On Friday May 27, 2022, an independent cybersecurity research team known as Nao_Sec discovered a malicious Microsoft Office document shared on VirusTotal. Uploaded from an IP address in Belarus, the document contained what turned out to be a 0-day, zero-click remote code execution (RCE) vulnerability in the Microsoft Support Diagnostic Tool (MSDT) in Windows. The vulnerability, nicknamed “Follina,” has been assigned CVE-2022-30190 and Microsoft has reported active exploitation in the wild. The U.S. Cybersecurity and Infrastructure Security Agency (CISA) is urging users and administrators to review Microsoft’s Guidance for CVE-2022-30190 Microsoft Support Diagnostic Tool Vulnerability and apply the necessary workaround.
To exploit the vulnerability, an attacker can abuse the MS Word remote template feature as a calling application to retrieve a malicious HTML file that uses the ms-msdt URL protocol to execute arbitrary code such as PowerShell within the context of Word and at the privilege level at which the calling application is running, allowing an attacker to install programs, view, change, or delete data, or create new accounts. This works even if macros are disabled, however, Application Guard for Office as well as Protected View may prevent the attack.
The Content Team at AttackIQ has created a new scenario replicating exploitation of this vulnerability to help security teams validate visibility, patching, security controls and logging in their environments relative to this pervasive 0-day vulnerability exploited in the wild. The scenario drops and executes a Microsoft Office document that retrieves a remote HTML file that contains a crafted ms-msdt URL that will execute an obfuscated PowerShell command.
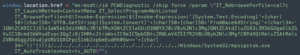
When decoded, that command will first stop the running Microsoft Troubleshooting msdt.exe process and then drop a canary file on the host indicating that the vulnerability has successfully been exploited.
$cmd = “c:\windows\system32\cmd.exe”;
Start-Process $cmd -windowstyle hidden -ArgumentList “/c taskkill /f /im msdt.exe”;
Get-Process | Out-File -FilePath $env:TEMP\<verification file>.txt;
This scenario is available in the AttackIQ Security Optimization Platform now. AttackIQ stands at the ready to help security teams implement this assessment and other aspects of the AttackIQ Security Optimization Platform, including through our co-managed security service, AttackIQ Vanguard.