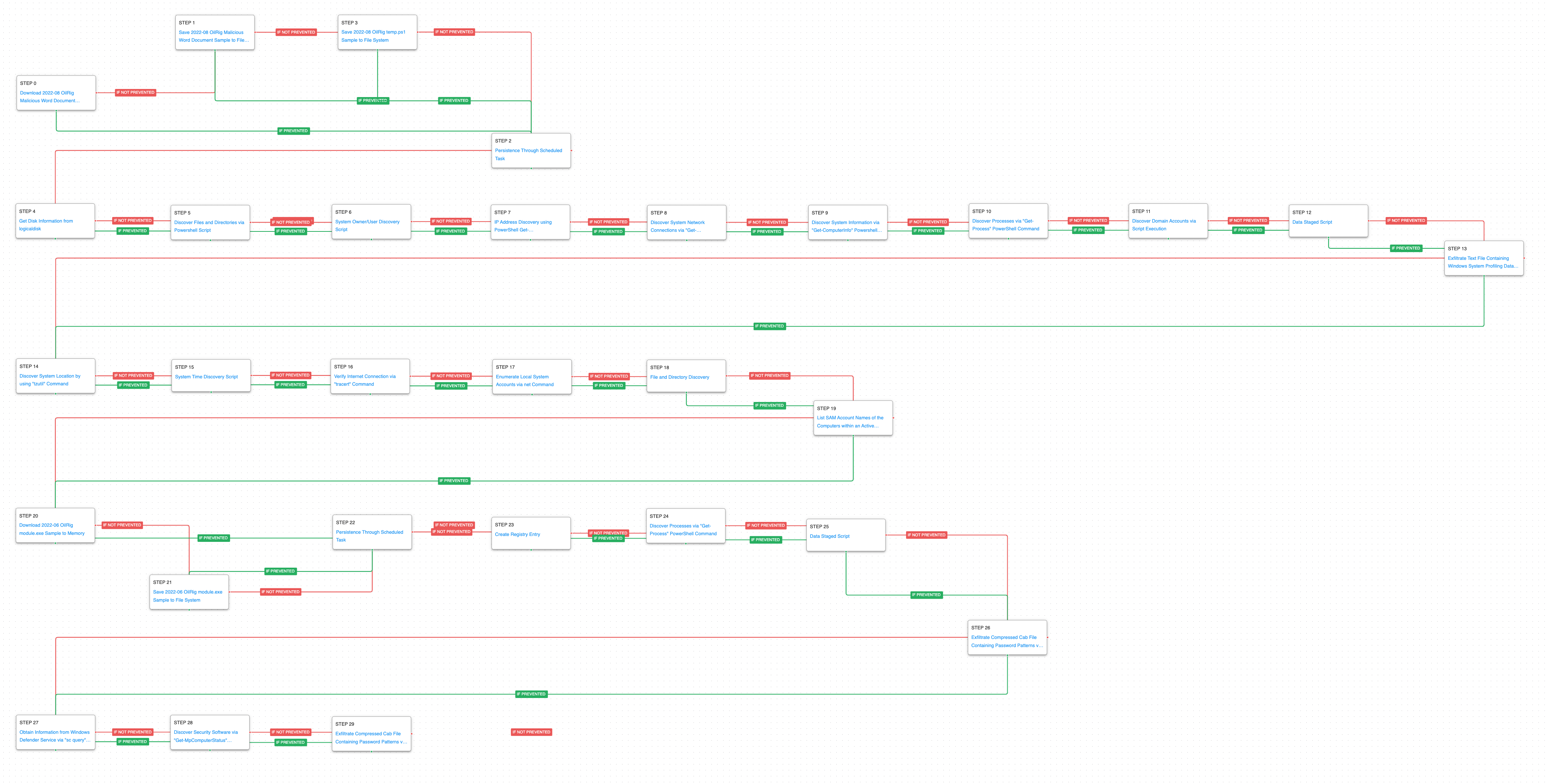
The attack graph begins with downloading and saving the malicious Word document used for initial access. The document drops additional payloads including a PowerShell script that has the capability to receive and execute base64 encoded commands obtained from the C2 server. The first stage culminates with establishing persistence through the creation of a scheduled task.
Ingress Tool Transfer (T1105): This scenario downloads to memory and saves to disk in independent scenarios to test both network and endpoint controls and their ability to prevent the delivery of known malicious files.
Scheduled Task/Job: Scheduled Task (T1053.005): This scenario creates a new scheduled task using the schtasks utility with the name WindowsUpdate that was observed being used in these attacks.
The second stage of the attack is focused on discovery and information-gathering tasks performed by OilRig through the use of native Windows utilities and PowerShell cmdlets.
Windows Management Instrumentation (WMI) (T1047): This scenario executes the logicaldisk command to retrieve details on the system’s disks.
File and Directory Discovery (T1083): The actors used the PowerShell Get-ChildItem cmdlet to recursively query a series of folders and list all of the files.
System Owner/User Discovery (T1033): Executes the native query user and whoami commands to receive details of the running user account.
System Network Configuration Discovery (T1016): PowerShell is used to collect information about the system’s network configuration by leveraging the Get-NetIPConfiguration cmdlet.
System Network Connections Discovery (T1049): The PowerShell cmdlet Get-NetTCPConnection is used to get a list of current TCP connections.
System Information Discovery (T1082): PowerShell is continued to be used to collect information about the host including the operating system information and hardware configuration by using the Get-ComputerInfo cmdlet.
Process Discovery (T1057): This scenario uses the Get-Process PowerShell cmdlet to get a list of all the running processes.
Account Discovery: Domain Account (T1087.002): PowerSploit and PowerShell are used to get information about the domain administrator account.
Data Staged (T1074): This scenario identifies Office documents and copies them to a temporary staging directory.
Exfiltration Over C2 Channel (T1041): System profiling data is sent to an AttackIQ controlled server using HTTP POST requests.
The third stage of the activity begins with the adversary seeking to obtain additional system information, such as the geographic location of the compromised host and then enumerate local and domain accounts.
System Location Discovery (T1614): Use the native Windows command tzutil to get the time zone of the infected host.
System Time Discovery (T1124): The scenario identifies the time and time zone of the compromised system through the net time command.
Internet Connection Discovery (T1016.001): The actor uses the tracert utility to verify network accessibility to a remote IP address.
Account Discovery: Local Account (T1087.001): A list of local accounts configured on this host is collected by executing the net user command.
File and Directory Discovery (T1083): A batch script is executed that lists all files and directories in %ProgramFiles% and the %systemdrive%\Users directory.
Account Discovery: Domain Account (T1087.002): This scenario uses PowerShell to search for all the computers in a network and displays their names and operating systems.
Subsequently, the graphical attack downloads and saves the keylogger used by OilRig and it is then given persistence by creating a new scheduled task. Keylogging data is saved to a registry key which is compressed before its exfiltration.
Modify Registry (T1112): This scenario sets the same registry key used by the actor for storing keylogging data: HKEY_CURRENT_USER\SOFTWARE\GetKeypressValue.
Process Discovery (T1057): PowerShell is used to get a list of running processes using the Get-Process cmdlet.
Archive Collected Data: Archive via Utility (T1560.001): The actors use the native Windows utility makecab to compress the data prior to its exfiltration over HTTP POST requests.
Finally, in the fifth and final stage of the attack, the adversary details on the system’s current security configuration settings. They are focused on discovering if Microsoft Defender and if it is actively protecting the infected host.
System Service Discovery (T1007): Microsoft’s native sc utility is executed to query a list of all running services and filters for the Microsoft Defender service.
Security Software Discovery (T1518.001): A PowerShell script is executed to determine if Microsoft Defender is actively protecting the system by calling the Get-MpComputerStatus cmdlet.
Detection and Mitigation Opportunities
With so many different techniques being used by threat actors, it can be difficult to know which to prioritize for prevention and detection assessment. AttackIQ recommends first focusing on the following techniques:
1. Scheduled Task/Job: Scheduled Task (T1053.005)
Adversaries may abuse the Windows Task Scheduler to perform task scheduling for initial or recurring execution of malicious code. There are multiple ways to access the Task Scheduler in Windows. The schtasks utility can be run directly from the command line, or the Task Scheduler can be opened through the GUI within the Administrator Tools section of the Control Panel.
1a. Detection
With an EDR or SIEM Platform, you can detect the following commands being issued to schedule a malicious task:
Process Name = (“cmd.exe” OR “Powershell.exe”)
Command Line CONTAINS (“schtasks” AND “/CREATE” AND (“cmd” OR “powershell”)
1b. Mitigation
MITRE ATT&CK has the following mitigation recommendations:
- M1047 – Audit
- M1028 – Operating System Configuration
- M1026 – Privileged Account Management
- M1018 – User Account Management
2. Command and Scripting Interpreter: PowerShell (T1059.001)
This actor heavily utilizes PowerShell scripts and built-in PowerShell cmdlets to complete their discovery objectives and interact with Active Directory.
2a. Detection
Enabling PowerShell script logging is critical to being able to track how PowerShell is being used in your environment. Many actors will obfuscate their code to make it more difficult to detect.
Resources for Enabling PowerShell Logging:
- https://logrhythm.com/blog/powershell-command-line-logging/
- https://www.mandiant.com/resources/blog/greater-visibility
- https://www.splunk.com/en_us/blog/security/hunting-for-malicious-powershell-using-script-block-logging.html
2b. Mitigation
MITRE ATT&CK has the following mitigation recommendations:
- M1049 – Antivirus/Antimalware
- M1045 – Code Signing
- M1042 – Disable or Remove Feature or Program
- M1038 – Execution Prevention
- M1026 – Privileged Account Management
Wrap-up
In summary, this attack graph will evaluate security and incident response processes and support the improvement of your security control posture against another a determined Iranian threat actor. With data generated from continuous testing and use of these attack graphs, you can focus your teams on achieving key security outcomes, adjust your security controls, and work to elevate your total security program effectiveness against a known and dangerous threat.
AttackIQ stands at the ready to help security teams implement this attack graph and other aspects of the AttackIQ Security Optimization Platform, including through our co-managed security service, AttackIQ Vanguard.
Test Yourself on OilRig
See how your defenses stack up (for free) by downloading and trialing Flex.
Try it out for yourself.
 (Click for Larger)
(Click for Larger)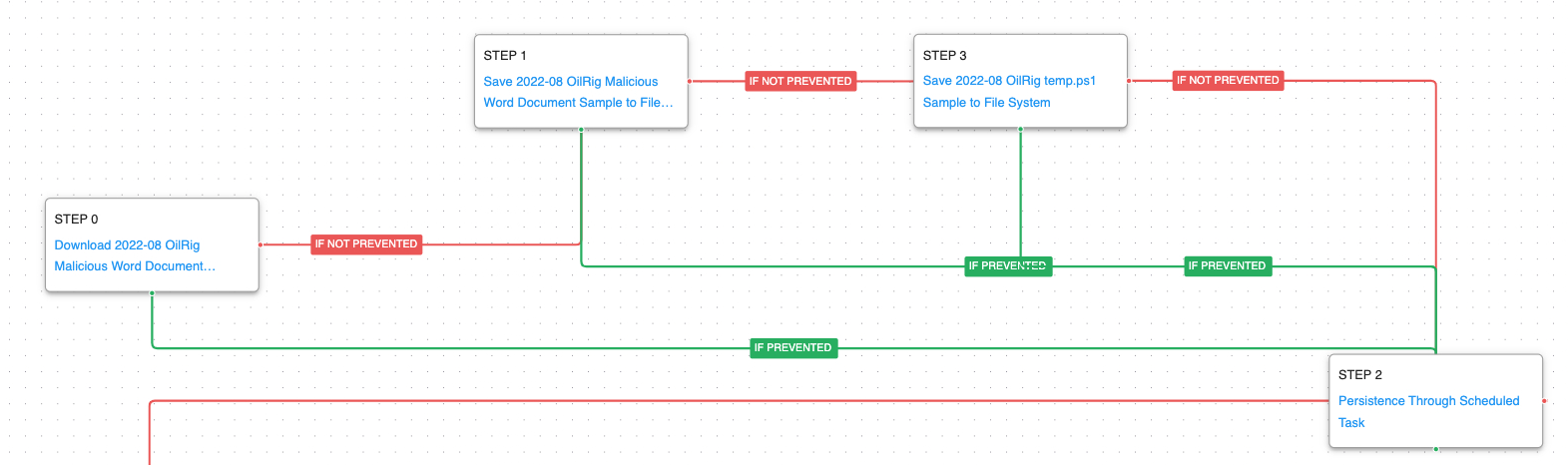 (Click for Larger)
(Click for Larger) (Click for Larger)
(Click for Larger)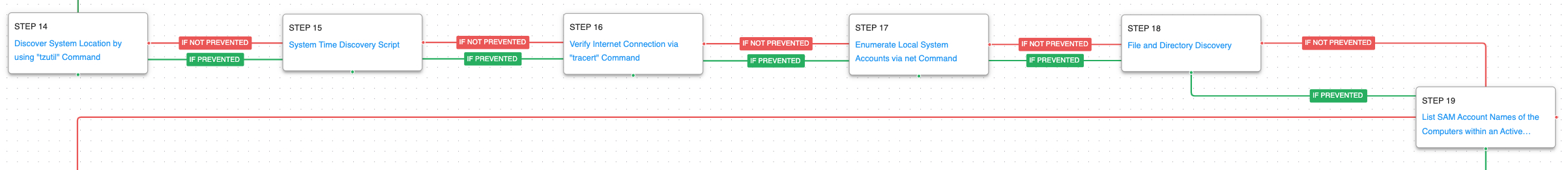 (Click for Larger)
(Click for Larger) (Click for Larger)
(Click for Larger) (Click for Larger)
(Click for Larger)

