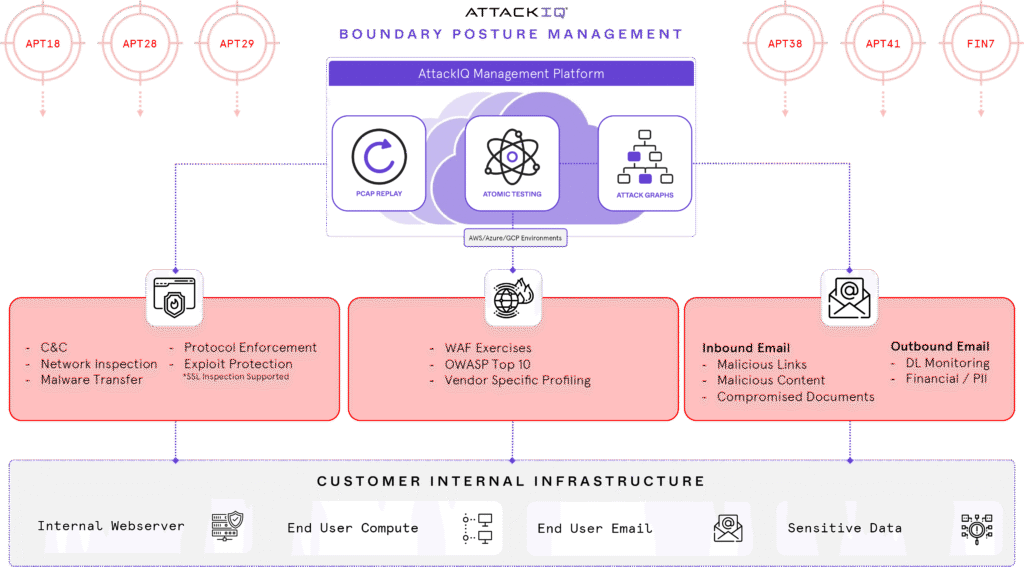
Boundary Posture Management
AttackIQ’s Boundary Posture Management (BPM) module addresses the challenges of security control failure by continuously evaluating your boundary security, generating analytic data about your performance and identifying gaps between your assumed effectiveness and your actual posture. How does it work? BPM uses a combination of atomic tests, packet capture (PCAP) replays, inbound email attacks, and outbound data exfiltration to emulate a range of adversary behaviors, to include command and control, protocol enforcement, and DLP monitoring, among other defensive capabilities.
BPM runs multiple adversary emulations against your boundary security controls at scale and in production, generating real-time performance data about known threats. With BPM, AttackIQ provides the most comprehensive adversary emulation capabilities available on the market, emulating attackers with specificity and realism at the beginning, middle, and end of the kill-chain to give customers a portrait of their overall security posture effectiveness.
Benefits