AttackIQ Ready
Turnkey Exposure Validation. Built and run by Experts.
Emulate real adversaries, validate control performance, and prioritize what truly puts you at risk—without the burden of managing it yourself.
Schedule a Demo
Adversarial Exposure Validation. Delivered as a Service.
No build. No maintenance. Just continuous, expert-led validation that strengthens your defenses.
Run Real-World Adversary TTPs
Execute emulations based on MITRE ATT&CK—no scripting, tuning, or setup required.
Expose Detection Blind Spots
Surface silent failures and security gaps across EDR, SIEM, firewalls, and perimeter controls.
Identify Exploitable Attack Paths
Map how adversaries can move through your environment to reach critical systems and data.
Prioritize High-Risk Exposures
Leverage hyperlocal threat intelligence and AI to focus on actively exploited exposures.
Remediate Validated Security Gaps
Apply targeted fixes with automated retesting to confirm control effectiveness.
Prove Security Improvements
Track control performance, remediation velocity, and risk reduction over time.
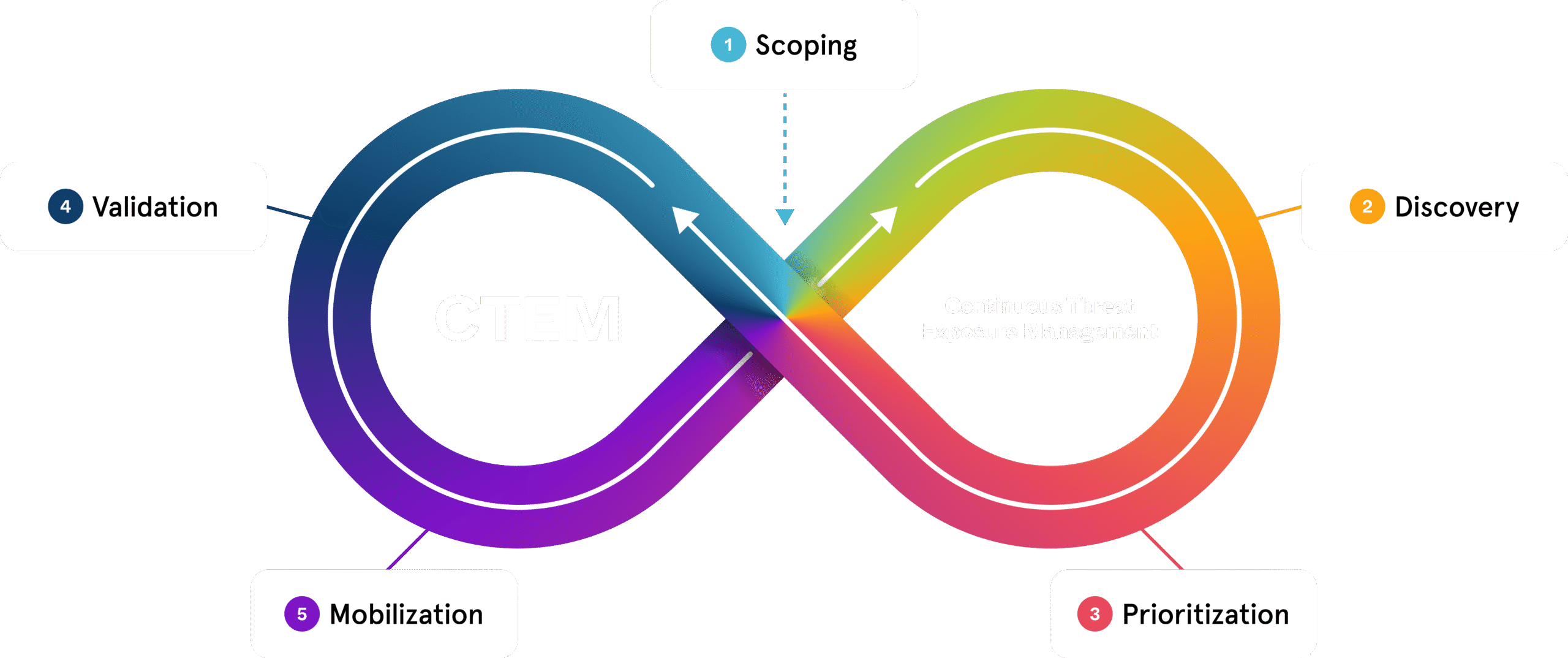
Engineered to Execute CTEM, End to End
Ready supports the execution of the CTEM framework from discovery to remediation. You define scope and objectives; we accelerate everything else.
Prove Control Effectiveness—from the SOC to the C-Suite
Showcase measurable risk reduction with expert-led testing, automated validation, and executive-ready reporting.
Track Security Performance Over Time
Monitor validation results, control gaps, and improvements across your environment.
Translate Risks for Executives and Boards
Deliver concise reports that map technical findings to business and mission impact.
Quantify ROI and Program Value
Measure outcomes like coverage, remediation speed, and reduced exposure.
Demonstrate Compliance Confidence
Generate audit-ready reports aligned to NIST, DORA, and cyber insurance standards.
Ready FAQs
Never Settle for Uncertainty
Validate Your Defenses
Take the guesswork out of threat exposure management. Validate your defenses with real-world attack scenarios and focus on what matters most—managing your risk.