On December 13, 2023, the U.S. Federal Bureau of Investigation (FBI), U.S. Cybersecurity & Infrastructure Security Agency (CISA), U.S. National Security Agency (NSA), Polish Military Counterintelligence Service (SKW), CERT Polska (CERT.PL), and the UK’s National Cyber Security Centre (NCSC) released a Cybersecurity Advisory (CSA) assessing that Russian Foreign Intelligence Service (SVR) cyber actors, also known as APT 29, the Dukes, CozyBear, and NOBELIUM/Midnight Blizzard, were observed exploiting CVE-2023-42793 at a large scale, targeting servers hosting JetBrains TeamCity software since September 2023.
Nobelium is a politically motivated state-sponsored adversary suspected of operating on behalf of the Russian Foreign Intelligence Service (SVR). This adversary, which has been active since at least 2019, has targeted government organizations, non-governmental organizations (NGOs), think tanks, and technology service providers, primarily in the United States and Europe.
Nobelium is often identified as a new iteration of the historical adversary APT29, active since at least 2013, as it shares many similarities in terms of Tactics, Techniques and Procedures (TTP). Microsoft identified Nobelium as a new name for this continuation of APT29 in March 2021, but publicly available reports from multiple security vendors continue to use Nobelium and APT29 as interchangeable aliases.
AttackIQ has previously released an attack graph emulating the activities conducted by Nobelium against European Union (EU) governments. Such activities continued Russia’s efforts to gather intelligence on countries supporting Ukraine in the Russia-Ukraine war. For further coverage and details, we suggest the reader visit the blog published on May 4, 2023.
Software developers use TeamCity software to manage and automate software compilation, building, testing, and releasing. If compromised, access to a TeamCity server would provide malicious actors with access to that software developer’s source code, signing certificates, and the ability to subvert software compilation and deployment processes. Access to a TeamCity server by a malicious actor could additionally be used to conduct supply chain operations.
The SVR has been observed using the initial access gleaned by exploiting the TeamCity CVE to escalate its privileges, move laterally, deploy additional backdoors, and take other steps to ensure persistent and long-term access to the compromised network environments.
To bring Russia’s actions to public attention, the authoring agencies are providing information on the SVR’s most recent compromise to aid organizations in conducting their own investigations and securing their networks, provide compromised entities with actionable indicators of compromise (IOCs), and empower private sector cybersecurity companies to better detect and counter the SVR’s malicious actions.
AttackIQ has released a new attack graph that emulates the behaviors exhibited by Russian Foreign Intelligence Service (SVR) cyber actors during a wave of activities in which they abused the JetBrains TeamCity vulnerability (CVE-2023-42793), with the aim of helping customers validate their security controls and their ability to defend against this recent threat.
Validating your security program performance against these behaviors is vital in reducing risk. By using this new assessment template in the AttackIQ Security Optimization Platform, security teams will be able to:
- Evaluate security control performance against the post-compromise activities related to the exploitation of the vulnerability CVE-2023-42793.
- Assess their security posture against highly prolific and opportunistic adversaries that have been observed exploiting this vulnerability globally.
- Continuously validate detection and prevention pipelines against adversaries associated with the Russian Foreign Intelligence Service (SVR)
[CISA AA23-347A] Russian Foreign Intelligence Service (SVR) Exploiting JetBrains TeamCity CVE Globally
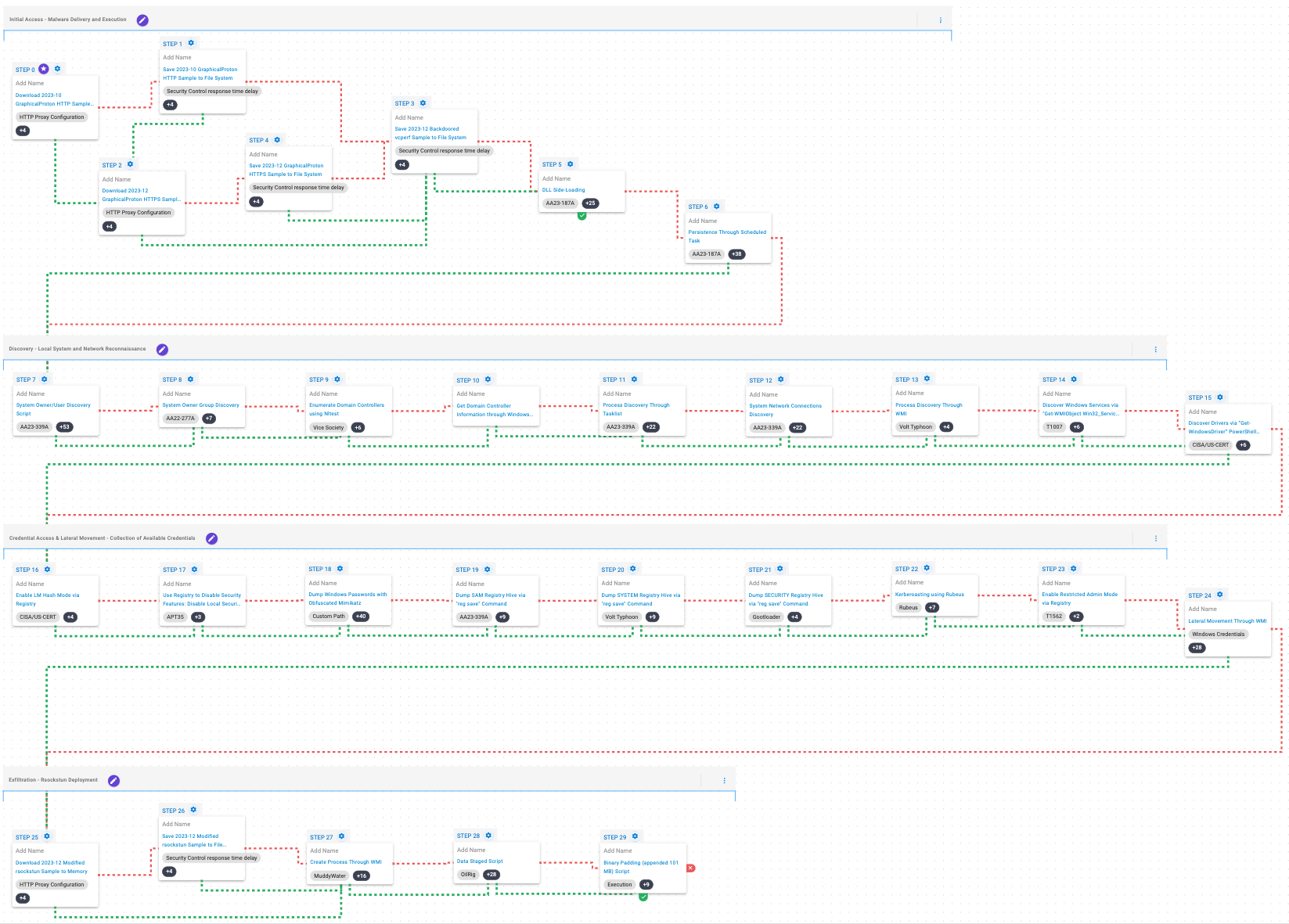
This attack graph emulates the various Tactics, Techniques and Procedures (TTPs) associated with the exploitation of the JetBrains TeamCity CVE-2023-42793 vulnerability by adversaries linked to the Russian Foreign Intelligence Service (SVR).
This emulation begins by downloading and saving GraphicalProton, a simplistic backdoor that uses OneDrive, Dropbox, and randomly generated BMPs to exchange data with its operator. After this, a modified legitimate application will be saved to the system, which is then abused to execute the backdoor via DLL Side-Loading. Once the execution is successful, the attacker will seek to achieve persistence by creating a scheduled task.
Ingress Tool Transfer (T1105): This scenario downloads to memory and saves to disk in independent scenarios to test network and endpoint controls and their ability to prevent the delivery of known malicious samples.
Hijack Execution Flow: DLL Side-Loading (T1574.002): Bundles a DLL with a Windows executable that is susceptible to DLL Side-Loading to execute actor code.
Scheduled Task/Job: Scheduled Task (T1053.005): This scenario creates a new scheduled task named WindowsDefenderService using the schtasks utility.
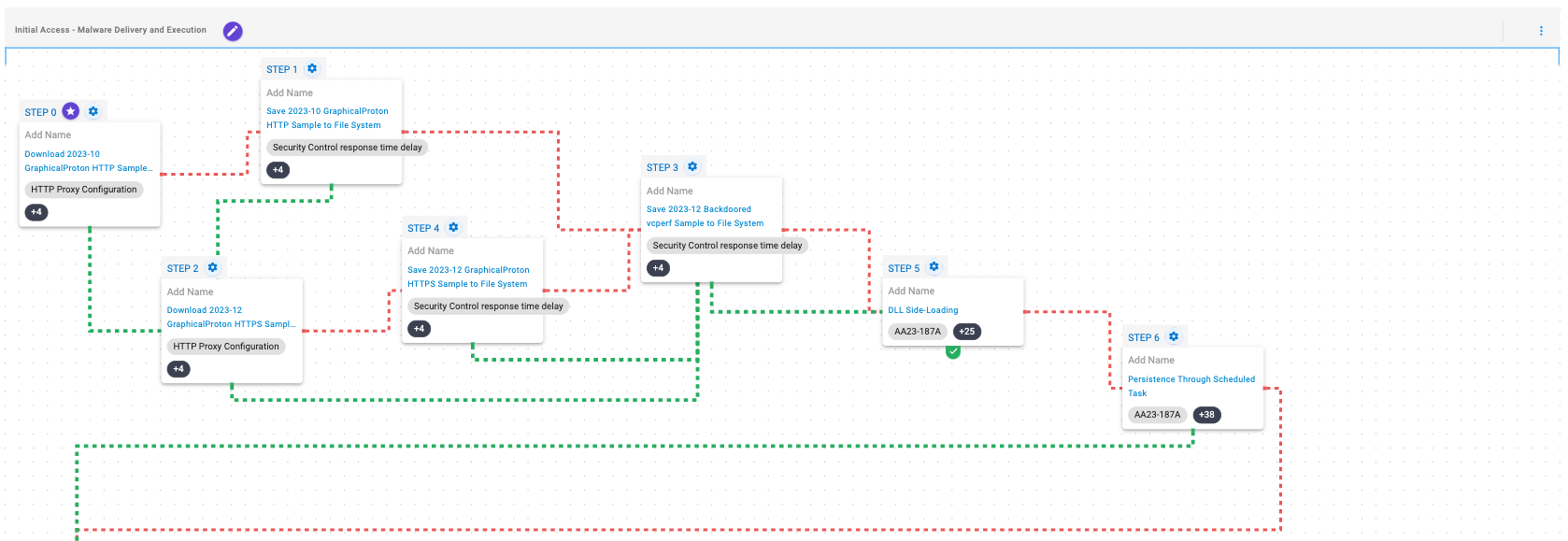
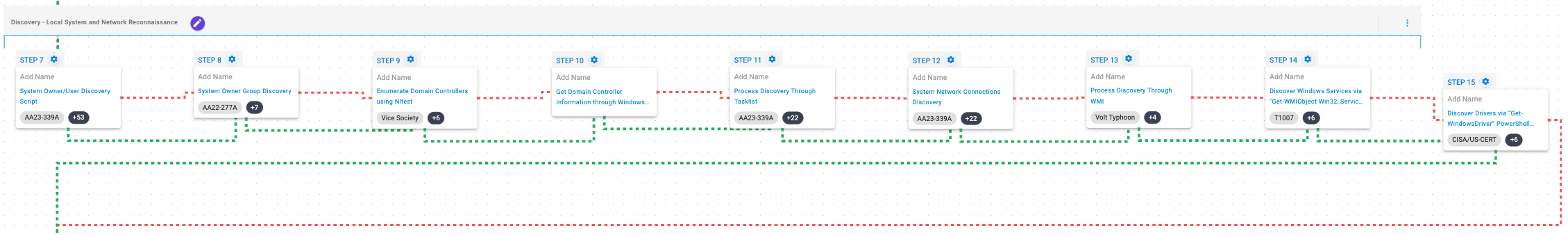
This stage is focused on the discovery of information related to the local environment and the network of which the compromised system is part. During these activities, the adversary obtains information about the compromised system, its users, active processes and services, available drivers, available network connections and information concerning the associated domain controller.
System Owner / User Discovery (T1033): Live off the land by running whoami and users to gain details about the currently available accounts and permission groups.
Remote System Discovery (T1018): This scenario executes the nltest command to gather a list of domain controllers associated with a domain.
Process Discovery (T1057): Window’s built-in tasklist command is executed as a command process and the results are saved to a file in a temporary location.
System Network Configuration Discovery (T1016): Native Window’s commands like route, ipconfig, and net use are executed to collect details about the infected host and network shares.
System Service Discovery (T1007): This scenario executes the Get-WmiObject -Class Win32_Service WMI command to query a list of all running services.
System Information Discovery (T1082): The PowerShell command Get-WindowsDriver is executed to retrieve a list of the active Windows drivers.
During this stage, the adversary performs techniques associated with gathering credentials available on the compromised system that will later be used to move laterally to additional targets.
The adversary will then enable LM hash mode to ensure that LM hashes are stored in memory and afterwards, it will disable Local Security Authority (LSA) to allow untrusted processes to access protected system resources.
Once these modifications are accomplished, the adversary will try to perform a dump of the SAM, SYSTEM and SECURITY registry hives, perform kerberoasting and eventually enable Restricted Admin Mode. Finally, using these credentials, the attacker will attempt to move laterally to available systems via WMI.
Modify Registry (T1112): The HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Lsa\NoLmHash registry value is modified to ensure that the host will keep LM hashes in memory.
Modify Registry (T1112): The HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Lsa\RunAsPPL registry value is modified to disable Local Security Authority (LSA) protection.
OS Credential Dumping (T1003): This scenario leverages an obfuscated version of Mimikatz to dump credentials on Windows hosts.
OS Credential Dumping: Security Account Manager (T1003.002): The built-in reg save command is executed to dump the Windows SAM, SYSTEM, and SECURITY hive.
Steal or Forge Kerberos Tickets: Kerberoasting (T1558.003): Kerberoasting allows an attacker to attempt to extract password hashes for accounts using their Service Principal Name (SPN) ticket. This scenario attempts to perform Kerberoasting using Rubeus.
Modify Registry (T1112): The HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Lsa\DisableRestrictedAdminMode registry value is modified to ensure that RDP credentials are stored in memory.
At this stage, the attacker will seek to carry out deployment by a modified version of the tunneler called Rsockstun, that is used to establish a tunnel to the C2 infrastructure, which will be executed via WMI.
Finally, the adversary will bundle all the collected data into a file, to which useless data will be added via binary padding prior to exfiltration.
Windows Management Instrumentation (WMI) (T1047): This scenario creates a new process using the Windows Management Instrumentation (WMI) Console.
Data Staged: Local Data Staging (T1074.001): Files are collected and stored in a temporary directory so they can be exfiltrated later.
Obfuscated Files or Information: Binary Padding (T1027.001): This scenario will execute a version of Mimikatz which includes trailing padding increase its size to avoid detection by security controls that will choose not to scan large files.
Detection and Mitigation Opportunities
Given the number of different techniques being utilized by this threat, it can be difficult to know which to prioritize for prevention and detection opportunities. AttackIQ recommends first focusing on the following techniques emulated in our scenarios before moving on to the remaining techniques.
1. Review CISA’s Patching and Detection Recommendations:
CISA has provided a significant number of recommendations for the best ways to defend yourself from these and similar attacks. AttackIQ strongly recommends reviewing the detection and mitigation recommendations to adapt them to your environment first to determine if you have any existing impact before reviewing the assessment results.
2. Hijack Execution Flow: DLL Side-Loading (T1574.002):
Malware will commonly use side-loading to load malicious code into legitimate running processes to attempt to blend in with legitimate applications to remain hidden and appear normal to the compromised system.
2a. Detection
Searching for common processes that are performing uncommon actions can help identify when a process has been compromised. Searching for newly constructed processes or monitoring for DLL/PE file events, specifically for the creation and loading of DLLs into running processes can help identify when a system process has been compromised.
2b. Mitigation
MITRE ATT&CK recommends the following mitigation recommendations:
3. Scheduled Task/Job: Scheduled Task (T1053.005)
Adversaries may abuse the Windows Task Scheduler to perform task scheduling for initial or recurring execution of malicious code. There are multiple ways to access the Task Scheduler in Windows. The schtasks utility can be run directly from the command line, or the Task Scheduler can be opened through the GUI within the Administrator Tools section of the Control Panel.
3a. Detection
With an EDR or SIEM Platform, you can detect the following commands being issued to schedule a malicious task
Process Name = (“cmd.exe” OR “Powershell.exe”)
Command Line CONTAINS (“schtasks” AND “/CREATE” AND (“cmd” OR “powershell”)
3b. Mitigation
MITRE ATT&CK has the following mitigation recommendations for Scheduled Task
- M1047 – Audit
- M1028 – Operating System Configuration
- M1026 – Privileged Account Management
- M1018 – User Account Management
Wrap-up
In summary, this attack graph will evaluate security and incident response processes and support the improvement of your security control posture against the recent activities carried out by Russian Foreign Intelligence Service (SVR) cyber actors. With data generated from continuous testing and use of this assessment template, you can focus your teams on achieving key security outcomes, adjust your security controls, and work to elevate your total security program effectiveness against a known and dangerous threat.
AttackIQ offers a comprehensive Breach and Attack Simulation Platform to assist security teams. This includes AttackIQ Flex, a tailored pay-as-you-go service; AttackIQ Ready!, a fully managed service for continuous security optimization; and AttackIQ Enterprise, a co-managed service offering enhanced support. These services ensure your team maintains a robust security posture.
 Click for Larger
Click for Larger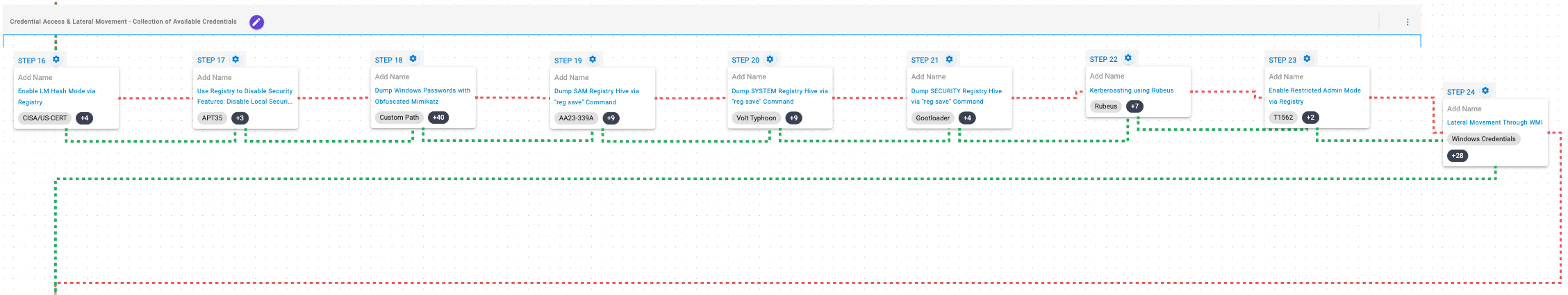 Click for Larger
Click for Larger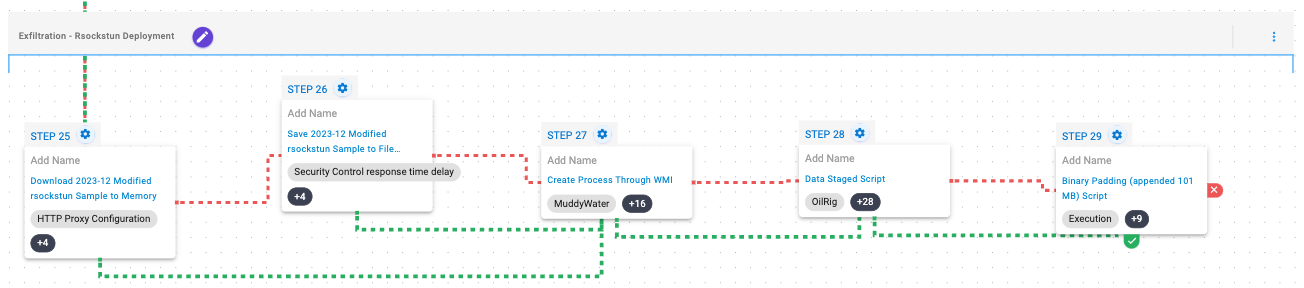 Click for Larger
Click for Larger