This is a writeup for CVE-2021-26556, a local privilege escalation in Octopus Server.
The following versions are affected by this vulnerability:
- All 0.x.x, 1.x.x, 2.x.x, 3.x.x, 4.x.x versions
- All 2018.x.x, 2019.x.x, 2020.1.x, 2020.2.x, 2020.3.x versions
- All 2020.4.x versions before 2020.4.229
- All 2020.5.x versions before 2020.5.256
OctopusDeploy Local Privilege Escalation
In order to investigate field reports of potential permissions issues with the service, we signed up for the free license key here: https://octopus.com/start/server. From there, we were emailed instructions and a license key. Following the installation directions, we install the self-hosted server.
We used the default settings at every step, except for the installation directory which we changed to C:\tools to demonstrate the permission misconfiguration. This directory can either be created through the installer GUI, or through the command line – for example: mkdir C:\tools.
After completing the installation, we found the service was registered as expected.
Note the improper permissions, BUILTIN\Users Allow *, on the installation directory, which are inherited from the drive root:
To fully demonstrate the implications of this vulnerability, we created a new unprivileged user. Then, as this new user, we downloaded the provided CRYPTBASE.dll. Note how the user has permissions to add the poisoned dll to the installation directory. This DLL has a payload which will execute once the file is loaded.
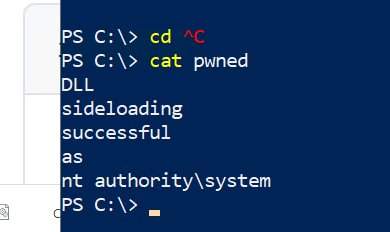
From here, we simply restarted the OctopusDeploy service as an administrator user (restarting the computer would have the same effect). This causes the payload to execute, which creates a file at C:\pwned, containing evidence of what access rights were gained:
The Fix
As described in the vendor advisory, the recommended solution is to download the latest version of Octopus Server from https://octopus.com/downloads.
Vendor Notification
| December 31st, 2020 | Reported to [email protected] |
| January 3rd, 2021 | Octopus Deploy team response |
| January 7th, 2021 | Vulnerability triaged by Octopus Deploy team |
| February 20th | Continued correspondence with Octopus Deploy team |
| March 7th | Patch and CVE-2021-26556 released, along with a patch for CVE-2021-26557 which is a similar issue in the Octopus Tentacle service. |
| April 13th, 2021 | DeepSurface Advisory published |
Acknowledgements
We would like to thank the Octopus security team for their excellent response and thoroughness in investigating this issue.