AttackIQ Flex
Agentless, On-Demand Exposure Validation.
Run production-safe adversary emulations in minutes. No agents, no installs, no commitment.
Try it FreeFinally, Exposure Validation That Works. On Your Terms.
Transform ad hoc testing into continuous validation that uncovers vulnerabilities other tools miss.
Self-contained test packages you can run on any device
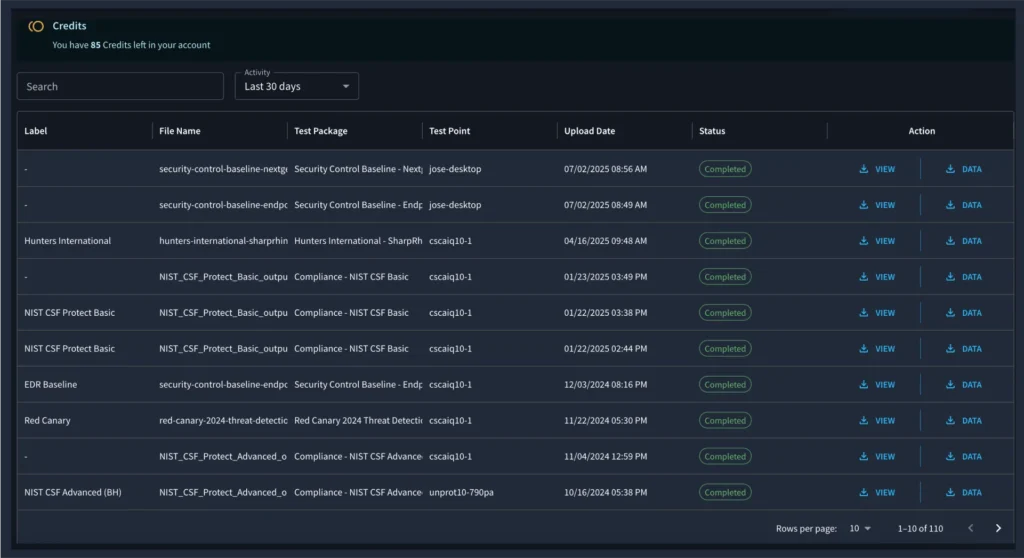
Pay-as-you-go pricing with free credits to start
Prebuilt emulations aligned to real-world adversaries
Remediation guidance built in for faster fixes
Simple Exposure Validation—Anytime, Anywhere
Lightweight deployment gets you testing real-world attack scenarios immediately.
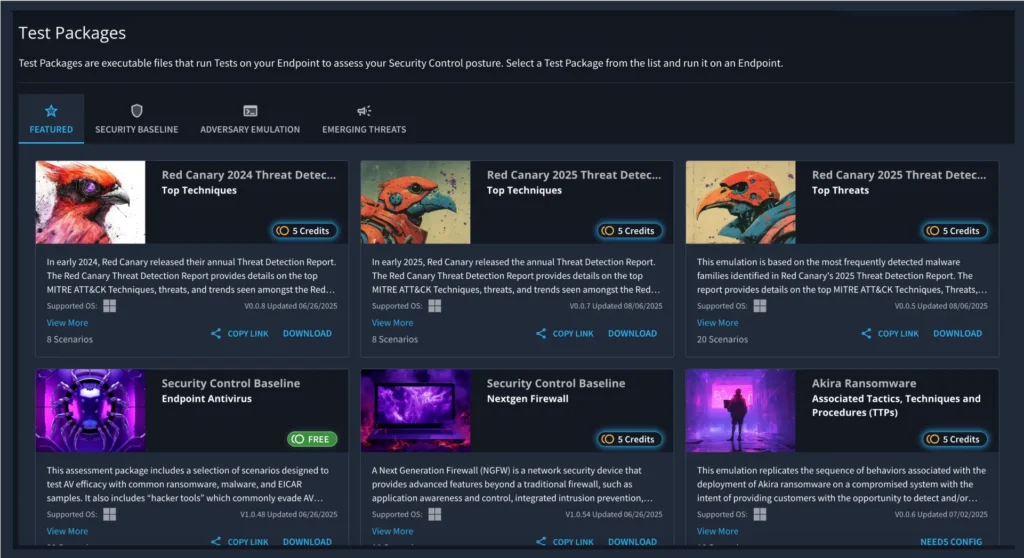
Choose
Your Tests
Select from full adversary campaigns and security control baselines to validate your defenses.
Run Anywhere,
Instantly
No agents. No installs. Execute production-safe tests on any device in your environment—Flex is fully self-contained.
Analyze and
Remediate
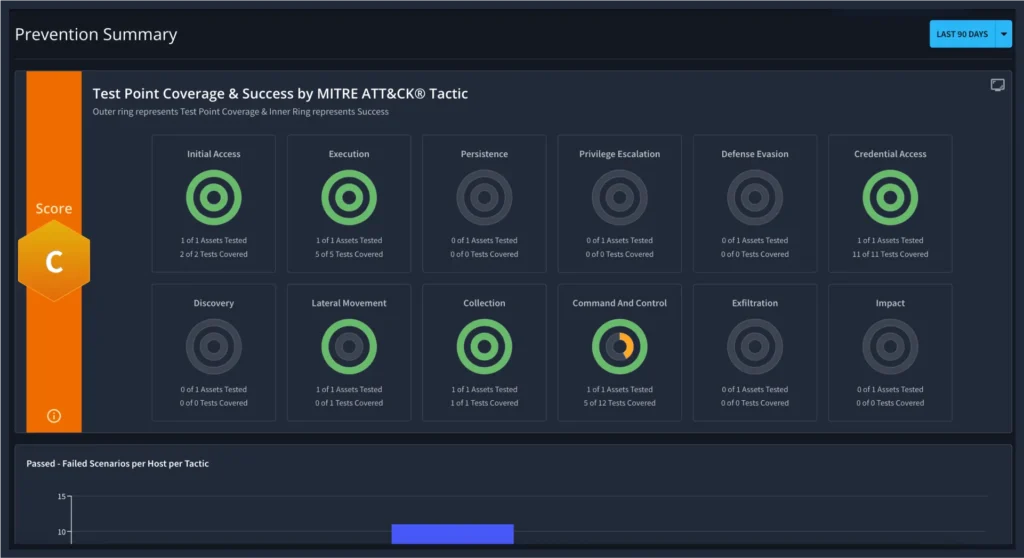
View detailed results mapped to MITRE ATT&CK. Use built-in detection rules and mitigation guidance to close validated exposure gaps fast.
Adversary-Informed Testing Built for Speed
Validate your defenses against current threat intelligence without delays or lengthy procurement cycles.
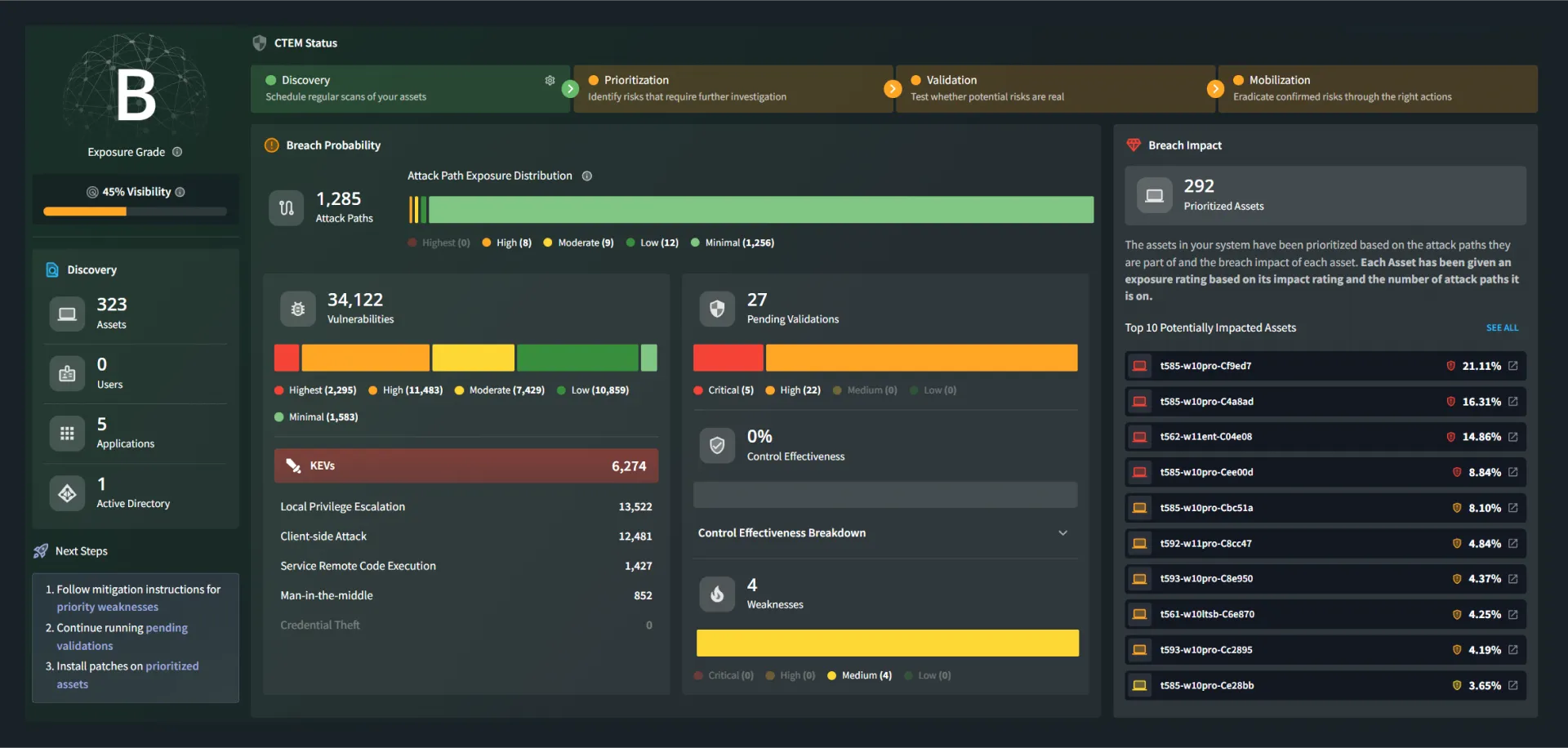
Validate Exposure Using Real Attack Paths
Understand Your Risk in Minutes
Fix Validated Exposures
Verify Detection Coverage
Pay-as-You-Test Pricing That Scales With You
Start free, then scale based on actual usage. You maintain full control over testing frequency and scope—no overhead, no surprises.
FAQs
Never Settle for Uncertainty
Validate Your Defenses
Take the guesswork out of threat exposure management. Validate your defenses with real-world attack scenarios and focus on what matters most—managing your risk.