The Rise of Exploit-Based Attacks
Recent studies highlight that vulnerabilities, not just phishing, have become a primary attack vector. Mandiant reports that exploit-based attacks have overtaken email-based methods, and CrowdStrike notes that 75% of threats now leverage “living off the land” (LotL) tools rather than traditional malware[1][2]. These methods exploit vulnerabilities in existing systems and applications, often taking advantage of overlooked entry points. The growing prevalence of zero-days and AI-powered exploit discovery further complicates the challenge for defenders.
The Critical Role of Detection
Effective detection is essential, especially with the increasing number of malware-less attacks. According to Accenture, less than 1% of an organization’s detection rules are fully effective. Many detection rules remain outdated, resulting in a flood of false positives and missed detection opportunities.
Detection must focus on adversary behaviors, not static indicators like malware hashes. The shelf life for these ephemeral indicators is short. Behavior-based detection tied to adversary tactics, techniques, and procedures (TTPs) gives organizations a chance to detect and mitigate threats in real time, meeting compliance requirements from regulations like GDPR, PCI, HIPAA, and FISMA.
Why Improving Detection is Challenging
Detection engineering is the discipline of transforming adversary knowledge into actionable detection rules. This is a continuous cycle: researching relevant threats, building specific detection logic, and validating those detections to ensure effectiveness. But many organizations struggle here. Writing, testing, and maintaining hundreds of detection rules can overwhelm even the most mature security teams. Tests can be written poorly, and when they aren’t validated accurately, they lead to gaps in coverage or false positives that bury real alerts.
Four Questions to Streamline Detection Efforts
For organizations aiming to bolster detection, there are four fundamental questions to address:
- Is Your Detection Pipeline Effective? Visibility into your detection alert pipeline is essential to confirm your controls are communicating with your SIEM
- Can Your Controls Catch Threats Beyond Prevention? Relying solely on prevention leaves a gap. Detection provides a safety net to identify threats that bypass preventative measures.
- How Quickly Can You Gain Insights? In fast-moving scenarios like incident response, it’s crucial to have immediate visibility into your detection capabilities.
- How Can You Address Detected Gaps? Once gaps are identified, the next step is developing rules to close those gaps.
Flex 3.0: Agentless Detection Validation with Splunk Integration
With Flex 3.0’s integration into Splunk, organizations can now continuously identify detection gaps across all devices without the need for agents. This integration provides instant insights into the detection pipeline, surfacing visibility gaps in minutes and enabling deployment of Sigma rules to address gaps as soon as they’re found. With a dedicated Flex app for Splunk, customers can access detection insights through a centralized dashboard.
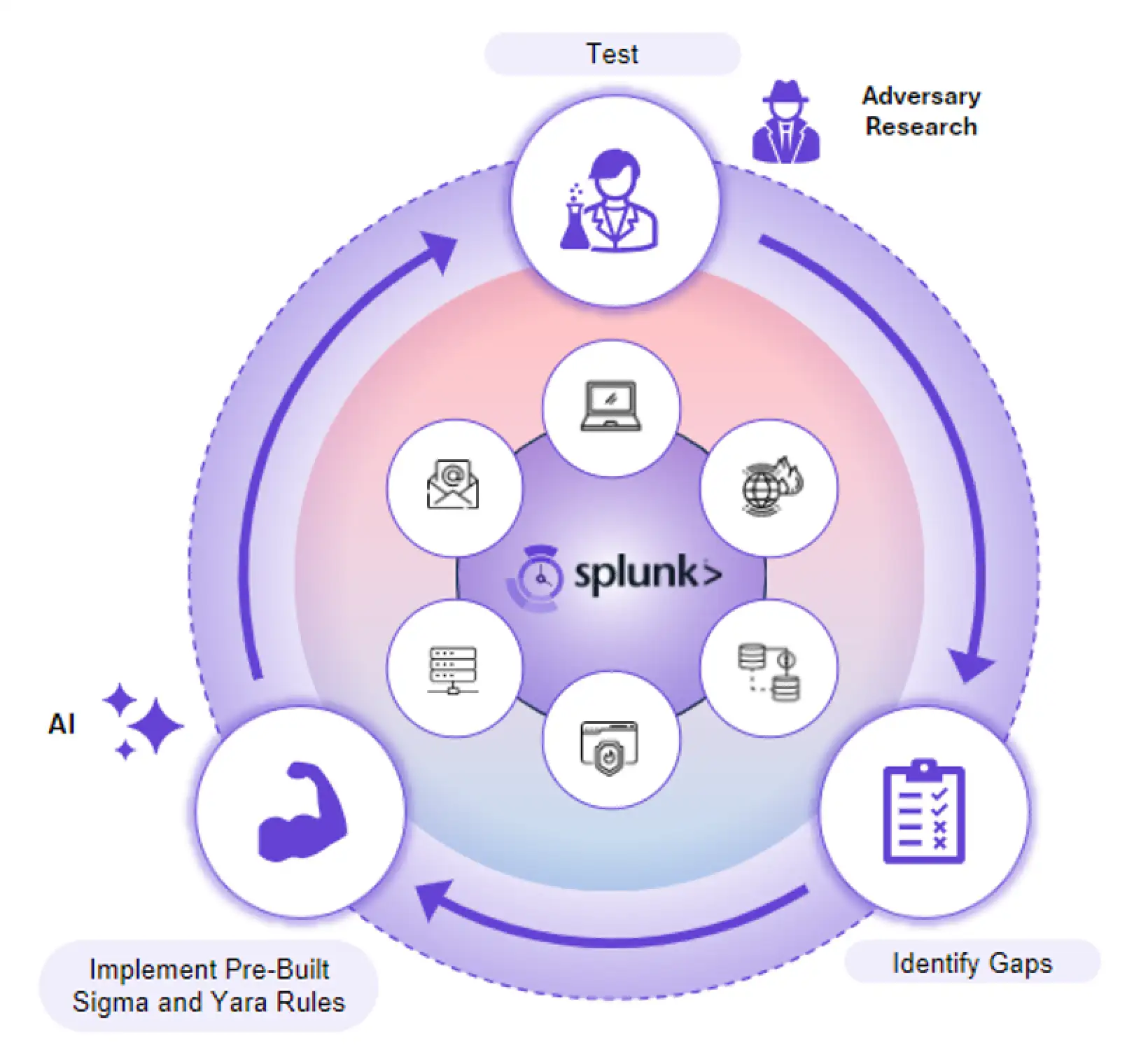
The Value to Customers
With the enhanced detection capabilities in Flex 3.0, customers can expect significant benefits. IDC research indicates that organizations using AttackIQ achieve a 44% cost reduction in security breaches, 47% improvement in security operations efficiency, and a 37% increase in SOC analyst efficiency. These efficiencies translate into an average savings of over $1 million per customer annually, in addition to strengthened security.
Ready to Learn More?
Flex detection is available for everyone for users with Splunk deployments. Try it for free today.
[1] How Low Can You Go? An Analysis of 2023 Time-to-Exploit Trends | Google Cloud Blog
[2] 2024 Global Threat Report Trends and Overview | CrowdStrike