Access Denied:
A Behavioral Analysis of Modern Ransomware Operations
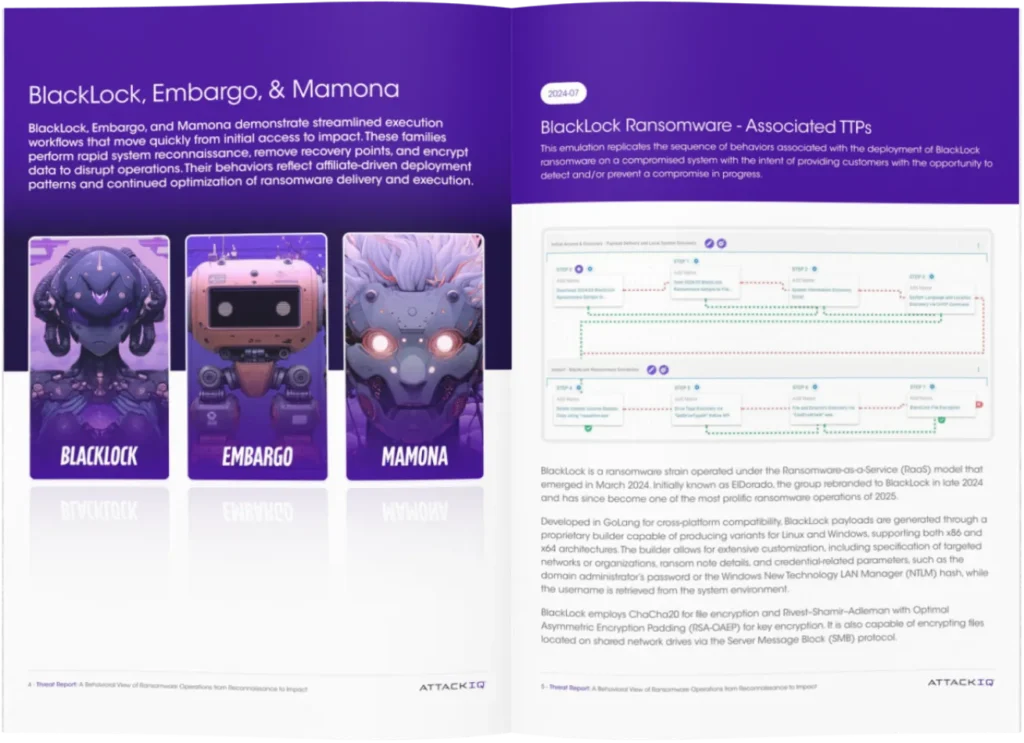
Ransomware continues to evolve at the surface, but its underlying playbook rarely changes. Behind every new strain is the same structured progression: gain access, analyze the environment, neutralize recovery, and escalate toward impact.
This report dissects those behaviors across both legacy and active ransomware families, revealing the repeatable patterns defenders can reliably detect and interrupt.
By focusing on how ransomware operators truly operate during intrusions, security teams can more effectively identify early activity, verify defensive performance, and strengthen their response strategy against real ransomware attacks.
What You’ll Learn:
Learn how ransomware really works—and how to detect, disrupt, and stop attacks before they escalate.
Download the Report
By submitting this form, you indicate that you have read and agree to the terms of our Privacy Policy.
