Introduction
The Alert Entropy Problem
It’s a scene all too familiar in Security Operations Centers worldwide: the alert queue showing thousands of notifications, analysts struggling to determine which threats deserve immediate attention, and no one quite remembering why certain detection rules were created in the first place.
This isn’t just anecdotal frustration. According to recent research, SOC analysts face up to 10,000 alerts per day, and their accuracy can drop by 40% after just 12 hours of work due to alert fatigue when bombarded by this constant stream of notifications. A 2023 Devo survey found that 83% of analysts feel overwhelmed by alert noise and context gaps which severely impacts the effectiveness of security teams, leading to potential vulnerabilities and breaches.
The problem is entropy – that fundamental law of physics that describes how systems naturally move toward disorder. In detection engineering, entropy manifests as rules that age poorly, logs that change format, security controls that evolve, and threats that constantly transform. Meanwhile, the institutional knowledge about these rules fades as team members move on.
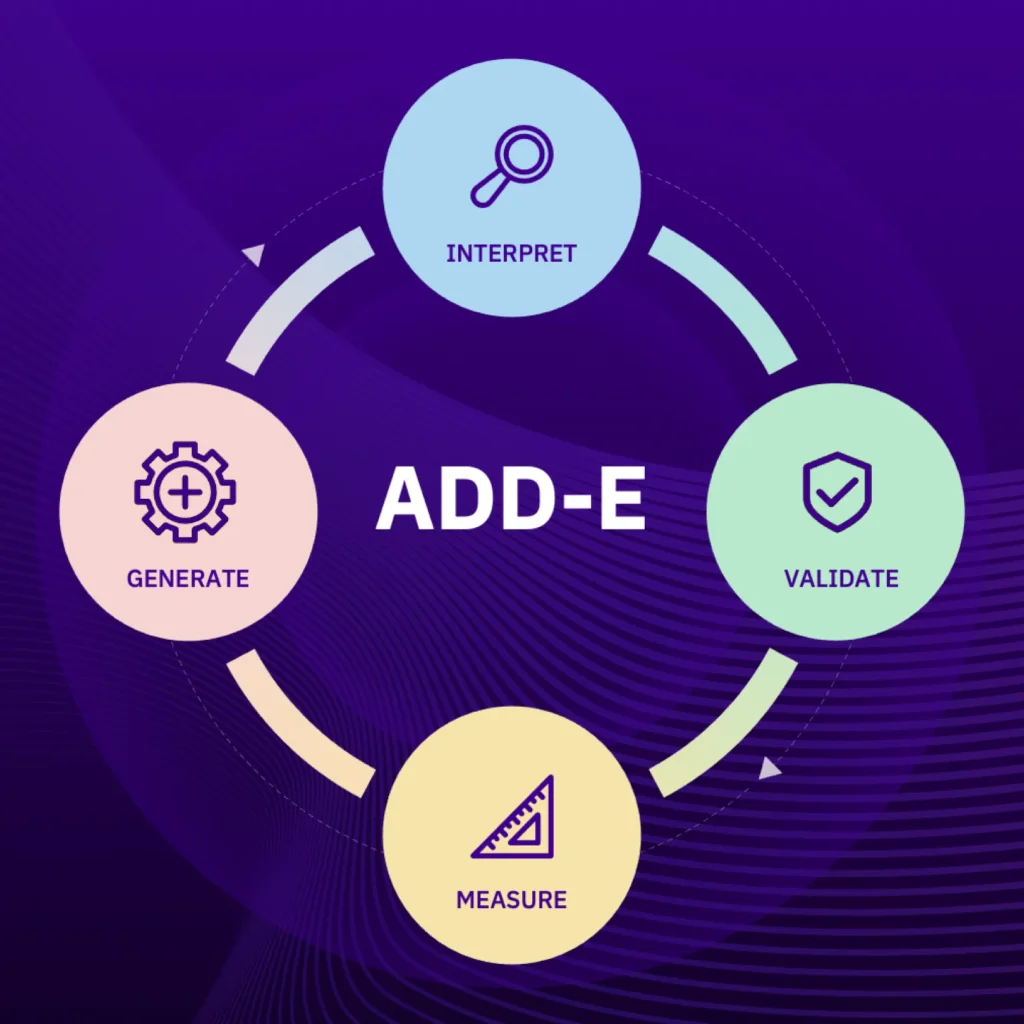
The ADD-E Framework
Four Pillars of Agent-Driven Detection Engineering
To combat this entropy, we’ve developed the ADD-E (Agent-Driven Detection Engineering) loop, a practical framework that leverages focused AI agents to unblock human-led detection engineering workflows. Rather than promising a fully automated “lights-out SOC,” ADD-E deploys precisely targeted automation to support human analysts at critical decision points.
The framework consists of four pillars that form a continuous cycle:
- Interpret – Understanding what rules do and why they exist
- Validate – Testing rules against realistic attack scenarios
- Measure – Evaluating rule efficacy and coverage
- Generate – Creating better rules from threat intelligence
At the heart of this framework sits a robust Detection Rule Manager – not an Excel spreadsheet, but a proper relational database model with many-to-many relationships and a CRUD API that allows agents to interact with it programmatically.
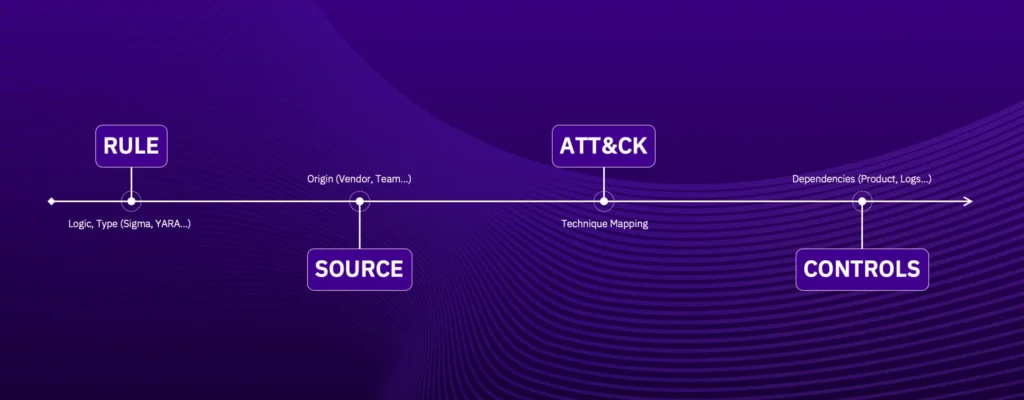
The Detection Rule Manager
A Home for Every Rule
For this approach to work, we need a structured home for every detection rule. Our model includes:
- Rules table: Stores each rule’s ID, type (Sigma, YARA, Snort, etc.), body, and creation metadata
- Sources table: Documents where rules came from (vendor, package, import date)
- Techniques table: Maps to MITRE ATT&CK tactics and techniques
- Controls table: Links to security products and log types
- Join tables: Create many-to-many relationships with confidence scoring
Everything is exposed via a CRUD API that agents can query and manipulate. This structured approach creates the foundation for our agent ecosystem.
Pillar 1:
Interpret – Clarity Through Explanation
The first challenge for any SOC is understanding what existing rules actually do. Many organizations have accumulated hundreds or thousands of detection rules from various sources – vendor packs, open-source repositories, internal development – with minimal documentation about their original purpose or current relevance.
According to the 2024 Ponemon Institute study on AI in Cybersecurity, SOCs receive an average of 22,111 security alerts per week, with an estimated 9,854 false positives generated by security tools in a typical week and an average of 12,009 unknown threats going undetected. Without proper context, analysts waste valuable time investigating benign activity or miss critical threats.
This is where our Rule Explainer Agents come in. These specialized agents can:
- Parse and interpret rules written in various languages (Sigma, YARA, Snort, SPL)
- Extract and explain the detection logic in plain English
- Surface the original author, creation date, and edit history
- Identify the MITRE ATT&CK techniques being targeted
- Flag assumptions hidden in the rule’s conditions

For example, when an analyst opens a complex Sigma rule looking for PowerShell download cradles, the Rule Explainer Agent can immediately provide a natural language explanation: “This rule detects attempts to download and execute code directly in memory using PowerShell’s Net.WebClient and DownloadString methods, a common technique (T1059.001) used in fileless malware attacks.”
By providing this context immediately, we reduce the time spent puzzling over rule logic and increase analyst confidence in taking action.
Pillar 2
Validate – Testing Against Reality
Rules that don’t detect anything are just pretty XML. But how do you know if your rules will fire under real-world attack conditions?
According to a study published in the Journal of Big Data, over 12,000 articles on cyber-attack detection methods were published in academic journals between 2020 and 2024 with researchers finding that machine learning and deep learning methods significantly improve detection capabilities. However, translating these approaches into practical, validated detection rules remains challenging.
The Pyramid of Pain framework, developed by David Bianco, provides a valuable lens for understanding the effectiveness of different detection approaches by illustrating the levels of difficulty an adversary would encounter to evade detection. The most effective detections target the “tough” layers of the pyramid – the tactics, techniques, and procedures (TTPs) that are hardest for attackers to change.
Our Validation Agents bridge the gap between theoretical detection approaches and practical implementation by:
- Atomic Scenario Matcher Agent: Finds existing attack simulation content that maps to the rule’s target TTP
- Attack Graph Matcher Agent: Identifies complex chains that could trigger the rule
- Assessment Planner Agent: Plans tests with the highest efficacy for validating the rule
These agents remove the manual labor of finding and configuring appropriate test scenarios, allowing engineers to rapidly validate whether their rules detect what they’re supposed to detect.
Pillar 3
Measure – Beyond True/False Positives
Detection engineering isn’t just about whether rules fire – it’s about whether they provide actionable intelligence that improves security outcomes.
According to Mandiant’s M-Trends 2024, the global median dwell time (how long attackers remain undetected) is 10 days, down from 16 in previous years. However, European organizations still average 22 days – more than three weeks during which attackers can explore, exfiltrate, and escalate.
Our Measurement Agents help teams understand which rules actually matter:
- Integration Agent: Records TP/FP/TN/FN feedback from analyst consoles
- Precision-Recall Calculator: Plots metrics over time to highlight rule drift
- Rule-to-ATT&CK Mapper Agent: Automatically maps detection capabilities to the MITRE ATT&CK framework and reveals coverage gaps
This approach moves beyond binary “good/bad” evaluations to a more nuanced understanding of detection efficacy. By visualizing coverage across the ATT&CK matrix, teams can quickly identify areas where they lack visibility – perhaps strong on persistence techniques but weak on credential access.
The key question changes from “Does this rule work?” to “Which rule buys me a day?” – meaning which detections most effectively reduce attacker dwell time and provide the highest return on the analyst’s attention investment.
Pillar 4
Generate – Intelligence-Driven Creation
The final pillar addresses the challenge of creating new, high-quality detection rules as threats evolve. A study by AllAboutAI found that the AI cybersecurity market was valued at $24.3 billion in 2023 and is projected to reach $134 billion by 2030 as organizations increasingly adopt AI tools to detect and counter threats.
Our Generation Agents transform this process by:
- CTI Decomposer Agent: Extracts IOCs, IOAs, TTPs, and attack flow information from threat intelligence
- Human Threat Analyst: Takes these elements and crafts relevant evidence at appropriate Pyramid of Pain levels
- Specialized Rule Builder Agents:
- YARA Builder for malicious binaries and scripts
- Snort/SURICATA Builder for suspicious PCAPs
- Sigma Builder for log patterns
This human-in-the-loop approach ensures that automated rule generation remains grounded in expert judgment while significantly accelerating the conversion of threat intelligence into detection capabilities.
Real-World Impact
Moving the Needle
Implementing ADD-E doesn’t automate away the SOC – rather, it amplifies human expertise by removing friction from the detection engineering lifecycle. According to the 2024 Study on the State of AI in Cybersecurity by the Ponemon Institute, 66% of respondents believe AI technologies increase security personnel productivity and 70% say AI is highly effective in detecting previously undetectable threats.
For SOC teams implementing these techniques:
- Faster Time-to-Detection: New threats are converted to validated detections within hours instead of days
- Reduced Alert Fatigue: Higher quality detections mean fewer false positives
- Better ATT&CK Coverage: Systematic approach identifies and fills critical gaps
- Enhanced Institutional Memory: Rule context preserved regardless of staff turnover

Most importantly, this approach creates a positive feedback loop. As detections improve, analysts spend less time on dead-end investigations and more time on high-value hunting and validation, further improving detection quality.
Conclusion
Running the Loop
The ADD-E framework represents a practical path out of the alert fatigue quagmire that plagues modern SOCs. By deploying focused agent assistance at key points in the detection lifecycle, teams can:
- Interpret the forgotten, making institutional knowledge accessible
- Validate against the real, ensuring rules actually detect threats
- Measure what matters, focusing effort where it has the most impact
- Generate the next defense, adapting faster than adversaries
This isn’t about replacing humans – it’s about removing the soul-crushing grunt work that leads to a turnover rate. According to a recent SANS report, it can take seven months to two years to fill a SOC role, creating a critical staffing shortage.
As Forrester analyst Allie Mellen observed, there are no “winners” in security – just data to learn from. ADD-E treats detection rules the same way: as data to continuously improve, not “set-and-forget” artifacts.
The next time you look at your alert queue, imagine seeing only what matters most – the high-fidelity signals that deserve your expertise—while your agent crew handles the rest. That’s the journey from stuck to started.
This blog post is based on a talk delivered at the EU MITRE ATT&CK Community Workshop 2025. For more information on implementing ADD-E in your organization, contact our team.